Wireless Questions
|
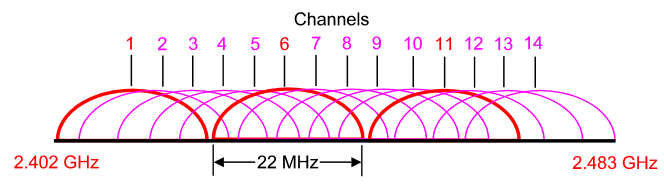
Quick Wireless Summary – Control and Provisioning for Wireless Access Point (CAPWAP) is an IETF standard for control messaging for setup, authentication and operations between APs and WLCs. CAPWAP is similar to LWAPP except the following differences: + CAPWAP uses Datagram Transport Layer Security (DTLS) for authentication and encryption to protect traffic between APs and controllers. LWAPP uses AES. An LAP operates in one of six different modes: Mobility Express is the ability to use an access point (AP) as a controller instead of a real WLAN controller. But this solution is only suitable for small to midsize, or multi-site branch locations where you might not want to invest in a dedicated WLC. A Mobility Express WLC can support up to 100 APs. The 2.4 GHz band is subdivided into multiple channels each allotted 22 MHz bandwidth and separated from the next channel by 5 MHz.
Antenna An antenna is a device to transmit and/or receive electromagnetic waves. Electromagnetic waves are often referred to as radio waves. Most antennas are resonant devices, which operate efficiently over a relatively narrow frequency band. An antenna must be tuned (matched) to the same frequency band as the radio system to which it is connected otherwise reception and/or transmission will be impaired. Types of external antennas:
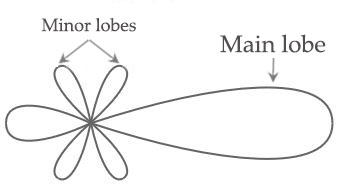
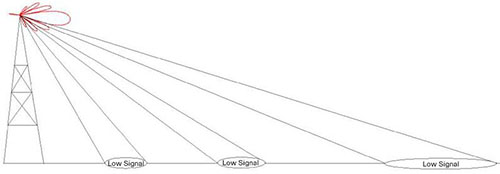
Omnidirectional Antenna Radiation Pattern + Directional: Focus the radio signal in a specific direction. Typically, these antennas have one main lobe and several minor lobes. Examples are the Yagi and parabolic dish
+ Multiple Input Multiple Output (MIMO) – Uses multiple antennas (up to eight) to increase bandwidth A real example of how the lobes affect the signal strength:
Common Antennas Commonly used antennas in a WLAN system are dipoles, omnidirectional antennas, patches and Yagis as shown below:
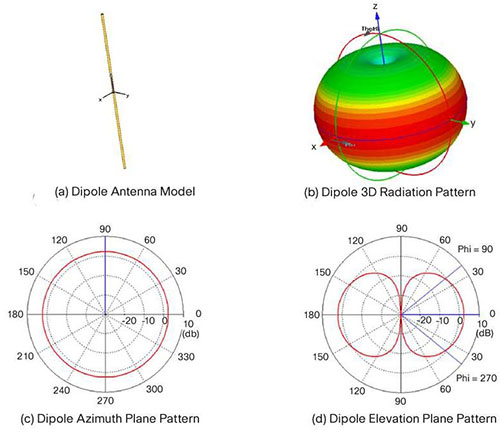
Antenna Radiation Patterns Dipole
A more comprehensive explanation of how we get the 2D patterns in (c) and (d) above is shown below:
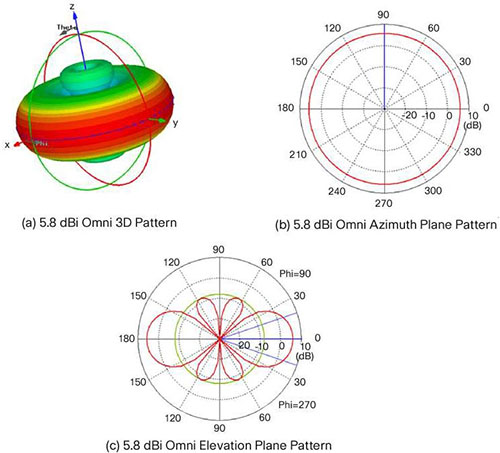
Omni
Patch
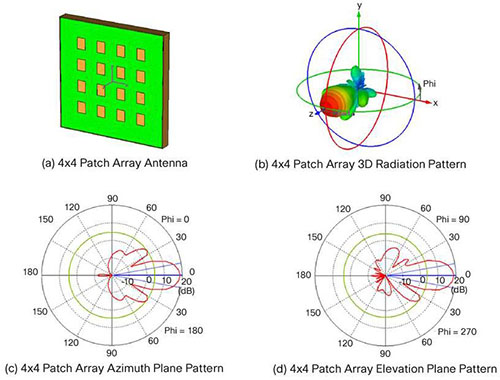
4 x 4 Patch
Wireless Terminologies Decibels Decibels (dB) are the accepted method of describing a gain or loss relationship in a communication system. If a level is stated in decibels, then it is comparing a current signal level to a previous level or preset standard level. The beauty of dB is they may be added and subtracted. A decibel relationship (for power) is calculated using the following formula:
“A” might be the power applied to the connector on an antenna, the input terminal of an amplifier or one end of a transmission line. “B” might be the power arriving at the opposite end of the transmission line, the amplifier output or the peak power in the main lobe of radiated energy from an antenna. If “A” is larger than “B”, the result will be a positive number or gain. If “A” is smaller than “B”, the result will be a negative number or loss. You will notice that the “B” is capitalized in dB. This is because it refers to the last name of Alexander Graham Bell. Note: + dBi is a measure of the increase in signal (gain) by your antenna compared to the hypothetical isotropic antenna (which uniformly distributes energy in all directions) -> It is a ratio. The greater the dBi value, the higher the gain and the more acute the angle of coverage. +To divide one number by another, simply subtract their equivalent decibel values. For example, to find 100 divided by 10: 100÷10 = log100 – log10= 20dB – 10dB = 10dB = 10 + dBm is a measure of signal power. It is the the power ratio in decibel (dB) of the measured power referenced to one milliwatt (mW). The “m” stands for “milliwatt”. Example: At 1700 MHz, 1/4 of the power applied to one end of a coax cable arrives at the other end. What is the cable loss in dB? Solution:
=> Loss = 10 * (- 0.602) = – 6.02 dB From the formula above we can calculate at 3 dB the power is reduced by half. Loss = 10 * log (1/2) = -3 dB; this is an important number to remember. Beamwidth The angle, in degrees, between the two half-power points (-3 dB) of an antenna beam, where more than 90% of the energy is radiated.
