New ENCOR Questions- Part 7
Premium Member: You can practice these questions first via these links:
+ Question 1 to 20
+ Question 21 to 40
+ Question 41 to 60
+ Question 61 to 80
+ Question 81 to 99
or practice all 99 questions of this part 7 at All ENCOR Questions – Part 7
Question 1
An engineer must export the contents of the devices object in JSON format. Which statement must be use?
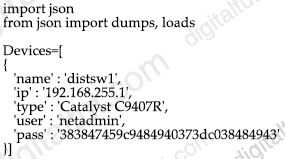
A. json.print(Devices)
B. json.loads(Devices)
C. json.dumps(Devices)
D. json.repr(Devices)
Answer: C
Explanation
json.loads() takes in a string and returns a json object while json.dumps() takes in a json object and returns a string. In this question, “Devices” is a ‘list’, not a string so we have to “dumps” it first to convert it into a string before printing it out.
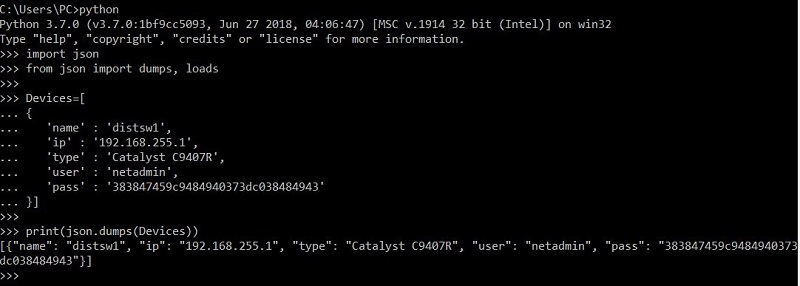
Try printing with “loads”:
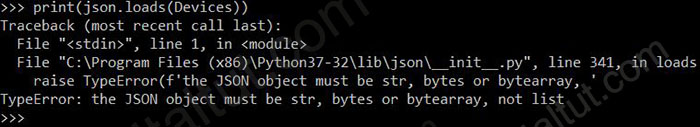
Note: JSON does not have attributes “print” or “repr” so we cannot use them.
Question 2
What is the function of Cisco DNA Center in a Cisco SD-Access deployment?
A. It is responsible for routing decisions inside the fabric
B. It is responsible for the design, management, deployment, provisioning, and assurance of the fabric network devices
C. It possesses information about all endpoints, nodes, and external networks related to the fabric
D. It provides integration and automation for all nonfabric nodes and their fabric counterparts
Answer: B
Question 3
Refer to the exhibit.

An engineer troubleshoots connectivity issues with an application. Testing is performed from the server gateway, and traffic with the DF bit set is dropped along the path after increasing packet size. Removing the DF bit setting at the gateway prevents the packets from being dropped. What is the cause of this issue?
A. PMTUD does not work due to ICMP Packet Too Big messages being dropped by an ACL
B. The remote router drops the traffic due to high CPU load
C. The server should not set the DF bit in any type of traffic that is sent toward the network
D. There is a CoPP policy in place protecting the WAN router CPU from this type of traffic
Answer: C
Explanation
If the DF bit is set, routers cannot fragment packets. The ping result of “MMMMM” means “Maximum transmission unit (MTU) problem. Could not fragment.” -> In this case, packet needs to be fragmented but we disabled fragmentation via DF bit.
Question 4
Refer to the exhibit.
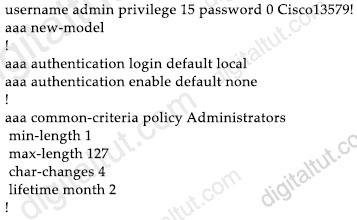
A network engineer must configure a password expiry mechanism on the gateway router for all local passwords to expire after 60 days. What is required to complete this task?
A. Add the username admin privilege 15 common-criteria-policy Administrators password 0 Cisco013579! command
B. No further action is required. The configuration is complete
C. Add the aaa authentication enable default Administrators command
D. The password expiry mechanism is on the AAA server and must be configured there
Answer: A
Explanation
The command “username username common-criteria-policy policy-name password password” applies a specific policy and password to a user profile.
In the exhibit above, we see the policy “Administrators” satisfies the requirements of “all local passwords to expire after 60 days” but this policy has not been applied to any user so we have to use above command to apply to local user “admin”.
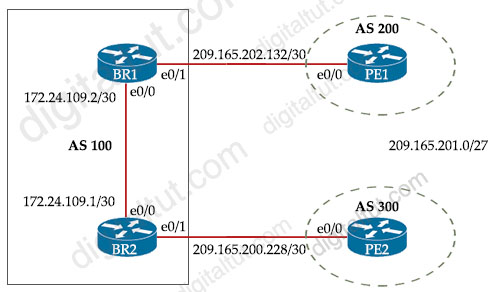
Question 5
Refer to the exhibit.
| BR1 router bgp 100 neighbor 172.24.109.1 remote-as 100 neighbor 172.24.109.1 next-hop self neighbor 209.165.202.134 remote-as 200 |
PE1 router bgp 200 bgp log-neighbor-changes neighbor 209.165.202.133 remote as 100 |
| BR2 router bgp 100 neighbor 172.24.109.2 remote-as 100 neighbor 172.24.109.2 next-hop-self neighbor 209.165.200.230 remote-as 300 |
PE2 router bgp 300 bgp log-neighbor-changes neighbor 209.165.200.229 remote as 100 |
BR2#sh ip route | i 209.165.201.0 209.165.201.0/27 is subnetted, 1 subnets B 209.165.201.0 [20/0] via 209.165.200.230, 00:00:12
Which configuration change will force BR2 to reach 209.165.201.0/27 via BR1?
A. Set the origin to igp on BR2 toward PE2 inbound
B. Set the local preference to 150 on PE1 toward BR1 outbound
C. Set the weight attribute to 65,535 on BR1 toward PE1
D. Set the MED to 1 on PE2 toward BR2 outbound
Answer: D
Explanation
We cannot set the local preference on PE1 because local preference is only sent to iBGP neighbors so this attribute cannot reach BR1 -> Answer B is not correct.
Weight attribute is only used locally in a router (not be exchanged between BGP neighbors) so we cannot affect BR2 from BR1 with this attribute -> Answer C is not correct.
We cannot affect BR2 routing decision by modifying BGP advertisements from BR2 toward PE2 (inbound) -> A is not correct. Also if network 209.165.201.0/27 is advertised with “network” statement in BGP, BR2 will match it with origin “IGP”. Please check the example in the link below.
By default, the MED attribute is set to 0 so by increasing the MED on PE2 toward BR2, BR2 would think the metric of its direct link to PE2 is higher than the path advertised by BR1 -> BR2 would use BR1 to reach 209.165.201.0/27.
Good lab example and reference: https://www.cisco.com/c/en/us/support/docs/ip/border-gateway-protocol-bgp/13759-37.html
Question 6
What is a benefit of YANG?
A. It enables multiple leaf statements to exist within a leaf list.
B. It enforces configuration constraints.
C. It collects statistical constraint analysis information.
D. It enforces the use of a specific encoding format for NETCONF.
Answer: B
Explanation
YANG (Yet Another Next Generation) is a data modeling language for the definition of data sent over network management protocols such as the NETCONF and RESTCONF.
YANG allows you to define constraints and rules for configuration and operational data, such as Data types, Value ranges, dependencies between configuration elements. By enforcing these constraints, YANG helps ensure that configurations are valid and conform to the intended structure, preventing misconfigurations.
Question 7
Refer to the exhibit.
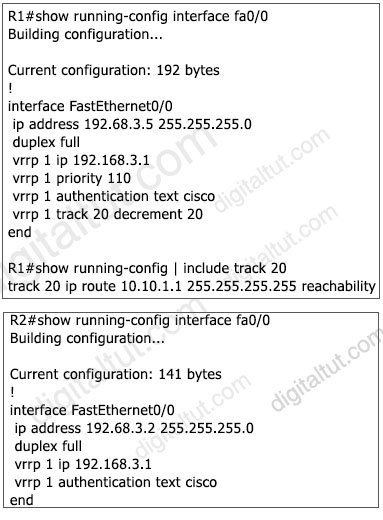
An engineer configures VRRP and issues the show commands to verify operation. What does the engineer confirm about VRRP group 1 from the output?
A. There is no route to 10.10.1.1/32 in R2’s routing table
B. If R1 reboots, R2 becomes the master virtual router until R2 reboots
C. Communication between VRRP members is encrypted using MD5
D. R1 is master if 10.10.1.1/32 is in its routing table
Answer: D
Explanation
We don’t have any information about the route to 10.10.1.1/32 so we cannot say if answer A is correct or not.
Answer B is not correct because if R2 reboots, R2 only becomes the master until R1 is up again (not until R2 reboots) because “preempt” is enabled by default with VRRP.
Answer C is not correct because R1 & R2 are authenticating via plain text, not MD5.
R1 is tracking the route to 10.10.1.1/32, if this route is removed from R1’s routing table, the VRRP priority of R1 would be decreased by 20 (110 – 20 = 90) which is smaller than the priority of R2 -> R2 would take the master role -> Answer D is correct.
Question 8
Refer to the exhibit.
flow record Recorder match ipv4 protocol match ipv4 source address match ipv4 destination address match transport source-port match transport destination-port ! flow exporter Exporter destination 192.168.100.22 transport udp 2055 ! flow monitor Monitor exporter Exporter record Recorder ! et-analytics ip flow-export destination 192.168.100.22 2055 ! interface gi1 ip flow monitor Monitor input ip flow monitor Monitor output et-analytics enable !
An engineer must add the SNMP interface table to the NetFlow protocol flow records. Where should the SNMP table option be added?
A. under the interface
B. under the flow record
C. under the flow monitor
D. under the flow exporter
Answer: D
Explanation
The following example shows how to enable the periodic sending of an options table that allows the collector to map the interface SNMP indexes provided in flow records to interface names:
Device(config)# flow exporter FLOW-EXPORTER-1
Device(config-flow-exporter)# option interface-table
Question 9
Refer to the exhibit.

|
BR(config)#interface tunnel1 HQ(config)#interface tunnel1 |
What is the effect of these commands on the BR and HQ tunnel interfaces?
A. The tunnel line protocol goes down when the keepalive counter reaches 6
B. The keepalives are sent every 5 seconds and 3 retries
C. The keepalives are sent every 3 seconds and 5 retries.
D. The tunnel line protocol goes down when the keepalive counter reaches 5
Answer: B
Explanation
The syntax of keepalive command is: keepalive {seconds retries} so R1 will send keepalive message every 5 seconds and retry 3 times. If all of the keepalive messages are failed, R1 concludes the tunnel was broken.
Question 10
In Cisco SD-WAN, which protocol is used to measure link quality?
