Use Distribute-list to filter Routing Updates in BGP
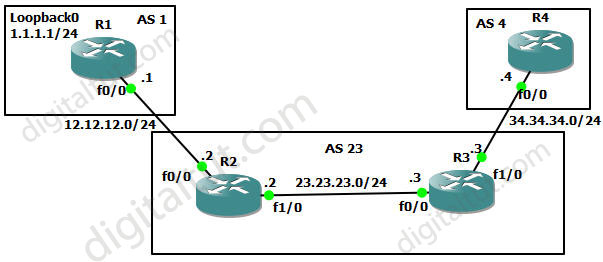
In this lab we will learn how to use distribute-list to filter unwanted routes in BGP. Below is the topology of this lab:
IOS used in this lab: c3640-jk9s-mz.124-16.bin
Objectives of this lab:
+ Task 1: Configure EBGP on AS 1, AS 23, AS 4 and configure IBGP between R2 & R3 (AS23), also advertise loopback 0 interface on R1 so that all the routers learn about this network.
+ Task 2: Use a distribute-list to filter out network 1.1.1.0
Let’s start our lab!
Task 1 has been mentioned in detail in BGP next-hop-self, community no-export & send-community Lab so I just post the configuration here:
Configure IP addresses on all interfaces
| R1(config)#interface f0/0 R1(config-if)#ip address 12.12.12.1 255.255.255.0 R1(config-if)#no shutdown |
R3(config)#interface f0/0 R3(config-if)#ip address 23.23.23.3 255.255.255.0 R3(config-if)#no shutdown R3(config)#interface f1/0 R3(config-if)#ip address 34.34.34.3 255.255.255.0 R3(config-if)#no shutdown |
| R2(config)#interface f0/0 R2(config-if)#ip address 12.12.12.2 255.255.255.0 R2(config-if)#no shutdown R2(config)#interface f1/0 R2(config-if)#ip address 23.23.23.2 255.255.255.0 R2(config-if)#no shutdown |
R4(config)#interface f0/0 R4(config-if)#ip address 34.34.34.4 255.255.255.0 R4(config-if)#no shutdown |
Configure EBGP & IBGP
| R1(config)#router bgp 1 R1(config-router)#neighbor 12.12.12.2 remote-as 23 |
R3(config)#router bgp 23 R3(config-router)#neighbor 23.23.23.2 remote-as 23 R3(config-router)#neighbor 34.34.34.4 remote-as 4 R3(config-router)#neighbor 23.23.23.2 next-hop-self |
| R2(config)#router bgp 23 R2(config-router)#neighbor 12.12.12.1 remote-as 1 R2(config-router)#neighbor 23.23.23.3 remote-as 23 R2(config-router)#neighbor 23.23.23.3 next-hop-self |
R4(config)#router bgp 4 R4(config-router)#neighbor 34.34.34.3 remote-as 23 |
Advertise loopback0 on R1 to other routers
| R1(config)#interface loopback0 R1(config-if)#ip address 1.1.1.1 255.255.255.0 R1(config-if)#exit R1(config)#router bgp 1 R1(config-router)#network 1.1.1.0 mask 255.255.255.0 |
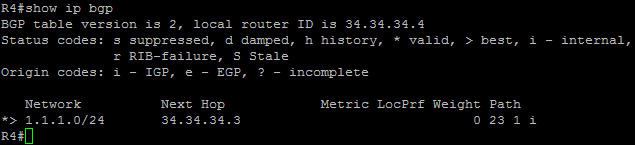
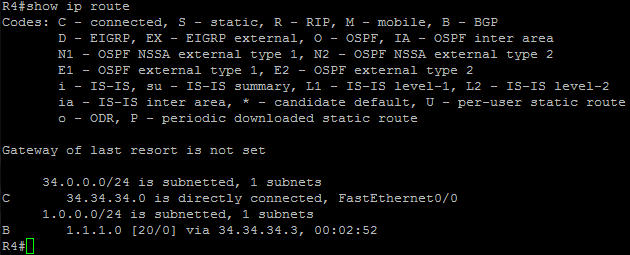
Now we can see 1.1.1.0/24 on all routers. For example on R4 we see:
Task 2: Use distribute-list to filter out network 1.1.1.0
On R2 configure an access-list and apply it in the distribute-list under BGP mode.
| R2(config)#access-list 1 deny 1.1.1.0 0.0.0.255 R2(config)#access-list 1 permit any R2(config)#router bgp 23 R2(config-router)#neighbor 12.12.12.1 distribute-list 1 in |
Now network 1.1.1.0 disappears in both BGP routing table and routing table of R4
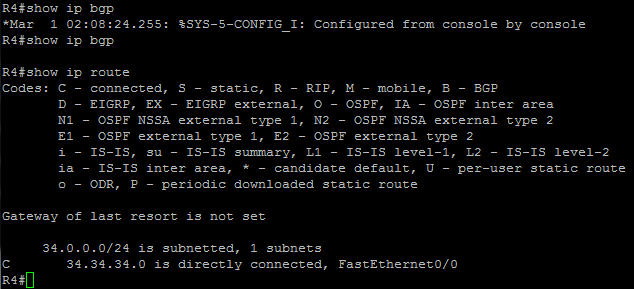
You can check to see the access-list 1 has been matched with the “show access-list 1” command:
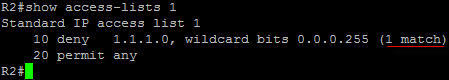
Another way to complete this task is to apply the distribute-list on R3
| R3(config)#access-list 1 deny 1.1.1.0 0.0.0.255 R3(config)#access-list 1 permit any R3(config)#router bgp 23 R3(config-router)#neighbor 34.34.34.4 distribute-list 1 out |
In practical we should apply the distribute-list on R2 so that routers in our company don’t need to learn about that route.



Couldnt it be a third viable option of setting up a distribute-list on R3 with ‘in’ option:
neighbor 23.23.23.2 distribute-list 1 in ?
Thanks
Satrel – That would still work (filtering as the traffic gets into R3), however, the principle is “avoid unnecessary traffic into your network” else it consumes your bandwidth for nothing, therefore filter the traffic out before it gets into AS 23 if it is not required (at R2 in).
If we are a company represented by AS23, wouldn’t we want both our routers R2 and R3 to know about the 1.1.1.1/24 prefix? Thereby making the best option as you described secondly filter out on R3 towards R4?