A radiation pattern defines the variation of the power radiated by an antenna as a function of the direction away from the antenna. Polarization describes the way the electric field of the radio wave is oriented. Antenna gain is the ability of the antenna to radiate more or less in any direction compared to a theoretical antenna.
Basic Service Set (BSS) A group of stations that share an access point are said to be part of one BSS. Extended Service Set (ESS) Some WLANs are large enough to require multiple access points. A group of access points connected to the same WLAN are known as an ESS. Within an ESS, a client can associate with any one of many access points that use the same Extended service set identifier (ESSID). That allows users to roam about an office without losing wireless connection. Roaming Roaming is the movement of a client from one AP to another while still transmitting. Roaming can be done across different mobility groups, but must remain inside the same mobility domain. The wireless client makes decisions on whether to change APs or remain connected to the current AP. There are 2 types of roaming: A client roaming from AP1 to AP2. These two APs are in the same mobility group and mobility domain
Roaming in the same Mobility Group A client roaming from AP1 to AP2. These two APs are in different mobility groups but in the same mobility domain
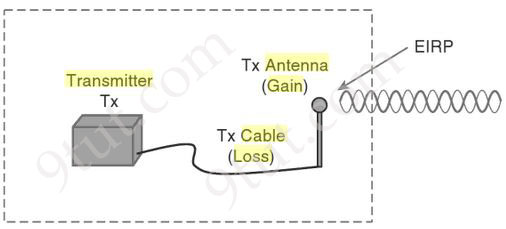
Roaming in different Mobility Groups (but still in the same Mobility Domain) Layer 2 & Layer 3 Intercontroller Roam When a mobile client roams from one AP to another, and if those APs are on different WLCs, then the client makes an intercontroller roam. When a client starts an intercontroller roam, the two WLCs compare the VLAN IDs allocated to their WLAN interfaces. Both of the roaming above allow the client to continue using its current IP address on the new AP and WLC. In a Layer 3 roaming, the original WLC is called the anchor controller, and the WLC where the roamed client is reassociated is called the foreign controller. The client is anchored to the original WLC even if it roams to different controllers. Wireless Parameters Noise There is radio frequency (RF) everywhere, from human activity, earth heat, space… The amount of unwanted RF is called noise. Effective Isotropic Radiated Power (EIRP) EIRP tells you what is the actual transmit power of the antenna. EIRP is a very important parameter because it is regulated by governmental agencies in most countries. In those cases, a system cannot radiate signals higher than a maximum allowable EIRP. To find the EIRP of a system, simply add the transmitter power level to the antenna gain and subtract the cable loss.
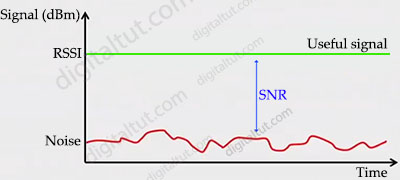
EIRP = Tx Power – Tx Cable + Tx Antenna Suppose a transmitter is configured for a power level of 10 dBm. A cable with 5-dB loss connects the transmitter to an antenna with an 8-dBi gain. The resulting EIRP of the system is EIRP = 10 dBm – 5 dB + 8 dBi = 13 dBm. You might notice that the EIRP is made up of decibel-milliwatt (dBm), dB relative to an isotropic antenna (dBi), and decibel (dB) values. Even though the units appear to be different, you can safely combine them because they are all in the dB “domain”. Receive Signal Strength Indicator (RSSI) RSSI is a measurement of how well your device can hear a signal from an access point or router (useful signal). It’s a value that is useful for determining if you have enough signal to get a good wireless connection. Signal-to-noise ratio (SNR or S/N) SNR is the ratio of received signal power (at wireless client) to the noise power, and its unit of expression is typically decibels (dB). If your signal power and noise power are already in decibel form, then you can subtract the noise power from the signal power: SNR = S – N. This is because when you subtract logarithms, it is the equivalent of dividing normal numbers. Also, the difference in the numbers equals the SNR.For example, if the noise floor is -80 dBm and the wireless client is receiving a signal of -65 dBm SNR = -65 – (-80) = 15.