A. OMP
B. BFD
C. RSVP
D. IPsec
Answer: B
Question 11
What is used to perform QoS packet classification?
A. the Options field in the Layer 3 header
B. the Type field in the Layer 2 frame
C. the Flags field in the Layer 3 header
D. the ToS field in the Layer 3 header
Answer: D
Explanation
Layer-3 marking is accomplished using the 8-bit Type of Service (ToS) field, part of the IP header. A mark in this field will remain unchanged as it travels from hop-to-hop, unless a Layer-3 device is explicitly configured to overwrite this field. There are two marking methods that use the ToS field:
+ IP Precedence: uses the first three bits of the ToS field.
+ Differentiated Service Code Point (DSCP): uses the first six bits of the ToS field. When using DSCP, the ToS field is often referred to as the Differentiated Services (DS) field.
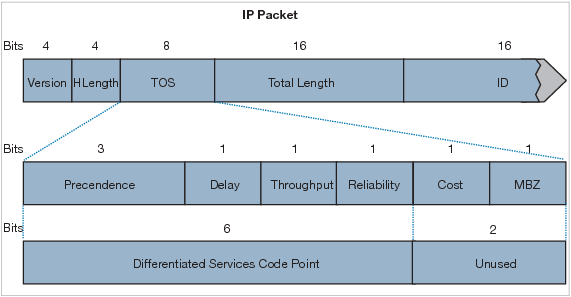
Question 12
Refer to the exhibit.
def get_token():
device_url="https://192.168.1.1/dna/sytem/api/v1/auth/token"
http_result = requests.post(device_url, auth = ("test","test34393838!"))
if http_result.status_code != requests.codes.ok:
print("Call failed!" Review get_token().")
sys.exit()
return(http_result.json()["Token"])
Which HTTP code must be returned to prevent the script from exiting?
A. 200
B. 201
C. 300
D. 301
Answer: A
Explanation
In order to prevent the script from exiting, the returned code must equal to “requests.codes.ok” so that the “sys.exit()” statement does not run. “requests.codes.ok” here is 200:
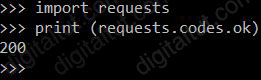
Question 13
Which LISP component is required for a LISP site to communicate with a non-LISP site?
A. ETR
B. ITR
C. Proxy ETR
D. Proxy ITR
Answer: C
Explanation
The proxy egress tunnel router (PETR) allows the communication from the LISP sites to the non-LISP sites. The PETR receives LISP encapsulated traffic from ITR.
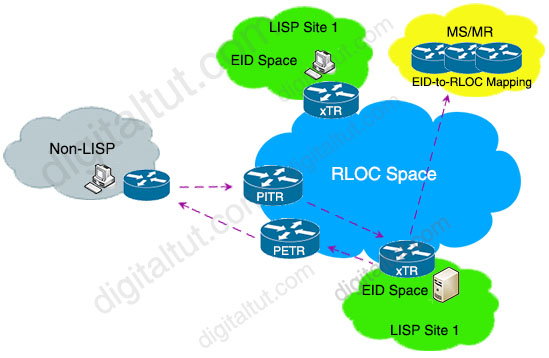
Question 14
What is a characteristic of a next-generation firewall?
A. only required at the network perimeter
B. required in each layer of the network
C. filters traffic using Layer 3 and Layer 4 information only
D. provides intrusion prevention
Answer: D
Question 15
Which technology is used as the basis for the Cisco SD-Access data plane?
A. IPsec
B. LISP
C. VXLAN
D. 802.1Q
Answer: C
Question 16
“HTTP/1.1 204 content” is returned when cur -l -x DELETE command is issued. Which situation has occurred?
A. The object could not be located at the URI path
B. The command succeeded in deleting the object
C. The object was located at the URI, but it could not be deleted
D. The URI was invalid
Answer: B
Explanation
The HTTP 204 No Content success status response code indicates that a request has succeeded, but that the client doesn’t need to navigate away from its current page.
Question 17
An engineer must provide wireless converge in a square office. The engineer has only one AP and believes that it should be placed it in the middle of the room. Which antenna type should the engineer use?
A. directional
B. polarized
C. Yagi
D. omnidirectional
Answer: D
Explanation
Types of external antennas:
+ Omnidirectional: Provide 360-degree coverage. Ideal in houses and office areas
+ Directional: Focus the radio signal in a specific direction. Examples are the Yagi and parabolic dish
+ Multiple Input Multiple Output (MIMO) – Uses multiple antennas (up to eight) to increase bandwidth
An omnidirectional antenna is designed to provide a 360-degree radiation pattern. This type of antenna is used when coverage in all directions from the antenna is required.
Omnidirectional Antenna Radiation Pattern
Question 18
While configuring an IOS router for HSRP with a virtual IP of 10.1.1.1, an engineer sees this log message:
| Jan 1 12:12:14.122: %HSRP-4-DIFFVIP1: GigabitEthernet0/0 Grp 1 active routers virtual IP address 10.1.1.1 is different to the locally configured address 10.1.1.25 |
Which configuration change must the engineer make?
A. Change the HSRP group configuration on the remote router to 1
B. Change the HSRP virtual address on the local router to 10.1.1.1
C. Change the HSRP virtual address on the remote router to 10.1.1.1
D. Change the HSRP group configuration on the local router to 1
Answer: B
Explanation
The local router was configured with command “standby 1 ip 10.1.1.25” while the peer HSRP router was configured with command “standby 10 ip 10.1.1.1”
Question 19
What is a characteristic of YANG?
A. It is a Cisco proprietary language that models NETCONF data
B. It allows model developers to create custom data types
C. It structures data in an object-oriented fashion to promote model reuse
D. It provides loops and conditionals to control now within models
Answer: C
Question 20
What is the function of the LISP map resolver?
A. to send traffic to non-LISP sites when connected to a service provider that does not accept nonroutable EIDs as packet sources
B. to connect a site to the LISP-capable part of a core network, publish the EID-to-RLOC mappings for the site and respond to map-request messages
C. to decapsulate map-request messages from ITRs and forward the messages to the MS
D. to advertise routable non-USP traffic from one address family to LISP sites in a different address family
Answer: C
Explanation
Map Resolver (MR): a LISP component which accepts LISP Encapsulated Map Requests, typically from an ITR, quickly determines whether or not the destination IP address is part of the EID namespace
Question 21
When is an external antenna used inside a building?
A. only when using 5 GHz
B. only when using 2.4 GHz
C. when it provides the required coverage
D. only when using Mobility Express
Answer: C
Question 22
Drag and drop the snippets onto the blanks within the code construct a script that configure a loopback interface with an IP address. Not all options are used.
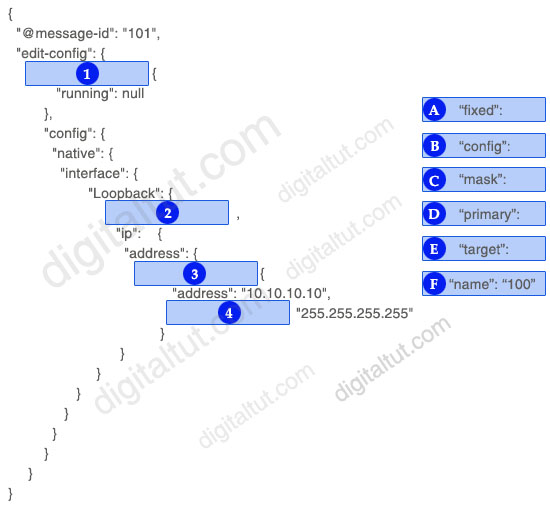
Answer:
1 – E
2 – F
3 – D
4 – C
Explanation
The code above is written in NETCONF with JSON format.
Question 23
Drag and drop the characteristics from the left onto the orchestration tools they describe on the right.
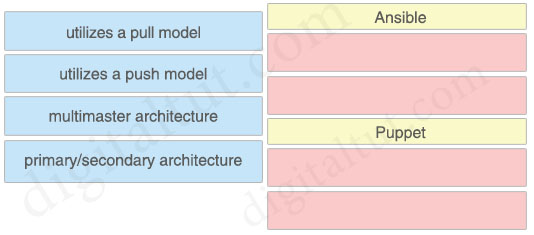
Answer:
Ansible
+ utilizes a push model
+ primary/secondary architecture
Puppet
+ utilizes a pull model
+ multimaster architecture
Explanation
Ansible runs with a single active node, called the Primary instance. If the primary goes down, there is a Secondary instance to take its place.
Puppet has multi-master architecture. If the active master goes down, then the other master takes the active master place.
Reference: https://www.javatpoint.com/ansible-vs-puppet
Question 24
Refer to the exhibit.
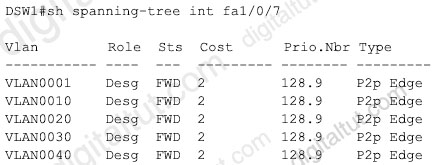
How was spanning-tree configured on this interface?
A. By entering the command spanning-tree portfast trunk in the interface configuration mode.
B. By entering the command spanning-tree portfast in the interface configuration mode
C. By entering the command spanning-tree mst1 vlan 10,20,30,40 in the global configuration mode
D. By entering the command spanning-tree vlan 10,20,30,40 root primary in the interface configuration mode
Answer: A
Explanation
As we see in the output, the type of this interface in all VLANs are “Edge” (which automatically transitions the port to the spanning tree forwarding state without passing through the blocking or learning states) so maybe this interface was configured with “portfast” command. There are many VLANs on this single interface so we can deduce it is a trunk port. Therefore the best answer here should be the command “spanning-tree portfast trunk” has been entered.
Question 25
An engineer is troubleshooting the AP join process using DNS. Which FQDN must be resolvable on the network for the access points to successfully register to the WLC?
A. cisco-capwap-controller.domain.com
B. wlchostname.domain.com
C. ap-manager.domain.com
D. primary-wlc.domain.com
Answer: A
Explanation
The lightweight access points support the following controller discovery processes:
…
DNS discovery—The access point can discover controllers through your domain name server (DNS). You must configure your DNS to return controller IP addresses in response to CISCO-CAPWAP-CONTROLLER.localdomain, where localdomain is the access point domain name. When an access point receives an IP address and DNS information from a DHCP server, it contacts the DNS to resolve CISCO-CAPWAP-CONTROLLER.localdomain. When the DNS sends a list of controller IP addresses, the access point sends discovery requests to the controllers.
Question 26
How is Layer 3 roaming accomplished in a unified wireless deployment?
A. An EoIP tunnel is created between the client and the anchor controller to provide seamless connectivity as the client is associated with the new AP
B. The client entry on the original controller is passed to the database on the new controller
C. The new controller assigns an IP address from the new subnet to the client
D. The client database on the original controller is updated the anchor entry, and the new controller database is updated with the foreign entry.