Or we can find SNR from RSSI with this formula: SNR = RSSI – N, with N is the noise power. A practical example to calculate SNR Here is an example to tie together this information to come up with a very simple RF plan calculator for a single AP and a single client. Based on the above, we can calculate the following information: WPA2 and WPA3 WPA2 is classified into two versions to encrypt Wi-Fi networks: Similar to WPA2, WPA3 includes: WPA3 provides improvements to the general Wi-Fi encryption, thanks to Simultaneous Authentication of Equals (SAE) replacing the Pre-Shared Key (PSK) authentication method used in prior WPA versions. SAE enables individuals or home users to set Wi-Fi passwords that are easier to remember and provide the same security protection even if the passwords are not complex enough. WPA3 requires the use of Protected Management Frames. These frames help protect against forging and eavesdropping. Wifi 6 (802.11ax) Wifi 6 is an IEEE standard for wireless local-area networks (WLANs) and the successor of 802.11ac. Wi-Fi 6 brings several crucial wireless enhancements for IT administrators when compared to Wi-Fi 5. The first significant change is using 2.4 GHz. Wi-Fi 5 was limited to only using 5 GHz. While 5 GHz is a ‘cleaner’ band of RF, it doesn’t penetrate walls and 2.4 GHz and requires more battery life. For Wi-Fi driven IoT devices, 2.4 GHz will likely continue to be the band of choice for the foreseeable future. Another critical difference between the two standards is the use of Orthogonal Frequency Division Multiple Access (OFDMA) and MU-MIMO. Wi-Fi 5 was limited to downlink only on MU-MIMO, where Wi-Fi 6 includes downlink and uplink. OFDMA, as referenced above, is also only available in Wi-Fi 6. |
Question 1
Explanation
The Lightweight AP (LAP) can discover controllers through your domain name server (DNS). For the access point (AP) to do so, you must configure your DNS to return controller IP addresses in response to CISCO-LWAPP-CONTROLLER.localdomain, where localdomain is the AP domain name. When an AP receives an IP address and DNS information from a DHCP server, it contacts the DNS to resolve CISCO-CAPWAP-CONTROLLER.localdomain. When the DNS sends a list of controller IP addresses, the AP sends discovery requests to the controllers.
The AP will attempt to resolve the DNS name CISCO-CAPWAP-CONTROLLER.localdomain. When the AP is able to resolve this name to one or more IP addresses, the AP sends a unicast CAPWAP Discovery Message to the resolved IP address(es). Each WLC that receives the CAPWAP Discovery Request Message replies with a unicast CAPWAP Discovery Response to the AP.
Question 2
Explanation
Signal to Noise Ratio (SNR) is defined as the ratio of the transmitted power from the AP to the ambient (noise floor) energy present. To calculate the SNR value, we add the Signal Value to the Noise Value to get the SNR ratio. A positive value of the SNR ratio is always better.
Here is an example to tie together this information to come up with a very simple RF plan calculator for a single AP and a single client.
+ Access Point Power = 20 dBm
+ 50 foot antenna cable = – 3.35 dB Loss
+ Signal attenuation due to glass wall with metal frame = -6 dB
+ External Access Point Antenna = + 5.5 dBi gain
+ RSSI at WLAN Client = -75 dBm at 100ft from the AP
+ Noise level detected by WLAN Client = -85 dBm at 100ft from the AP
Based on the above, we can calculate the following information.
+ EIRP of the AP at source = 20 – 3.35 + 5.5 = 22.15 dBm
+ Transmit power as signal passes through glass wall = 22.15 – 6 = 16.15 dBm
+ SNR at Client = -75 + -85 = 10 dBm (difference between Signal and Noise)
Receive Signal Strength Indicator (RSSI) is a measurement of how well your device can hear a signal from an access point or router. It’s a value that is useful for determining if you have enough signal to get a good wireless connection.
EIRP tells you what’s the actual transmit power of the antenna in milliwatts.
dBm is an abbreviation for “decibels relative to one milliwatt,” where one milliwatt (1 mW) equals 1/1000 of a watt. It follows the same scale as dB. Therefore 0 dBm = 1 mW, 30 dBm = 1 W, and -20 dBm = 0.01 mW
Question 3
Explanation
The EAP-FAST protocol is a publicly accessible IEEE 802.1X EAP type that Cisco developed to support customers that cannot enforce a strong password policy and want to deploy an 802.1X EAP type that does not require digital certificates.
EAP-FAST is also designed for simplicity of deployment since it does not require a certificate on the wireless LAN client or on the RADIUS infrastructure yet incorporates a built-in provisioning mechanism.
Question 4
Explanation
If the clients roam between APs registered to different controllers and the client WLAN on the two controllers is on different subnet, then it is called inter-controller L3 roam.
In this situation as well controllers exchange mobility messages. Client database entry change is completely different that to L2 roam(instead of move, it will copy). In this situation the original controller marks the client entry as “Anchor” where as new controller marks the client entry as “Foreign“.The two controllers now referred to as “Anchor controller” & “Foreign Controller” respectively. Client will keep the original IP address & that is the real advantage.
Note: Inter-Controller (normally layer 2) roaming occurs when a client roam between two APs registered to two different controllers, where each controller has an interface in the client subnet.
Question 5
Question 6
Explanation
According to the Meraki webpage, radar and rogue AP are two sources of Wireless Interference.
Interference between different WLANs occurs when the access points within range of each other are set to the same RF channel.
Note: Microwave ovens (not conventional oven) emit damaging interfering signals at up to 25 feet or so from an operating oven. Some microwave ovens emit radio signals that occupy only a third of the 2.4-GHz band, whereas others occupy the entire band.
Reference: https://www.ciscopress.com/articles/article.asp?p=2351131&seqNum=2
So answer D is not a correct answer.
Question 7
Explanation
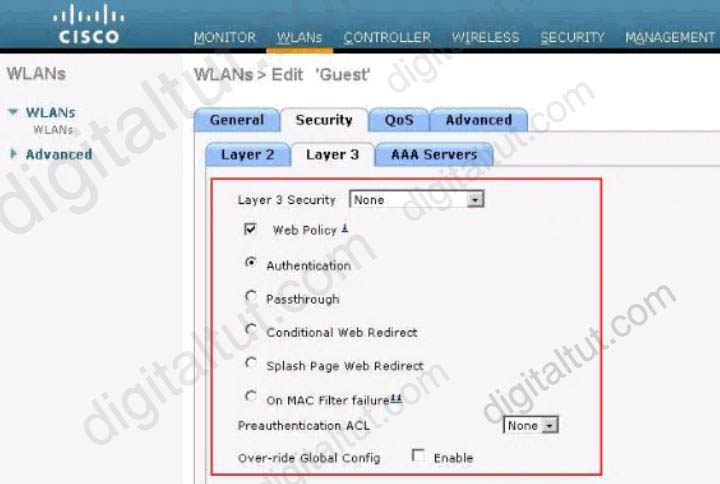
This paragraph was taken from the link https://www.cisco.com/c/en/us/support/docs/wireless-mobility/wlan-security/69340-web-auth-config.html#c5:
“The next step is to configure the WLC for the Internal web authentication. Internal web authentication is the default web authentication type on WLCs.”
In step 4 of the link above, we will configure Security as described in this question. Therefore we can deduce this configuration is for Internal web authentication.
Question 8
Explanation
FlexConnect is a wireless solution for branch office and remote office deployments. It enables customers to configure and control access points in a branch or remote office from the corporate office through a wide area network (WAN) link without deploying a controller in each office.
The FlexConnect access points can switch client data traffic locally and perform client authentication locally when their connection to the controller is lost. When they are connected to the controller, they can also send traffic back to the controller. In the connected mode, the FlexConnect access point can also perform local authentication.
Question 9
Explanation
Deploying WPA2-Enterprise requires a RADIUS server, which handles the task of authenticating network users access. The actual authentication process is based on the 802.1X policy and comes in several different systems labelled EAP. Because each device is authenticated before it connects, a personal, encrypted tunnel is effectively created between the device and the network.
Reference: https://www.securew2.com/solutions/wpa2-enterprise-and-802-1x-simplified/
Question 10
Explanation
802.11r Fast Transition (FT) Roaming is an amendment to the 802.11 IEEE standards. It is a new concept for roaming. The initial handshake with the new AP occurs before client roams to the target AP. Therefor it is called Fast Transition. 802.11r provides two methods of roaming:
+ Over-the-air: With this type of roaming, the client communicates directly with the target AP using IEEE 802.11 authentication with the Fast Transition (FT) authentication algorithm.
+ Over-the-DS (distribution system): With this type of roaming, the client communicates with the target AP through the current AP. The communication between the client and the target AP is carried in FT action frames between the client and the current AP and is then sent through the controller.
But both of these methods do not deal with legacy clients.
The 802.11k allows 11k capable clients to request a neighbor report containing information about known neighbor APs that are candidates for roaming.
Reference: https://www.cisco.com/c/en/us/td/docs/wireless/controller/technotes/80211r-ft/b-80211r-dg.html
IEEE 802.11v is an amendment to the IEEE 802.11 standard which describes numerous enhancements to wireless network management. One such enhancement is Network assisted Power Savings which helps clients to improve the battery life by enabling them to sleep longer. Another enhancement is Network assisted Roaming which enables the WLAN to send requests to associated clients, advising the clients as to better APs to associate to. This is useful for both load balancing and in directing poorly connected clients.
Cisco 802.11r supports three modes:
+ Pure mode: only allows 802.11r client to connect
+ Mixed mode: allows both clients that do and do not support FT to connect
+ Adaptive mode: does not advertise the FT AKM at all, but will use FT when supported clients connect
Therefore “Adaptive mode” is the best answer here.
Question 11
Explanation
Link aggregation (LAG) is a partial implementation of the 802.3ad port aggregation standard. It bundles all of the controller’s distribution system ports into a single 802.3ad port channel.
Restriction for Link aggregation:
+ LAG requires the EtherChannel to be configured for ‘mode on’ on both the controller and the Catalyst switch.
…
Question 12
Question 13
Explanation
Mobility Express is the ability to use an access point (AP) as a controller instead of a real WLAN controller. But this solution is only suitable for small to midsize, or multi-site branch locations where you might not want to invest in a dedicated WLC. A Mobility Express WLC can support up to 100 APs. Mobility Express WLC also uses CAPWAP to communicate to other APs.
Note: Local mode is the most common mode that an AP operates in. This is also the default mode. In local mode, the LAP maintains a CAPWAP (or LWAPP) tunnel to its associated controller.
Question 14
Explanation
A Cisco lightweight wireless AP needs to be paired with a WLC to function.