Answer: D
Explanation
An EoIP tunnel is created between the anchor and foreign controller, not between the client and the anchor controller -> Answer A is not correct.
In instances where the client roams between APs that are connected to different WLCs and the WLC WLAN is connected to a different subnet, a Layer 3 roam is performed, and there is an update between the new WLC (foreign WLC) and the old WLC (anchor WLC) mobility databases.
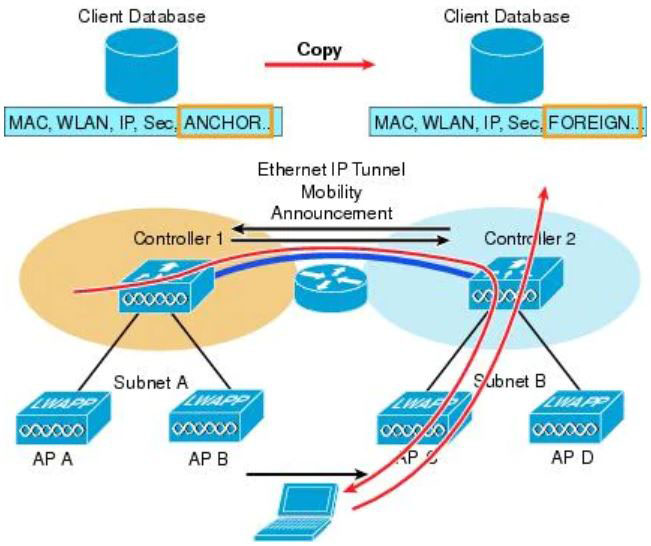 The client begins with a connection to AP B on WLC 1. This creates an ANCHOR entry in the WLC client database (-> Answer D is correct as the client database is marked “ANCHOR”). As the client moves away from AP B and makes an association with AP C, WLC 2 sends a mobility announcement to peers in the mobility group looking for the WLC with the client MAC address. WLC 1 responds to the announcement, handshakes, and ACKs. Next the client database entry for the roaming client is copied to WLC 2, and marked as FOREIGN. Included PMK data (master key data from the RADIUS server) is also copied to WLC 2. This provides fast roam times for WPA2/802.11i clients because there is no need to re-authenticate to the RADIUS server.
The client begins with a connection to AP B on WLC 1. This creates an ANCHOR entry in the WLC client database (-> Answer D is correct as the client database is marked “ANCHOR”). As the client moves away from AP B and makes an association with AP C, WLC 2 sends a mobility announcement to peers in the mobility group looking for the WLC with the client MAC address. WLC 1 responds to the announcement, handshakes, and ACKs. Next the client database entry for the roaming client is copied to WLC 2, and marked as FOREIGN. Included PMK data (master key data from the RADIUS server) is also copied to WLC 2. This provides fast roam times for WPA2/802.11i clients because there is no need to re-authenticate to the RADIUS server.
After a simple key exchange between the client and AP, the client is added to the WLC 2 database and is similar, except that it is marked as FOREIGN.
Reference: https://www.cisco.com/en/US/docs/solutions/Enterprise/Mobility/emob30dg/TechArch.html and https://mrncciew.com/2013/03/17/l3-inter-controller-roaming/
In Layer 3 roaming, no IP address refresh needed (although client must be re-authenticated and new security session established) -> Answer C is not correct.
In summary, the “Mobility State” of a client is described below:
+ Before roaming: Mobility State = Local
+ After roaming: Mobility State on Old Database = Anchor; Mobility State on New Database = Foreign
Therefore the client entry on the original controller is not passed to the database totally. The client entry is still on the old controller but it is marked “Anchor” -> Answer B is not correct.
Question 27
A network administrator has designed a network with two multilayer switches on the distribution layer, which act as default gateways for the end hosts. Which two technologies allow every end host in a VLAN to use both gateways? (Choose two)
A. HSRP
B. GLBP
C. MHSRP
D. VRRP
E. VSS
Answer: B C
Explanation
We can load share traffic in HSRP by using feature set called as Multiple HSRP wherein for a particular Group first path will be active and second as backup and for other group second path with be active and first the backup.
Question 28
Which measurement is used from a post wireless survey to depict the cell edge of the access points?
A. CCI
B. Noise
C. SNR
D. RSSI
Answer: D
Explanation
The following are elements that you should consider when performing a post assessment of the environment.
Analyze and define the cell edge: This requires the use of AirMagnet Survey, although there are simple tools like Omnipeek or Wireshark that can be used to measure wireless traffic as a client roams from one AP to another. According to design best practices that revolve around the Cell Edge Design, a wireless handset should roam before the RSSI reaches -67 dBm. You can analyze signal strength and determine the approximate cell edge by measuring the signal strength in a beacon frame as you move from the center of one cell towards the edge of that cell.
Question 29
Refer to the exhibit.
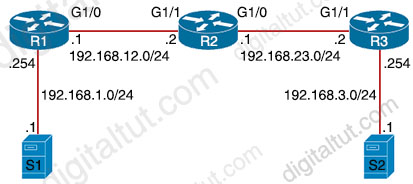
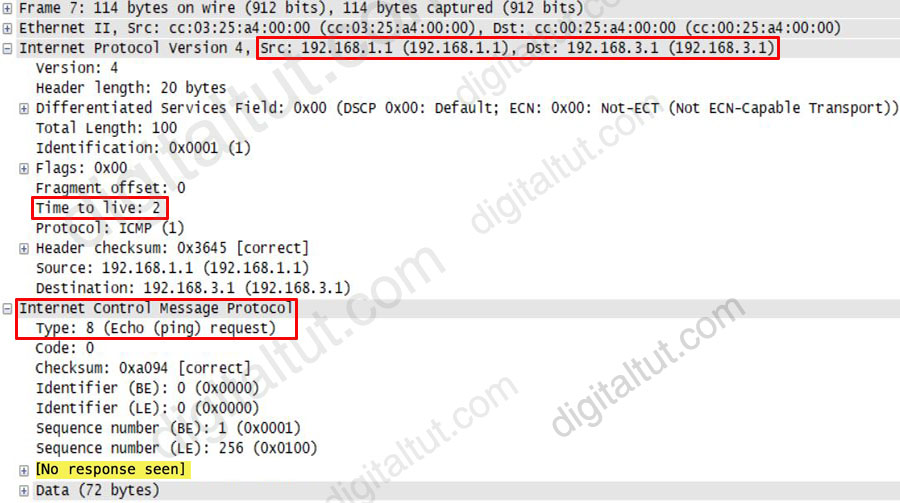
While troubleshooting a routing issue, an engineer issues a ping from S1 to S2. Which two actions from the initial value of the TTL? (Choose two)
A. The packet reaches R3, and the TTL expires
B. R2 replies with a TTL exceeded message
C. R1 replies with a TTL exceeded message
D. The packet reaches R2 and the TTL expires
E. R3 replies with a TTL exceeded message
F. The packet reaches R1 and the TTL expires
Answer: B D
Explanation
“Routers decrement the TTL by 1 every time they forward a packet; if a router decrements the TTL to 0, it throws away the packet. This prevents packets from rotating forever.” We want to make it clear that before the router forwards a packet, the TTL is still remain the same.
For example in the topology below, pings to S0/1 and S0/0 of Router 2 have the same TTL.
If a router finds a TTL value of 1 or 0, it drops the datagram and sends an Internet Control Message Protocol (ICMP) time-to-live-exceeded message to the sender.
The picture below shows TTL values for each interface of each router and for Host B. Notice that Host A initializes ICMP packet with a TTL of 255:
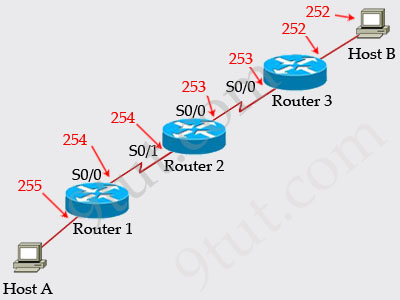
Therefore in this question, if the initial TTL is 2, then R1 receives the packet with TTL of 2, then it decreases the TTL before forwarding to R2. R2 receives packet with TTL of 1 then decreases the TTL to 0 so R2 drops the packet ( -> Answer D is correct). R2 also replies back to the source with an ICMPv4 Type 11, Code 0 Time Exceeded message -> Answer B is correct.
Question 30
Refer to the exhibit.
Router#show access-list Extended IP access list 100 10 permit ip 192.168.0.0 0.0.255.255 any 20 permit ip 172.16.0.0 0.0.15.255 any
Which command set must be added to permit and log all traffic that comes from 172.20.10.1 in interface GigabitEthernet0/1 without impacting the functionality of the access list?
|
Option A Router(config)#ip access-list extended 100 |
|
Option B Router(config)#no access-list 100 permit ip 172.16.0.0 0.0.15.255 any |
|
Option C Router(config)#access-list 100 permit ip host 172.20.10.1 any log |
|
Option D Router(config)#access-list 100 seq 5 permit ip host 172.20.10.1 any log |
A. Option A
B. Option B
C. Option C
D. Option D
Answer: C
Explanation
Option A logs the whole subnet 172.20.10.0/24, not only host 172.20.10.1 so it is not correct.
Option B does not log traffic coming from 172.20.10.1 so it is not correct.
We tested option D but the command “access-list 100 seq 5 permit ip host 172.20.10.1 any log” is not accepted as shown below:

Option C would append the access-list (statement 30 in the above figure) so it is the best answer.
Question 31
What is the function of a fabric border node in a Cisco SD-Access environment?
A. To connect the Cisco SD-Access fabric to another fabric or external Layer 3 networks
B. To collect traffic flow information toward external networks
C. To attach and register clients to the fabric
D. To handle an ordered list of IP addresses and locations for endpoints in the fabric.
Answer: A
Explanation
There are five basic device roles in the fabric overlay:
+ Control plane node: This node contains the settings, protocols, and mapping tables to provide the endpoint-to-location (EID-to-RLOC) mapping system for the fabric overlay.
+ Fabric border node: This fabric device (for example, core layer device) connects external Layer 3 networks to the SDA fabric.
+ Fabric edge node: This fabric device (for example, access or distribution layer device) connects wired endpoints to the SDA fabric.
+ Fabric WLAN controller (WLC): This fabric device connects APs and wireless endpoints to the SDA fabric.
+ Intermediate nodes: These are intermediate routers or extended switches that do not provide any sort of SD-Access fabric role other than underlay services.