An AP must be very diligent to discover any controllers that it can join—all without any preconfiguration on your part. To accomplish this feat, several methods of discovery are used. The goal of discovery is just to build a list of live candidate controllers that are available, using the following methods:
+ Prior knowledge of WLCs
+ DHCP and DNS information to suggest some controllers (DHCP Option 43)
+ Broadcast on the local subnet to solicit controllers
Reference: CCNP and CCIE Enterprise Core ENCOR 350-401 Official Cert Guide
If you do not tell the LAP where the controller is via DHCP option 43, DNS resolution of “Cisco-capwap-controller.local_domain”, or statically configure it, the LAP does not know where in the network to find the management interface of the controller.
In addition to these methods, the LAP does automatically look on the local subnet for controllers with a 255.255.255.255 local broadcast.
Question 15
Explanation
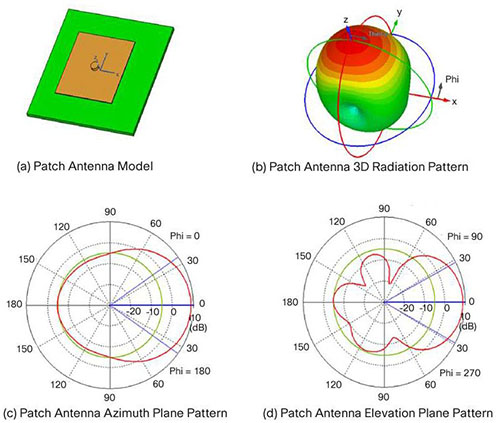
A patch antenna, in its simplest form, is just a single rectangular (or circular) conductive plate that is spaced above a ground plane. Patch antennas are attractive due to their low profile and ease of fabrication.
The azimuth and elevation plane patterns are derived by simply slicing through the 3D radiation pattern. In this case, the azimuth plane pattern is obtained by slicing through the x-z plane, and the elevation plane pattern is formed by slicing through the y-z plane. Note that there is one main lobe that is radiated out from the front of the antenna. There are three back lobes in the elevation plane (in this case), the strongest of which happens to be 180 degrees behind the peak of the main lobe, establishing the front-to-back ratio at about 14 dB. That is, the gain of the antenna 180 degrees behind the peak is 14 dB lower than the peak gain.
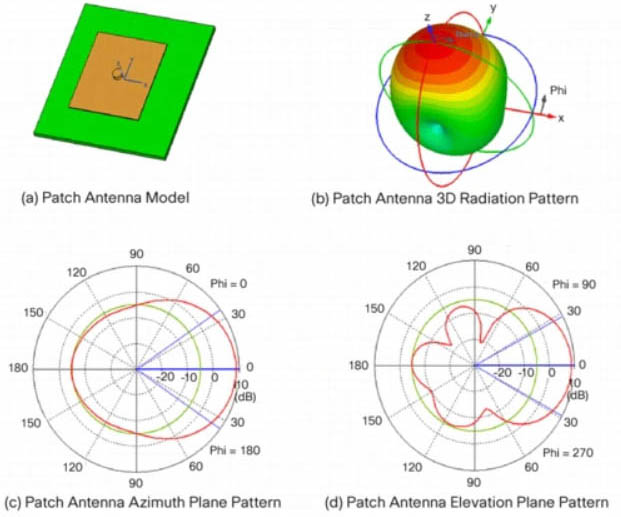
Again, it doesn’t matter if these patterns are shown pointing up, down, to the left or to the right. That is usually an artifact of the measurement system. A patch antenna radiates its energy out from the front of the antenna. That will establish the true direction of the patterns.


 Yagi
Yagi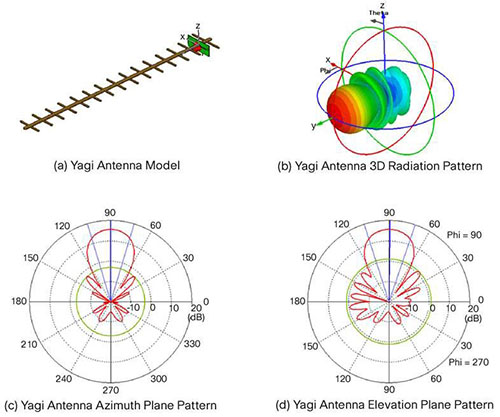





Question 6
What are two common sources of interference for WI-FI networks? (Choose two)
A. radar
B. LED lights
C. rogue AP
D. conventional oven
E. fire alarm
Answer: C D
Conventional ovens don’t emit signals and thus do not interfere with wireless signals. Microwave ovens do, conventional dont. Radars on the other hand do emit signals.
Answer should be A,D imo. Can someone confirm? Thanks
Sorry: answer is A,C.
@Wireless
from the Meraki documentation : https://documentation.meraki.com/MR/WiFi_Basics_and_Best_Practices/Common_Sources_of_Wireless_Interference
Radars and Fluorescent lights are mentioned (which are led lights if I’m not mistaken) and from Juniper documentation rogue APs cause interference.
So which 2 answers are correct???
The answer is A and C
Meraki documentation says: “fluorescent lights” not LED lights. They’re different. Fluorescent lights have thermionic emission that occurs in the lamp portion. This occurs as an arc passes through the mercury vapor present in the lamp. One side effect of this is the production of radio waves up to a few megahertz in frequency. Fluorescent bulbs contain inert gas within the glass casing while LEDs are a solid state technology.
@Digitaltut as per aussie you already confirmed this that the below is the answer. please check the answers its very confusing now. and please update it.