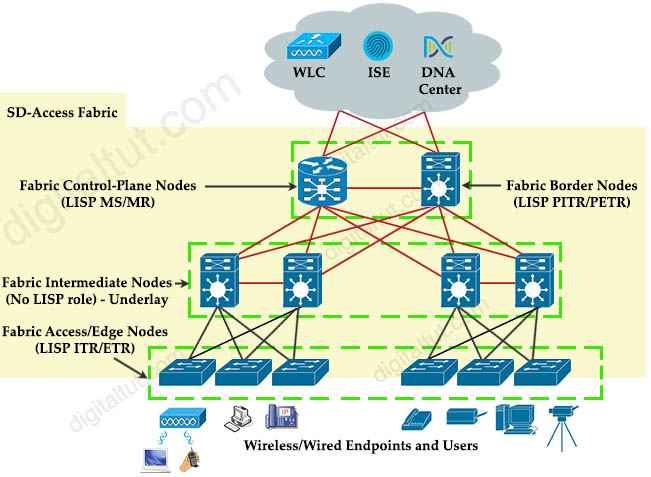
Reference: CCNP and CCIE Enterprise Core ENCOR 350-401 Official Cert Guide
Question 32
How are the different versions of IGMP compatible?
A. IGMPv2 is compatible only with IGMPv1
B. IGMPv2 is compatible only with IGMPv2
C. IGMPv3 is compatible only with IGMPv3
D. IGMPv3 is compatible only with IGMPv1
Answer: A
Explanation
IGMPv3 is backward compatible with previous versions of the IGMP protocol. In order to remain backward compatible with older IGMP
systems, IGMPv3 multicast routers MUST also implement versions 1 and 2 of the protocol.
Reference: https://datatracker.ietf.org/doc/html/rfc3376
IGMPv2 is only compatible with IGMPv1
Note: When saying “compatible”, we only mention about older version, not newer version. For example, we cannot say “IGMPv2 is compatible with IGMPv3” because IGMPv3 is newer. But we can say “IGMPv3 is compatible with IGMPv2”.
Question 33
What is one benefit of implementing a VSS architecture?
A. It provides multiple points of management for redundancy and improved support.
B. It provides a single point of management for improved efficiency
C. It uses GLBP to balance traffic between gateways
D. It uses a single database to manage configuration for multiple switches
Answer: B
Explanation
VSS increases operational efficiency by reducing switch management overhead and simplifying the network. It provides a single point of management, IP address, and routing instance.
VSS can be managed with single management point from which you configure and manage the VSS. Neighbors see the VSS as a single Layer 2 switching or Layer 3 routing node, thus reducing the control protocol traffic. VSS provides a single VLAN gateway IP address, removing the need for the first-hop redundancy protocol (HSRP, VRRP, GLBP). Multichannel EtherChannel (MEC) allows you to bundle links to two physical switches in VSS, creating a loop-free redundant topology without the need for STP.
Reference: Implementing Cisco IP Switched Networks (SWITCH) Foundation Learning Guide Book
Question 34
Which entity is a Type 1 hypervisor?
A. Oracle VM VirtualBox
B. VMware server
C. Citrix XenServer
D. Microsoft Virtual PC
Answer: C
Explanation
Type 1 hypervisor has direct access to the hardware resources. Therefore they are more efficient than hosted architectures. Some examples of type 1 hypervisor are VMware vSphere/ESXi, Oracle VM Server, KVM and Microsoft Hyper-V. Xen/Citrix XenServer is also a type 1 hypervisor.
Question 35
An engineer runs the code against an API of Cisco DNA Center, and the platform returns this output.
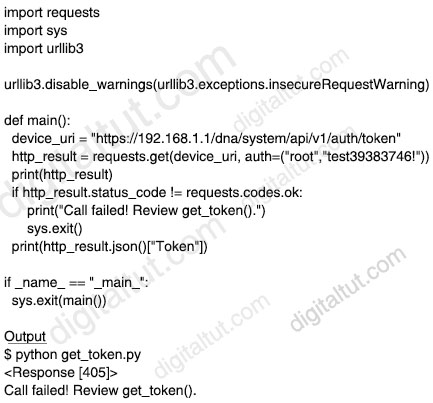
What does the response indicate?
A. The authentication credentials are incorrect
B. The URI string is incorrect
C. The Cisco DNA Center API port is incorrect
D. The HTTP method is incorrect
Answer: D
Explanation
From the output, we learn that a “Response [405]” was returned. The 405 Method Not Allowed is an HTTP response status code indicating that the specified request HTTP method was received and recognized by the server, but the server has rejected that particular method for the requested resource. Therefore answer B is not correct.
From this page (https://developer.cisco.com/docs/dna-center/#!command-runner/endpoints-and-methods-used), we may find out where the issue is:
“The Authentication endpoint used in this guide is /dna/system/api/v1/auth/token, which is valid for version 1.2.6 and above. The HTTP method used for the endpoint is POST and it requires for the user to send its credentials using Basic Authentication.
Note: For systems with versions below that, the endpoint is /api/system/v1/auth/token”
Therefore the most suitable reason for this issue is we have to use “POST” instead of “GET” (in requests.get) -> Answer D is the best choice.
Question 36
What is a consideration when designing a Cisco SD-Access underlay network?
A. End user subnets and endpoints are part of the underlay network
B. The underlay switches provide endpoint physical connectivity for users
C. Static routing is a requirement
D. It must support IPv4 and IPv6 underlay networks
Answer: B
Explanation
In SD-Access, the underlay switches (edge nodes) support the physical connectivity for users and endpoints. However, end-user subnets and endpoints are not part of the underlay network—they are part of the automated overlay network.
https://www.cisco.com/c/en/us/td/docs/solutions/CVD/Campus/cisco-sda-design-guide.html
Question 37
What is a characteristic of a virtual machine?
A. It relies on hypervisors to allocate computing resources for it
B. It is deployable without a hypervisor to host it
C. It must run the same operating system as its host
D. It must be aware of other virtual machines, in order to allocate physical resources for them
Answer: A
Question 38
What is one difference between Saltstack and Ansible?
A. SaltStack uses an API proxy agent to program Cisco boxes on agent mode, whereas Ansible uses a Telnet connection
B. SaltStack uses the Ansible agent on the box, whereas Ansible uses a Telnet server on the box
C. SaltStack is constructed with minion, whereas Ansible is constructed with YAML
D. SaltStack uses SSH to interact with Cisco devices, whereas Ansible uses an event bus
Answer: C
Explanation
– Saltstack uses YAML (Python) same as Ansible.
– Saltstack uses the push model for executing commands via the SSH protocol
– Ansible only uses SSH, not Telnet.
In SaltStack architecture, there is a core component called Salt-minion, which is a system that is being controlled by a Salt master.
Question 39
What is the centralized control policy in a Cisco SD-WAN deployment?
A. list of ordered statements that define user access policies
B. list of enabled services for all nodes within the cloud
C. set of rules that governs nodes authentication within the cloud
D. set of statements that defines how routing is performed
Answer: D
Explanation
In Cisco SD-WAN, there are two types of Centralized Control Policies that fulfill different objectives:
+ Topology – Topology policies control the route information such as omp, tloc, and service routes that are being redistributed to a list of sites. As the name implies, they are typically used for limiting the number of overlay tunnels between sites and controlling the overlay topology.
+ VPN Membership – VPN Membership policies are used to control the distribution of routing information for specific VPNs to a list of sites. A typical use-case is for creating guest networks that have Internet access but site-to-site communication is restricted.
Reference: https://www.networkacademy.io/ccie-enterprise/sdwan/what-is-a-centralized-control-policy
Question 40
Which command set configures RSPAN to capture outgoing traffic from VLAN 3 on interface GigabitEthernet 0/3 while ignoring other VLAN traffic on the same interface?
|
Option A monitor session 2 source interface gigabitethernet0/3 rx |
|
Option B monitor session 2 source interface gigabitethernet0/3 tx |
|
Option C monitor session 2 source interface gigabitethernet0/3 rx |
|
Option D monitor session 2 source interface gigabitethernet0/3 tx |
A. Option A
B. Option B
C. Option C
D. Option D
Answer: B
Explanation
To “capture outgoing traffic” we have to use “tx” (transmitted) keyword. To only monitor VLAN 3 we have to use “monitor session 2 filter vlan 3”.
Question 41
Refer to the exhibit.
R1#show crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id status 209.165.201.6 209.165.201.1 QM_IDLE 101 ACTIVE
After configurating an IPsec VPN, an engineer enters the show command to verify the ISAKMP SA status. What does the status show?
A. Peers have exchanged keys, but ISAKMP SA remains unauthenticated.
B. ISAKMP SA is authenticated and can be used for Quick Mode.
C. VPN peers agreed on parameters for the ISAKMP SA
D. ISAKMP SA has been created, but it has not continued to form.
Answer: B
Explanation
The “show crypto isakmp sa” command displays all current Internet Key Exchange (IKE) security associations (SAs) at a peer.
QM_IDLE state means this tunnel is UP and the IKE SA key exchange was successful (authenticated), but is idle and may be used for subsequent quick mode exchanges. It is in a quiescent state (QM)
Question 42
Refer to the exhibit.
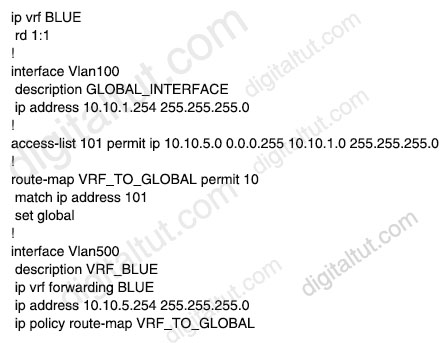
An engineer attempts to create a configuration to allow the Blue VRF to leak into the global routing table, but the configuration does not function as expected. Which action resolves this issue?
A. Change the access-list number in the route map
B. Change the source network that is specified in access-list 101
C. Change the route-map configuration to VRF_BLUE
D. Change the access-list destination mask to a wildcard
Answer: D
Explanation
We have to change the “10.10.1.0 255.255.255.0” to “10.10.1.0 0.0.0.255” in the ACL statement.
Question 43
Refer to the exhibit.
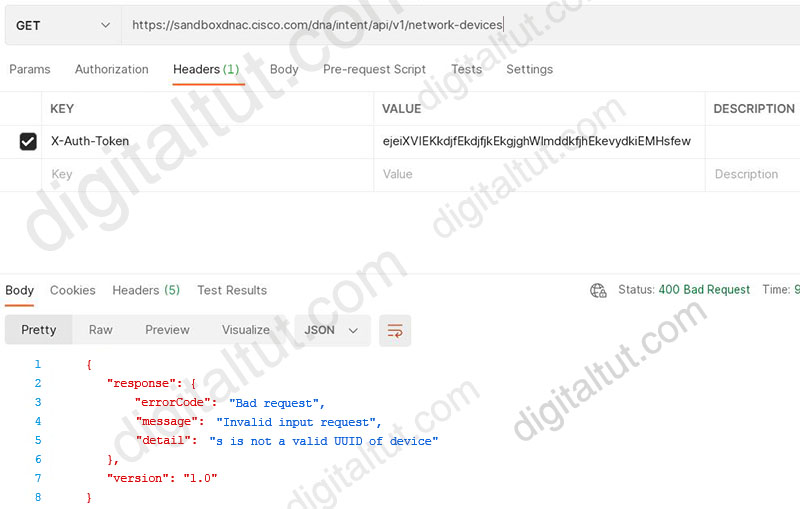
POSTMAN is showing an attempt to retrieve network device information from Cisco DNA Center API. What is the issue?
A. The token has expired
B. The URI string is incorrect
C. Authentication has failed
D. The JSON payload contains the incorrect UUID
Answer: B
Explanation
We tested with Postman successfully with URI https://sandboxdnac.cisco.com/dna/intent/api/v1/network-device
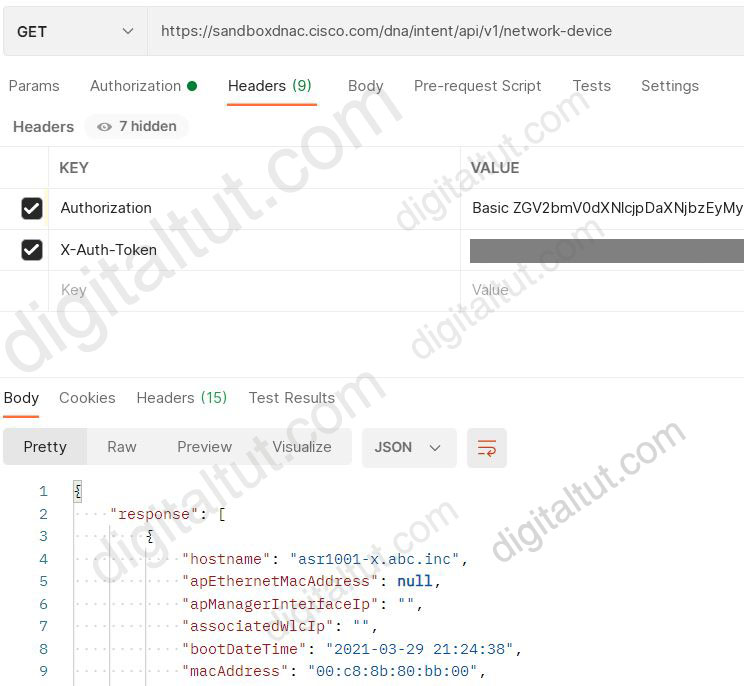
But when changing URI to https://sandboxdnac.cisco.com/dna/intent/api/v1/network-devices (appending the last letter “s” in “network-devices”) we could reproduce the error in this question:
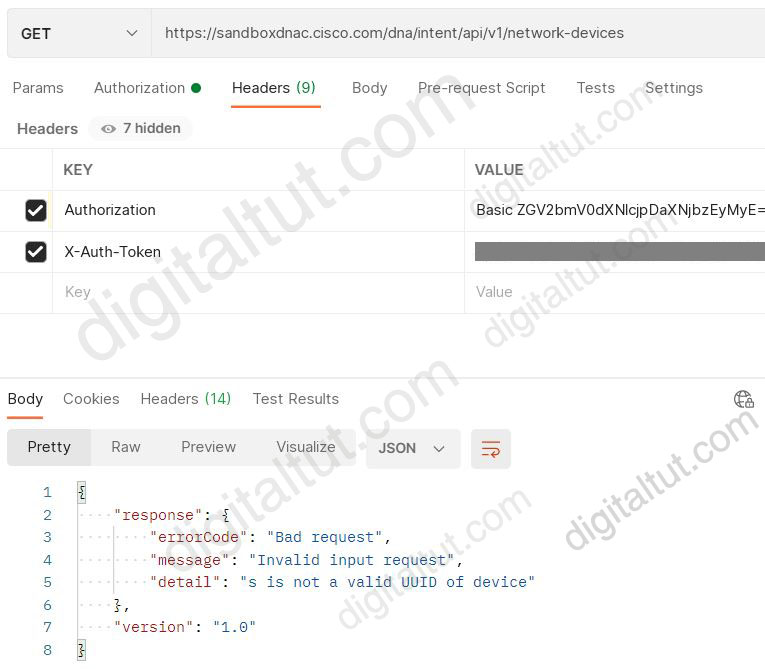
Therefore we can conclude the incorrect URI is the cause of this error.
If you want to check by yourself, this is a good tutorial for your reference https://garzum.net/cisco-dna-center-rest-api-calls-with-postman/
Question 44
Running the script causes the output in the exhibit. Which change to the first line of the script resolves the error?
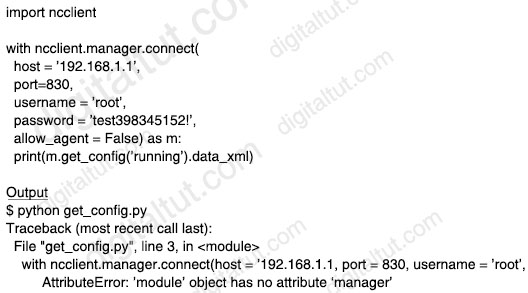
A. from ncclient import *
B. import manager
C. from ncclient import
D. import ncclient manager
Answer: A
Explanation
Importing a module (“ncclient” in this case) does not automatically import submodules/functions (“manager” in this case) so the above script causes error.
Answer B is not correct as we cannot directly import “manager” as it is a function in “ncclient”.
Answer C is not correct as we did not specify anything after keyword “import”.
Answer D is not correct as it is missing a dot “.” (it should be “import ncclient.manager).
We tested both answer ‘from ncclient import *’ and answer ‘import ncclient.manager’ in Python and both of them worked well.
Question 45
An engineer configures HSRP group 37. The configuration does not modify the default virtual MAC address. Which virtual MAC address does the group use?
A. 00:00:0c:07:ac:25
B. 00:00:0c:07:ac:37
C. C0:39:83:25:258:5
D. C0.00:00:25:00:00
Answer: A
Explanation
The last two-digit hex value in the MAC address presents the HSRP group number. In this case 37 in decimal is 25 in hexadecimal -> Answer A is correct.
Question 46
Which Cisco DNA center application is responsible for group-based access control permissions?
A. Design
B. Provision
C. Assurance
D. Policy
Answer: D
Question 47
Refer to the exhibit.
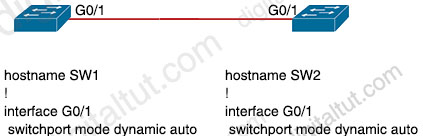
An engineer attempts to configure a trunk between switch SW1 and switch SW2 using DTP, but the trunk does not form. Which command should the engineer apply to switch SW2 to resolve this issue?
A. switchport mode access
B. switchport nonegotiate
C. no switchport
D. switchport mode dynamic desirable
Answer: D
Question 48
Refer to the exhibit.
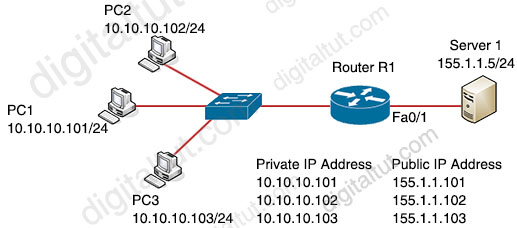
Which set of commands on router R1 allow deterministic translation of private hosts PC1, PC2, and PC3 to addresses in the public space?
|
Option A RouterR1(config)#int f0/0 |
|
Option B RouterR1(config)#int f0/0 |
|
Option C RouterR1(config)#int f0/0 |
|
Option D RouterR1(config)#int f0/0 |
A. Option A
B. Option B
C. Option C
D. Option D
Answer: C
Question 49
A client device roams between wireless LAN controllers that are mobility peers. Both controllers have dynamic interface on the same client VLAN. Which type of roam is described?
A. intra-VLAN
B. intra-controller
C. inter-controller
D. inter-subnet
Answer: C
Explanation
Inter Controller-L2 Roaming: Inter-Controller (normally layer 2) roaming occurs when a client roam between two APs registered to two different controllers, where each controller has an interface in the client subnet.
Question 50
Which line must be added in the Python function to return the JSON object {“cat_9k”:”FXS193202SE”)?
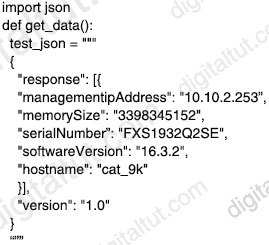
A. return (json.dumps({d[‘hostname’]: d[‘serialNumber’] for d in json.loads(test_json)[‘response’]}))
B. return (json.loads({for d in json.dumps(test_json)[‘response’]: d[‘hostname’]: d[‘serialNumber’]}))
C. return (json.loads({d[‘hostname’]: d[‘serialNumber’] for d in json.dumps(test_json)[‘response’]}))
D. return (json.dumps({for d in json.loads(test_json)[‘response’]: d[‘hostname’]: d[‘serialNumber’]}))
Answer: A
Explanation
Our first variable test_json is a string which we cannot loop through so we have to convert it into a dictionary type first with json.loads() function -> Therefore we must use “json.loads(test_json)[‘response’]”, not json.dumps(…) in the for loop. Then we can use the for loop to iterate through the dictionary. The script below is an example:
import json
json_string = '{"key1": "value1", "key2": "value2"}'
#Load JSON string to a dictionary
json_dictionary = json.loads(json_string)
#Loop through dictionary keys
for key in json_dictionary:
print(key, ":", json_dictionary[key])
OUTPUT:
key1 : value1
key2 : value2
-> Only answer A and answer D are correct.
We also tested both of the answers in Atom, only the first answer is correct:
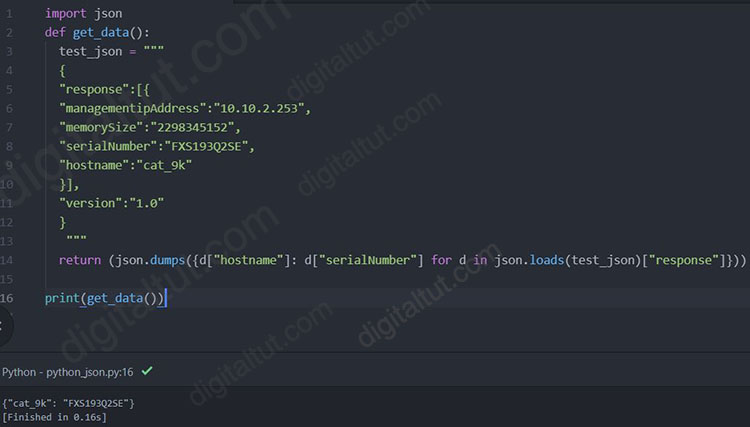
The second one returned error:
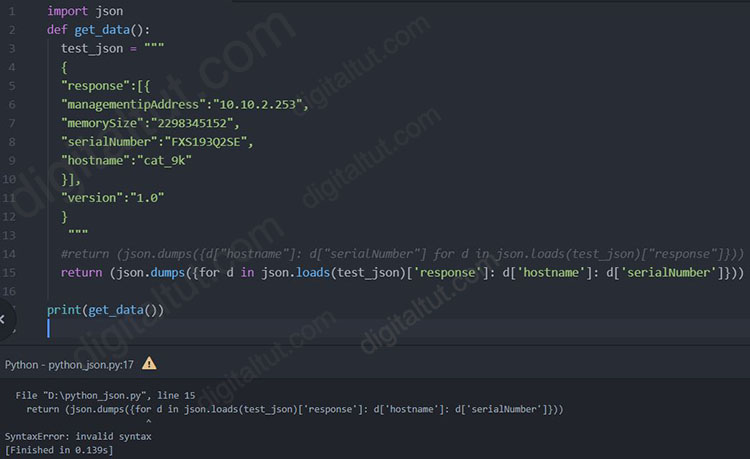
-> Only answer A is correct.