Which two descriptions of FlexConnect mode for Cisco APs are true? (Choose two)
A. APs that operate in FlexConnect mode cannot detect rogue APs
B. FlexConnect mode is used when the APs are set up in a mesh environment and used to bridge between each other
C. FlexConnect mode is a feature that is designed to allow specified CAPWAP-enabled APs to exclude themselves from managing data traffic between clients and infrastructure
D. When connected to the controller, FlexConnect APs can tunnel traffic back to the controller
E. FlexConnect mode is a wireless solution for branch office and remote office deployments
Answer BE
https://www.cisco.com/c/en/us/td/docs/wireless/controller/7-2/configuration/guide/cg/cg_flexconnect.html
For FlexConnect access points, the interface mapping at the controller for WLANs that is configured for FlexConnect local switching is inherited
at the access point as the default VLAN tagging. This mapping can be changed per SSID and per FlexConnect access point. Non-FlexConnect access points tunnel
all traffic back to the controller, and VLAN tagging is determined by each WLAN’s interface mapping.
Jlai B can’t be a right answer, for mesh environments, access points use bridge mode
Answers are D and E
D. When connected to the controller, FlexConnect APs can tunnel traffic back to the controller
This is true, even having the access point in flex connect, if in the wlan you don’t have the local switching configured, they will send the data traffic back to the controller.
Q4
Refer to the exhibit.
The WLC administrator sees that the controller to which a roaming client associates has Mobility Role Anchor configured under Clients > Detail.
Which type of roaming is supported?
Is the right answer Layer 3 intercontroller or Layer 2 intercontroller? And why is that right?
You are configuring a controller that runs Cisco IOS XE by using the CLI. Which three configuration
options are used for 802.11w Protected Management Frames? (Choose three.)
A. mandatory
B. association-comeback
C. SA teardown protection
D. saquery-retry-time
E. enable
F. comeback-time
Refer to the exhibit. An engineer is designing a guest portal on Cisco ISE using the default configuration.
During the testing phase, the engineer receives a warning when displaying the guest portal.(YOUR CONNECTION IS NOT PRIVATE WARNING ) Which issue is
occurring?
A. The server that is providing the portal has an expired certificate
B. The server that is providing the portal has a self-signed certificate
C. The connection is using an unsupported protocol
D. The connection is using an unsupported browser
Refer to the exhibit. Which level message does the WLC send to the syslog server?
A. syslog level errors and less severity messages
B. syslog level errors messages
C. all syslog levels messages
D. syslog level errors and greater severity messages
SYSLOG LEVEL : ERRORS
Refer to the exhibit.
A wireless client is connecting to FlexAP1 which is currently working standalone mode. The AAA
authentication process is returning the following AVPs:
Tunnel-Private-Group-Id(81): 15
Tunnel-Medium-Type(65): IEEE-802(6)
Tunnel-Type(64): VLAN(13)
Which three behaviors will the client experience? (Choose three.)
A. While the AP is in standalone mode, the client will be placed in VLAN 15.
B. While the AP is in standalone mode, the client will be placed in VLAN 10.
C. When the AP transitions to connected mode, the client will be de-authenticated.
D. While the AP is in standalone mode, the client will be placed in VLAN 13.
E. When the AP is in connected mode, the client will be placed in VLAN 13.
F. When the AP transitions to connected mode, the client will remain associated.
G. When the AP is in connected mode, the client will be placed in VLAN 15.
H. When the AP is in connected mode, the client will be placed in VLAN 10.
@Rocket What kind of questions are these? Are the questions valid?
@CHRIS 7890 yes , they are new . But i got only 10 new questions beside the legacy question already attached here. But the questions are only a bonus. I`m studying from January , read the book , did the official labs , saw INE videos , whatced ITproTV videos , read some Design guides for SD-wan and SD-ACCESS. And i have deployed WLC`s in my network so i hope that i will manage to pass.
@Rocket What does bonus mean, bonus which you have posted for you or bonus to ask which are available in the certificate
Bonus means that the knowledge after you study is yours and the certification is their’s.
@Rocket so you can say there are no valid 350-401 questions? But for our study it nice to have?
Something like that. I have my exam in the near future. I will how it goes.
Rocket
was anwer D. syslog level errors and greater severity messages ?
Chapter: 802.11w Protected Management Frames
CLI Configuration for Protected Management Frames
security pmf [ association-comeback
association-comeback-time-in-seconds | mandatory | optional |
saquery saquery-time-interval-milliseconds ]
Rocket
was answer A,B D ?
https://www.cisco.com/c/en/us/td/docs/wireless/controller/technotes/5700/software/release/ios_xe_33/11rkw_DeploymentGuide/b_802point11rkw_deployment_guide_cisco_ios_xe_release33/b_802point11rkw_deployment_guide_cisco_ios_xe_release33_chapter_0100.html
Rocket regarding :
A wireless client is connecting to FlexAP1 which is currently working standalone mode. The AAA
authentication process is returning the following AVPs:
Tunnel-Private-Group-Id(81): 15
Tunnel-Medium-Type(65): IEEE-802(6)
Tunnel-Type(64): VLAN(13)
Which three behaviors will the client experience? (Choose three.)