Note:
+ json.dumps() function converts a Python object into a json string. For example: json.dumps({‘name’: ‘John’,’age’: ’20’})
+ json.loads() method parses a valid JSON string and convert it into a Python Dictionary.
Question 51
Which two operational models enable an AP to scan one or more wireless channels for rouge access points and at the same time provide wireless services to clients? (Choose two)
A. Sniffer
B. Rouge detector
C. Local
D. FlexConnect
E. Monitor
Answer: C D
Explanation
An LAP operates in one of six different modes:
+ Local mode (default mode): measures noise floor and interference, and scans for intrusion detection (IDS) events every 180 seconds on unused channels
+ FlexConnect, formerly known as Hybrid Remote Edge AP (H-REAP), mode: allows data traffic to be switched locally and not go back to the controller. The FlexConnect AP can perform standalone client authentication and switch VLAN traffic locally even when it’s disconnected to the WLC (Local Switched). FlexConnect AP can also tunnel (via CAPWAP) both user wireless data and control traffic to a centralized WLC (Central Switched).
+ Monitor mode: does not handle data traffic between clients and the infrastructure. It acts like a sensor for location-based services (LBS), rogue AP detection, and IDS
+ Rogue detector mode: monitor for rogue APs. It does not handle data at all.
+ Sniffer mode: run as a sniffer and captures and forwards all the packets on a particular channel to a remote machine where you can use protocol analysis tool (Wireshark, Airopeek, etc) to review the packets and diagnose issues. Strictly used for troubleshooting purposes.
+ Bridge mode: bridge together the WLAN and the wired infrastructure together.
+ Sensor mode: this is a special mode which is not listed in the books but you need to know. In this mode, the device can actually function much like a WLAN client would associating and identifying client connectivity issues within the network in real time without requiring an IT or technician to be on site.
Although Monitor and Rogue detector mode can detect rough APs but they do not handle data so they are not correct.
Rogue Detection
A rogue is essentially any device that shares your spectrum, but is not in your control. This includes rogue Access Points, wireless router, rogue clients, and rogue ad-hoc networks. The Cisco UWN uses a number of methods to detect Wi-Fi-based rogue devices such as off-channel scanning and dedicated monitor mode capabilities. Cisco Spectrum Expert can also be used to identify rogue devices not based on the 802.11 protocol, such as Bluetooth bridges.
Off-Channel Scanning
This operation is performed by Local and Flex-Connect (in connected mode) mode APs and utilizes a time-slicing technique which allows client service and channel scanning with the usage of the same radio.
Question 52
Refer to the exhibit.

An engineer configures a new HSRP group. While reviewing the HSRP status, the engineer sees the logging message generated on R2. Which is the cause of the message?
A. A PC is on the network using the IP address 10.10.1.1
B. The HSRP configuration has caused a spanning-tree loop
C. The HSRP configuration has caused a routing loop
D. The same virtual IP address has been configured for two HSRP groups
Answer: D
Explanation
These messages specifically indicate that the router received a data packet that was sourced from the MAC addresses 0000.0c07.ac28, which is different from the MAC address of our HSRP group (0000.0c07.ac32). We also notice that 0000.0c07.ac28 is the virtual MAC address of another HSRP group (group 40 in particular; as 28 in hexadecimal equals to 40 in decimal).
Note: If the source MAC address of the error message is the same as our HSRP MAC address then the most likely cause is STP loop as our router received its own packet back.
Question 53
Refer to the exhibit. A network engineer troubleshoots an issue with the port channel between SW1 and SW2. Which command resolves the issue?
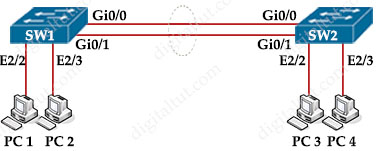
| *Aug 12 02:22:23.233: %LINK-3-UPDOWN: Interface Port-channel10, changed state to down *Aug 12 02:22:24.236: %LINEPROTO-5-UPDOWN: Line protocol on Interface Port-channel10,changed state to down *Aug 12 02:22:27.237: %ETC-5-L3DONTBNDL2: Gi0/1 suspended: LACP currently not enabled on the remote port *Aug 12 02:22:29.233: %ETC-5-L3DONTBNDL2: Gi0/0 suspended: LACP currently not enabled on the remote port |
A. SW1(config-if)#channel-group 10 mode active
B. SW1(config-if)#channel-group 10 mode desirable
C. SW2(config-if)#channel-group 10 mode on
D. SW2(config-if)#switchport mode trunk
Answer: A
Question 54
Which new enhancement was implemented in Wi-Fi 6?
A. Wi-Fi Protected Access 3
B. 4096 Quadrature Amplitude Modulation Mode
C. Uplink and Downlink Orthogonal Frequency Division Multiple Access
D. Channel bonding
Answer: C
Explanation
Wi-Fi 6 brings several crucial wireless enhancements for IT administrators when compared to Wi-Fi 5. The first significant change is using 2.4 GHz. Wi-Fi 5 was limited to only using 5 GHz. While 5 GHz is a ‘cleaner’ band of RF, it doesn’t penetrate walls and 2.4 GHz and requires more battery life. For Wi-Fi driven IoT devices, 2.4 GHz will likely continue to be the band of choice for the foreseeable future.
Another critical difference between the two standards is the use of Orthogonal Frequency Division Multiple Access (OFDMA) and MU-MIMO. Wi-Fi 5 was limited to downlink only on MU-MIMO, where Wi-Fi 6 includes downlink and uplink. OFDMA, as referenced above, is also only available in Wi-Fi 6.
Reference: https://www.extremenetworks.com/wifi6/what-is-80211ax/
Question 55
How is MSDP used to interconnect multiple PIM-SM domains?
A. MSDP depends on BGP or multiprotocol BGP for interdomain operation
B. MSDP allows a rendezvous point to dynamically discover active sources outside of its domain
C. MSDP SA request messages are used to request a list of active sources for a specific group
D. MSDP messages are used to advertise active sources in a domain
Answer: B
Explanation
Benefits of Using MSDP to Interconnect Multiple PIM-SM Domains
+ Allows a rendezvous points (RP) to dynamically discover active sources outside of its domain. -> Answer B is correct
+ Introduces a more manageable approach for building multicast distribution trees between multiple domains.
Reference: https://www.cisco.com/c/en/us/td/docs/ios/12_4t/ip_mcast/configuration/guide/mctmsdp.html#wp1054452
SA response messages are sent by the MSDP peer in response to an SA request message. SA response messages contain the IP address of the originating RP and one or more (S, G) pairs of the active sources in the originating RP’s domain that are stored in the cache -> Answer D is not correct as it should be “SA response messages are used to advertise active sources in a domain” (not MSDP messages).
In fact, answer A is also correct according to this link: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/ipmulti_pim/configuration/xe-16/imc-pim-xe-16-book/imc-msdp-im-pim-sim.html
“MSDP depends on BGP or multiprotocol BGP (MBGP) for interdomain operation. We recommended that you run MSDP on RPs sending to global multicast groups.”
But we think answer C is the better choice because it answers the question “How is MSDP used …”.
Note:
After a large PIM-SM network is divided into multiple PIM-SM domains, a mechanism is required to enable user hosts in a PIM-SM domain to receive multicast data from sources in another PIM-SM domain.
Multicast Source Discovery Protocol (MSDP) provides such a mechanism. It interconnects multiple PIM-SM domains to implement inter-domain multicast. RPs in PIM-SM domains set up MSDP peer relationships. By sending Source Active (SA) messages, the MSDP peers send the (S, G) information from the RP to which the source registers to the RPs in another PIM-SM domain.
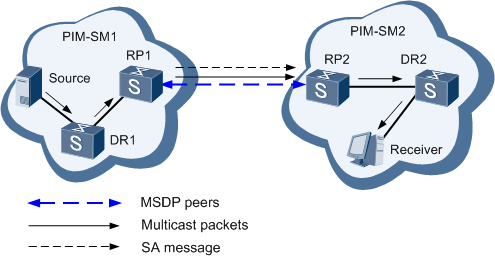
Reference: https://support.huawei.com/enterprise/en/doc/EDOC1000027471?section=j009
Note: A benefit of using MSDP to interconnect multiple PIM-SM domains is to allow a rendezvous point (RP) to dynamically discover active sources outside of its domain.
Question 56
Drag and drop the characteristics from the left onto the routing protocols they describe on the right.
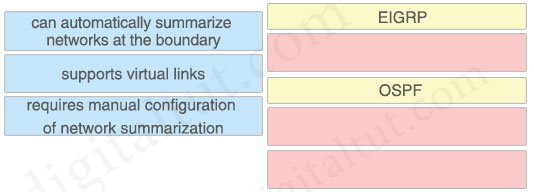
Answer:
EIGRP
+ can automatically summarize networks at the boundary
OSPF
+ supports virtual links
+ requires manual configuration of network summarization
Explanation
Unlike OSPF where we can summarize only on ABR or ASBR, in EIGRP we can summarize anywhere.
Manual summarization can be applied anywhere in EIGRP domain, on every router, on every interface via the ip summary-address eigrp as-number address mask [administrative-distance ] command (for example: ip summary-address eigrp 1 192.168.16.0 255.255.248.0). Summary route will exist in routing table as long as at least one more specific route will exist. If the last specific route will disappear, summary route also will fade out. The metric used by EIGRP manual summary route is the minimum metric of the specific routes.
Question 57
Drag and drop the characteristics from the left onto the protocols they apply to on the right.
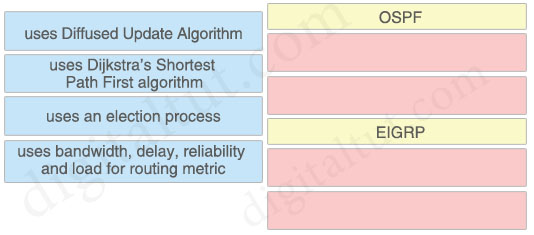
Answer:
OSPF
+ uses Dijkstra’s Shortest Path First algorithm
+ uses an election process
EIGRP
+ uses Diffused Update Algorithm
+ uses bandwidth, delay, reliability and load for routing metric
Question 58
How is 802.11 traffic handled in a fabric-enabled SSID?