A. While the AP is in standalone mode, the client will be placed in VLAN 15.
B. While the AP is in standalone mode, the client will be placed in VLAN 10.
C. When the AP transitions to connected mode, the client will be de-authenticated.
D. While the AP is in standalone mode, the client will be placed in VLAN 13.
E. When the AP is in connected mode, the client will be placed in VLAN 13.
F. When the AP transitions to connected mode, the client will remain associated.
G. When the AP is in connected mode, the client will be placed in VLAN 15.
H. When the AP is in connected mode, the client will be placed in VLAN 10.
the answer is ADE
Which two pieces of information are necessary to compute SNR? (Choose two)
A. EIRP
B. noise floor
C. antenna gain
D. RSSI
E. transmit power
Answer: B D
Answer should be B,E. What do you think?
@DMX the Answer is RSSI and noise floor.
to calculate SNR , the Signal and noise power values should be required not the transmitting power. Transmitting power and antenna gain do affect it but it seems here that Cisco looks for the Answer of : B , D
Refer to the exhibit. Which level message does the WLC send to the syslog server?
A. syslog level errors and less severity messages
B. syslog level errors messages
C. all syslog levels messages
D. syslog level errors and greater severity messages
SYSLOG LEVEL : ERRORS
Answer A:
Explanations:
If you set a syslog level, only those messages whose severity is equal to or less than that level are sent to the syslog servers. For example, if you set the syslog level to Errors (severity level 3), only those messages whose severity is between 0 and 3 are sent to the syslog servers.
https://www.cisco.com/c/en/us/td/docs/wireless/controller/8-0/configuration-guide/b_cg80/b_cg80_chapter_0110100.html
1) Tunnel-Private-Group-Id(81): 15 -> this is the Vlan you got from radius
https://tools.ietf.org/html/rfc2868
Type 81 for Tunnel-Private-Group-ID
2)Tunnel-Medium-Type(65): IEEE-802(6) -> this is nothing except telling it’s 802.1Q
https://www.iana.org/assignments/radius-types/radius-types.xhtml#radius-types-15
6 802 (includes all 802 media plus Ethernet “canonical format”) [RFC2868]
3) Tunnel-Type(64): VLAN(13) -> this is nothing except telling it’s a vlan
https://www.iana.org/assignments/radius-types/radius-types.xhtml#radius-types-14
Values for RADIUS Attribute 64, Tunnel-Type
13 Virtual LANs (VLAN) [RFC3580]
So we have only 1 vlan, the 15
SO, A & G minimum
+ in local mode, when transitioning, it should remain connected.
Final answer : AFG
@Rocket @hja031 @Voyager
Answer is BCG
Please see below:
Traffic flow on WLANs configured for Local Switching when Flex APs are in Connected Mode:
■If the VLAN is returned as one of the AAA attributes and that VLAN is not present in the Flex AP database, traffic will switch centrally and the client will be assigned this VLAN/Interface returned from the AAA server provided that the VLAN exists on the WLC.
■If the VLAN is returned as one of the AAA attributes and that VLAN is not present in the Flex AP database, traffic will switch centrally. If that VLAN is also not present on the WLC, the client will be assigned a VLAN/Interface mapped to a WLAN on the WLC.
■If the VLAN is returned as one of the AAA attributes and that VLAN is present in the FlexConnect AP database, traffic will switch locally.
■If the VLAN is not returned from the AAA server, the client will be assigned a WLAN mapped VLAN on that FlexConnect AP and traffic will switch locally.
Traffic flow on WLANs configured for Local Switching when Flex APs are in Standalone Mode:
■If the VLAN returned by an AAA server is not present in the Flex AP database, the client will be put to default VLAN (that is, a WLAN mapped VLAN on Flex AP). When the AP connects back, this client will be de-authenticated and will switch traffic centrally.
■If the VLAN returned by an AAA server is present in the Flex AP database, the client will be put into a returned VLAN and traffic will switch locally.
■If the VLAN is not returned from an AAA server, the client will be assigned a WLAN mapped VLAN on that FlexConnect AP and traffic will switch locally.
What is used to measure the total output energy of a Wi-Fi device?
A. dBi
B. EIRP
C. mW
D. dBm
Hi @Jo, the answer is C
After a redundant route processor failure occurs on a Layer 3 device, which mechanism allows for packets to be forwarded from a neighboring router based on the most recent tables?
A. RPVST+
B. RP failover
C. BFD
D. NSF
Answer: D
Which unit measures the power of a radio signal with reference to 1 milliwatt?
A. dBw
B. dBi
C. mW
D. dBm
Answer: D
Explanation
dBm is an abbreviation for “decibels relative to one milliwatt,” where one milliwatt (1 mW) equals 1/1000 of a watt. It follows the same scale as dB. Therefore 0 dBm = 1 mW, 30 dBm = 1 W, and -20 dBm = 0.01 mW
What is a characteristic of MACsec?
A. 802.1AE provides encryption and authentication services
B. 802.1AE is built between the host and switch using the MKA protocol, which negotiates encryption keys based on the master session key from a successful 802.1X session
C. 802.1AE is built between the host and switch using the MKA protocol using keys generated via the Diffie-Hellman algorithm (anonymous encryption mode)
D. 802.1AE is negotiated using Cisco AnyConnect NAM and the SAP protocol
Answer: A
Explanation
MACsec, defined in 802.1AE, provides MAC-layer encryption over wired networks by using out-of-band methods for encryption keying. The MACsec Key Agreement (MKA) Protocol provides the required session keys and manages the required encryption keys. MKA and MACsec are implemented after successful authentication using the 802.1x Extensible Authentication Protocol (EAP-TLS) or Pre Shared Key (PSK) framework.