A. converted by the AP into 802.3 and encapsulated into a VLAN
B. centrally switched back to WLC where the user traffic is mapped to a VXLAN on the WLC
C. centrally switched back to WLC where the user traffic is mapped to a VLAN on the WLC
D. converted by the AP into 802.3 and encapsulated into VXLAN
Answer: D
Explanation
For a fabric-enabled SSID, the AP converts 802.11 traffic to 802.3 and encapsulates it into VXLAN, encoding the VNI and SGT information of the client.
Question 59
Drag and drop the wireless elements on the left to their definitions on the right.
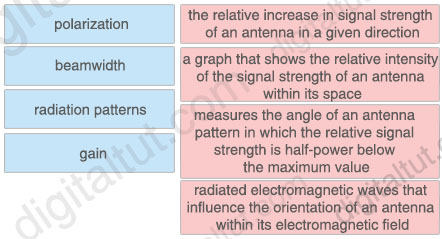
Answer:
+ the relative increase in signal strength of an antenna in a given direction: gain
+ a graph that shows the relative intensity of the signal strength of an antenna within its space: radiation patterns
+ measures the angle of an antenna pattern in which the relative signal strength is half-power below the maximum value: beamwidth
+ radiated electromagnetic waves that influence the orientation of an antenna within its electromagnetic field: polarization
Explanation
Beamwidth
The angle, in degrees, between the two half-power points (-3 dB) of an antenna beam, where more than 90% of the energy is radiated.

A radiation pattern defines the variation of the power radiated by an antenna as a function of the direction away from the antenna.
Polarization describes the way the electric field of the radio wave is oriented.
Antenna gain is the ability of the antenna to radiate more or less in any direction compared to a theoretical antenna.
Question 60
Refer to the exhibit.
R1 interface Ethernet0/0 ip address 10.1.1.10 255.255.255.0 ip nat inside ! interface Serial0/0 ip address 209.165.201.1 255.255.255.224 ip nat outside ! ip nat pool Busi 209.165.201.1 209.165.201.2 netmask 255.255.255.252 ip nat inside source list 1 pool Busi ! access-list permit 10.1.1.0 0.0.0.255 ! R1#show ip nat statistics Total active translations: 1 (0 static, 1 dynamic, 0 extended) Outside Interfaces: Inside Interfaces: Ethernet0/0 Hits: 119 Misses: 1 Expired translations: 0 Dynamic mappings: -- Inside Source access-list 1 pool Busi refcount 1 pool fred: netmask 255.255.255.252 start 209.165.201.1 end 209.165.201.2 type generic, total addresses 2, allocated 1 (50%), misses 0
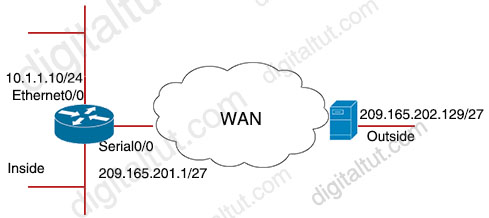
A network engineer configures NAT on R1 and enters the show command to verify the configuration. What does the output confirm?
A. R1 is configured with NAT overload parameters
B. The first packet triggered NAT to add on entry to NAT table
C. A Telnet from 160.1.1.1 to 10.1.1.10 has been initiated
D. R1 to configured with PAT overload parameters
Answer: B
Question 61
Which congestion queuing method on Cisco IOS based routers uses four static queues?
A. low latency
B. custom
C. weighted fair
D. Priority
Answer: D
Explanation
Priority Queuing (PQ): This type of queuing places traffic into one of four queues. Each queue has a different level of priority, and higher-priority queues must be emptied before packets are emptied from lower-priority queues. This behavior can “starve out” lower- priority traffic.
Question 62
What does the Cisco DNA REST response indicate?
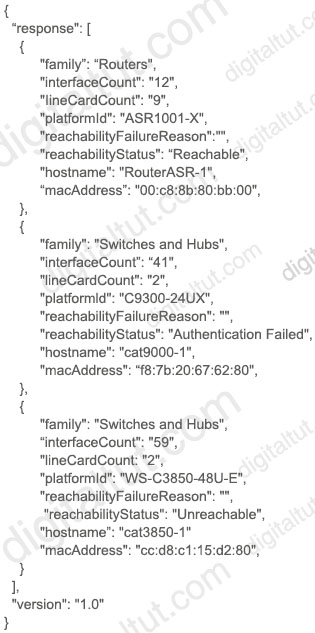
A. Cisco DNA Center has the incorrect credentials for cat9000-1
B. Cisco DNA Center is unable to communicate with cat9000-1
C. Cisco DNA Center has the incorrect credentials for RouterASR-1
D. Cisco DNA Center has the incorrect credentials for cat3850-1
Answer: A
Explanation
From the output, we see the following facts from top to bottom:
+ ASR1001 is reachable
+ Cat9000 (C9300) has the incorrect credentials
+ Cat3850 is unreachable
Question 63
Which AP mode allows an engineer to scan configured channels for rogue access points?
A. local
B. sniffer
C. bridge
D. monitor
Answer: D
Question 64
Where is radio resource management performed in a Cisco SD-access wireless solution?
A. control plane node
B. DNA Center
C. Cisco CMX
D. wireless controller
Answer: D
Explanation
WLC is still responsible for: AP image/config, Radio Resource Management (RRM) and client session management and roaming.
Reference: https://www.ciscolive.com/c/dam/r/ciscolive/latam/docs/2018/pdf/BRKEWN-2020.pdf
Question 65
Refer to the exhibit.
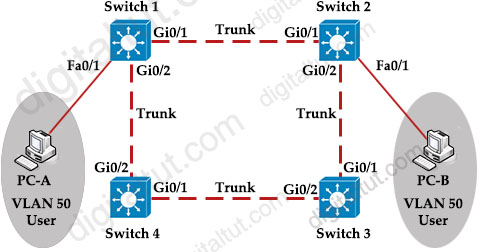
Rapid PVST+ is enabled on all switches. Which command set must be configured on Switch1 to achieve the following results on port fa0/1?
+ When a device is connected, the port transitions immediately to a forwarding state
+ The interface should not send or receive BPDUs.
+ If a BPDU is received, it continues operating normally.
A.
Switch1(config)# interface f0/1
Switch1(config-if)# spanning-tree portfast
Switch1(config-if)# spanning-tree bpduguard enable
B.
Switch1(config)# spanning-tree portfast bpduguard default
Switch1(config)# interface f0/1
Switch1(config-if)# spanning-tree portfast
C.
Switch1(config)#interface f0/1
Switch1(config-if)# spanning-tree portfast
D.
Switch1(config)#spanning-tree portfast bpdufilter default
Switch1(config)# interface f0/1
Switch1(config-if)# spanning-tree portfast
Answer: D
Explanation
BPDU Guard feature allows STP to shut an access port in the event of receiving a BPDU and put that port into err-disabled state so it is not the answer we want here.
BPDUFilter is designed to suppress the sending and receiving of BPDUs on an interface. If a BPDU is received on a Port Fast-enabled interface, the interface loses its Port Fast-operational status, and BPDU filtering is disabled -> BPDUFilter is the answer we want.
There are two ways to configure BPDU filtering feature, one in global configuration mode and one under a specific interface:
Configuring BPDU filter globally:
Switch(config)#spanning-tree portfast bpdufilter default
Configure BPDU Filter on the interface:
Switch(config-if)#spanning-tree bpdufilter enable (this overrides the global bpdufilter command above)
But the effect of these two commands are different and you should remember:
+ When BPDU filtering is enabled globally; and if BPDUs are seen, the port loses its PortFast status, BPDU filtering is disabled, the port returns to normal state
+ When BPDU filtering is enabled on a specific port, it prevents this port from sending or receiving BPDUs (so if BPDUs are seen, they will be dropped)
Question 66
Refer to the exhibit.
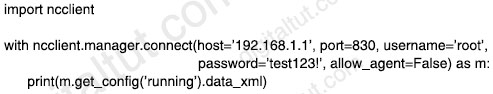
After running the code in the exhibit. Which step reduces the amount of data that NETCONF server returns to the NETCONF client, to only the interface’s configuration?
A. Create an XML filter as a string and pass it to get_config() method as an argument
B. Use the txml library to parse the data returned by the NETCONF server for the interface’s configuration
C. Create a JSON filter as a string and pass it to the get_config() method as an argument
D. Use the JSON library to parse the data returned by the NETCONF server for the interface’s configuration
Answer: A
Explanation
Sometimes we are only interested in a very particular part of the config. NETCONF accomodates this with the ability to specify a filter. In below script, we will specify a filter that only shows the information for interface GigabitEthernet3. The get_config also accepts a filter parameter (documentation). So in below script, we will simply pass that filter to the get_config method and see what happens.
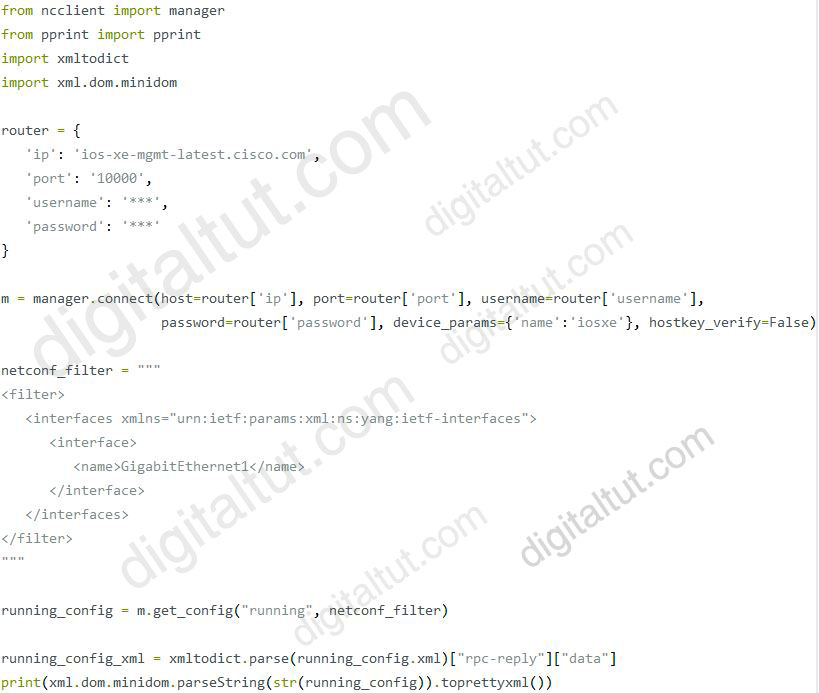
Reference: https://blog.wimwauters.com/networkprogrammability/2020-03-30-netconf_python_part1/
Question 67
A network engineer configures BGP between R1 and R2. Both routers use BGP peer group CORP and are set up to use MD5 authentication. This message is logged to the console of router R1:
| *Jun 5 33:34:33.033: %TCP-6-BADAUTH: Invalid MD5 digest from 10.10.10.1 (29832) to 10.120.10.1 (179) tableid -0 |
Which two configurations allow a peering session to form between R1 and R2? (Choose two)
A.