Reference: https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9300/software/release/16-9/configuration_guide/sec/b_169_sec_9300_cg/macsec_encryption.html
-> MACsec only provides encryption, not authentication -> Answer A is not correct.
Successful IEEE 802.1X authentication is the first step in establishing a MACsec session. IEEE 802.1X provides primary key material to the supplicant and switch that will subsequently be used by MACsec -> Answer B is correct.
If an MKA cryptographic algorithm is not configured, a default cryptographic algorithm of AES-CMAC-128 (Cipher-based Message Authentication Code with 128-bit Advanced Encryption Standard) is used -> Answer C is not correct.
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/macsec/configuration/xe-16/macsec-xe-16-book/wan-macsec-mka-support-enhance.html
802.1AE is negotiated using MKA Protocol so answer D is not correct
Help with this question please:
Which 2 methods are used to reduce the AP coverage area? (choose 2)
A. Reduce the transmit power
B. Increase minimum mandatory data rate
C. Reduce channel width from 40 Mhz to 20 Mhz
D. Enable Fastlane
E. Disable 2.4 Ghz and use only 5Ghz
Answers: A B
Are the answers correct? I could swear “E” was a correct answer.
@digitaltut what is the updated answer to this question? I answered A and D but it showed A to be wrong.
An engineer measures the Wi-Fi coverage at a customer site. The RSSI values are recorded as follows:
Location A: -72 dBm
Location B: -75 dBm
Location C: -85 dBm
Location D: -80 dBm
Which two statements does the engineer use to explain these values to the customer? (Choose two)
A. The signal strength at location B is 10 dB better than location
B. Location D has the strongest RF signal strength
C. The RF signal strength at location B is 50% weaker than location
D. The RF signal strength at location C is 10 times stronger than location
E. The signal strength at location C is too weak to support web surfing
An engineer measures the Wi-Fi coverage at a customer site. The RSSI values are recorded as follows:
Location A: -72 dBm
Location B: -75 dBm
Location C: -65 dBm
Location D: -80 dBm
Which two statements does the engineer use to explain these values to the customer? (Choose two)
Which two statements does the engineer use to explain these values to the customer? (Choose two)
A. The signal strength at location B is 10 dB better than location C
B. Location D has the strongest RF signal strength
C. The RF signal strength at location B is 50% weaker than location A
D. The RF signal strength at location C is 10 times stronger than location B
E. The signal strength at location C is too weak to support web surfing
To me, the right answers should be A and C due to the rule of 3s and 10s.
Can someone confirm? Thanks
@Martin I believe so that it should be A and E
anyone has any idea why here is the answer C i would say it should be A as 3dB increase will double the power.
If the maximum power level assignment for global TPC 802.11a/n/ac is configured to 10dBm, which power level effectively doubles the transmit power?
A: 13dBm
B: 14dBm
C: 17dBm
D: 20dBm
An engineer measures the Wi-Fi coverage at a customer site. The RSSI values are recorded as follows:
Location A: -72 dBm
Location B: -75 dBm
Location C: -65 dBm
Location D: -80 dBm
Which two statements does the engineer use to explain these values to the customer? (Choose two)
Which two statements does the engineer use to explain these values to the customer? (Choose two)
A. The signal strength at location B is 10 dB better than location C
B. Location D has the strongest RF signal strength
C. The RF signal strength at location B is 50% weaker than location A
D. The RF signal strength at location C is 10 times stronger than location B
E. The signal strength at location C is too weak to support web surfing
To me, the right answers should be A and C due to the rule of 3s and 10s.
Can someone confirm? Thanks
Answers: C and D
whit “-” if absolute value is higher the true value is lower. ( -72 > -75; -72 – (-75) = -72 + 75 = 3dBm) Whit 3dB difference location B is 50% weaker than location A and C is correct.
-65 dBm is for 10 dBm higher than -75 dBm. 10 dBm is 10 times stronger. And D is correct.
An engineer measures the Wi-Fi coverage at a customer site. The RSSI values are recorded as follows:
Location A: -72 dBm
Location B: -75 dBm
Location C: -65 dBm
Location D: -80 dBm
Which two statements does the engineer use to explain these values to the customer? (Choose two)
Which two statements does the engineer use to explain these values to the customer? (Choose two)
A. The signal strength at location B is 10 dB better than location C
B. Location D has the strongest RF signal strength
C. The RF signal strength at location B is 50% weaker than location A
D. The RF signal strength at location C is 10 times stronger than location B
E. The signal strength at location C is too weak to support web surfing
Correct answer would be C and D
Difference between A and B is 3dB so A/B = 0.5 or 50%
Difference between B and C is 10dB so C/B = 10 (10 times)
if you are not certain of the answer stop confusing people with wrong answer.
Which type of tunnel is required between two WLCs to enable intercontroller roaming?
A. LWAPP
B. CAPWAP
C. mobility
D. iPsec
Shouldn’t correct answer be CAPWAP? There are mobility messages but there is no mobility tunnel. In OCG 551 page it is shown on picture that is CAPWAP!
Pass4 surexams.com exam dumps helped me achieve a score of 92%.
Guys dont make mess please.
Question 8 :
Answer is D and E :
https://www.cisco.com/c/en/us/td/docs/wireless/controller/8-5/config-guide/b_cg85/flexconnect.html
From the above link in the first paragraph you have the answer
FlexConnect is a wireless solution for branch office and remote office deployments.
When they are connected to the controller, they can also send traffic back to the controller.