R2(config-router)#neighbor 10.10.10.1 peer-group CORP
R2(config-router)#neighbor CORP password Cisco
B.
R2(config-router)#neighbor 10.10.10.1 peer-group CORP
R2(config-router)#neighbor PEER password Cisco
C.
R1(config-router)#neighbor 10.10.10.1 peer-group CORP
R1(config-router)#neighbor CORP password Cisco
D.
R1(config-router)#neighbor 10.120.10.1 peer-group CORP
R1(config-router)#neighbor CORP password Cisco
E.
R2(config-router)#neighbor 10.120.10.1 peer-group CORP
R2(config-router)#neighbor CORP password Cisco
Answer: C E
Explanation
The above message (“…Invalid MD5 digest from 10.10.10.1 (29832) to 10.120.10.1…”) was received on R1 so we can deduce the IP address of R1 is 10.120.10.1 and the IP address of R2 is 10.10.10.1. Therefore on R1 we have to configure “neighbor 10.10.10.1 …” while on R2 we have to use “neighbor 10.120.10.1 …”
Question 68
Which device makes the decision for a wireless client to roam?
A. wireless client
B. access point
C. wireless LAN controller
D. WCS location server
Answer: A
Explanation
Roaming is a client side decision in 802.11 WiFi. Client devices listen for beacon frames or send probe requests to discover APs advertising the preferred SSID. The clients driver uses the received signal strength of beacons or probe responses to make decisions on whether to change APs or remain connected to the current AP.
Question 69
Refer to the exhibit.
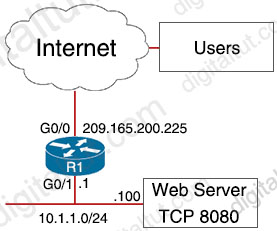
External users require HTTP connectivity to an internal company web server that is listening on TCP port 8080. Which command set accomplishes this requirement?
|
Option A interface G0/0 |
Option B interface G0/0 interface G0/1 ip nat inside source static tcp 209.165.200.225 80 10.1.1.100 8080 |
|
Option C interface G0/0 interface G0/1 ip nat inside source static tcp 10.1.1.1 8080 209.166.200.225 80 |
Option D interface G0/0 interface G0/1 ip nat inside source static tcp 10.1.1.100 8080 interface G0/0 80 |
|
Option E interface G0/0 interface G0/1 ip nat inside source static tcp 209.165.200.225 8080 10.1.1.100 8080 |
A. Option A
B. Option B
C. Option C
D. Option D
E. Option E
Answer: D
Explanation
We need:
+ G0/0: NAT outside
+ G0/1: NAT inside
-> Only Option D & Option E are correct
We need to configure local-ip before global-ip in the command ip nat inside source static local-ip global-ip so only Option D is correct.
Question 70
Which three elements determine Air Time efficiency? (Choose three)
A. evert-driven RRM
B. data rate (modulation density) or QAM
C. channel bandwidth
D. number of spatial streams and spatial reuse
E. RF group leader
F. dynamic channel assignment
Answer: B C D
Explanation
Four things determine Air Time Efficiency
1. Data rate (Modulation density) orQAM -(how many Bit’s per Radio Symbol) 64 QAM is more robust but 1024 QAM is a lot faster
2. Number of spatial streams and spatial reuse (introduction of OFDMA and Resource Units) and UL/DL MU-MIMO
3. Channel bandwidth –How Many frequencies can we modulate at one time
4. Protocol overhead –Preamble/Ack/BA, Guard Interval “GI” etc.
Reference: https://www.ciscolive.com/c/dam/r/ciscolive/emea/docs/2020/pdf/BRKEWN-3010.pdf
Question 71
Which features does Cisco EDR use to provide threat detection and response protection?
A. containment, threat intelligence, and machine learning
B. firewalling and intrusion prevention
C. container-based agents
D. cloud analysis and endpoint firewall controls
Answer: A
Explanation
In addition to continuous file analysis, it is important to note that an EDR is only as good at detecting files as the cyber threat intelligence that powers it. Cyber threat intelligence leverages large-scale data, machine learning capabilities, and advanced file analysis to help detect threats. The greater the cyber threat intelligence, the more likely it is your EDR solution will identify the threat. Without any cyber threat intelligence, an EDR solution is ineffective.
After detecting a malicious file, an EDR solution must be able to contain the threat. Malicious files aim to infect as many processes, applications, and users as possible. Segmentation can be a great defense within your data center to avoid lateral movement of advanced threats. Segmentation is helpful, but a proper EDR solution can help contain a malicious file before testing the edges of segmented areas of the network. Ransomware is a tremendous example of why you need to contain threats. Ransomware can be tricky to remove. Once it has encrypted information, your EDR needs to be able to fully contain ransomware to mitigate the damages.
Question 72
Refer to the exhibit.
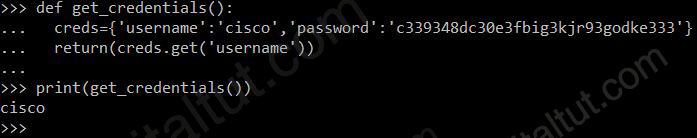
def get_credentials():
creds={'username':'cisco','password':'c339348dc30e3fbig3kjr93godke333'}
return(creds.get('username'))
print(get_credentials())
What is the output of this code?
A. username: Cisco
B. get_credentials
C. username
D. cisco
Answer: D
Explanation
“creds” is Dictionary type in Python so we can use the method “get” to get the value of an item.
Question 73
Which two threats does AMP4E have the ability to block? (Choose two)
A. DDoS
B. ransomware
C. SQL injection
D. Microsoft Word macro attack
E. email phishing
Answer: B D
Explanation
+ Advanced Malware Protection for Endpoints (AMP4E): provides malware protection on endpoints
Question 74
Refer to the exhibit.
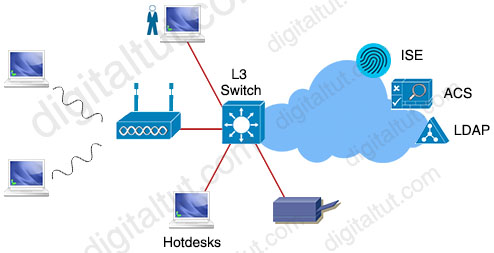
Which single security feature is recommended to provide Network Access Control in the enterprise?
A. 802.1X
B. MAB
C. WebAuth
D. port security sticky MAC
Answer: A
Question 75
Refer to the exhibit.
%OSPF-5-ADJCHG: Process 1, Nbr 10.0.0.2 on FastEthernet0/0 from FULL to DOWN, Neighbor Down: Interface down or detached %OSPF-6-AREACHG: 10.0.0.1/32 changed from area 0 to area 1 %OSPF-4-ERRRCV: Received invalid packet: mismatch area ID, from backbone area must be virtual-link but not found from 10.0.0.2, FastEthernet0/0
What is the cause of the log messages?
A. OSPF area change
B. hello packet mismatch
C. MTU mismatch
D. IP address mismatch
Answer: A
Question 76
What are two benefits of virtual switching when compared to hardware switching? (Choose two)
A. increased MTU size
B. hardware independence
C. VM-level isolation
D. increased flexibility
E. extended 802.1Q VLAN range
Answer: C D
Explanation
Virtual switches have benefits as well as virtual machines attached to them. They boost security by leveraging isolation, control and content inspection methods between virtual machines, which helps deter inter-switch link attacks. Moreover, with virtual switches, network administrators can control them with a hypervisor. Additionally, virtual switches can help with the migration of virtual machines across physical hosts by eliminating the need to reconfigure each virtual machine. They can also enhance operational efficiency, improve communications and scale system bandwidth capacity.
Reference: https://www.rcrwireless.com/20180328/fundamentals/physical-switches-vs-virtual-switches
Question 77
What are two characteristics of VXLAN? (Choose two)
A. It uses VTEPs to encapsulate and decapsulate frames.
B. It has a 12-bit network identifier
C. It extends Layer 2 and Layer 3 overlay networks over a Layer 2 underlay.
D. It lacks support for host mobility
E. It allows for up to 16 million VXLAN segments
Answer: A E
Explanation
VXLAN has a 24-bit VXLAN network identifier (VNI), which allows for up to 16 million (= 224) VXLAN segments to coexist within the same infrastructure. This surely solve the small number of traditional VLANs -> The first problem of VLAN has been resolved.
VTEPs connect between Overlay and Underlay network and they are responsible for encapsulating frame into VXLAN packets to send across IP network (Underlay) then decapsulating when the packets leaves the VXLAN tunnel.
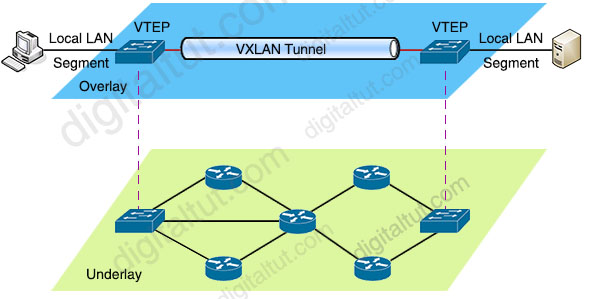
VXLAN is a virtual overlay network which runs on the top of a physical underlay network. The underlay network may use any Layer 3 routing protocol like OSPF, EIGRP, IS-IS… to route packets so no Spanning Tree Protocol is required -> One of the major benefits of VXLAN technology is that it allows creating virtual Layer 2 segments over Layer 3 routed networks. Therefore answer C is not correct because “It extends Layer 2 and Layer 3 overlay networks over a Layer 3 underlay” (not Layer 2 underlay).
Question 78
Refer to the exhibit.
Router# traceroute 10.10.10.1 Type escape sequence to abort. Tracing the route to 10.10.10.1 1 10.0.0.1 5 msec 5 msec 5 msec 2 10.5.0.1 15 msec 17 msec 17 msec 3 10.10.10.1 * * *
An engineer is troubleshooting a connectivity issue and executes a traceoute. What does the result confirm?
A. The destination server reported it is too busy
B. The probe timed out
C. The destination port is unreachable
D. The protocol is unreachable
Answer: B
Explanation
In Cisco routers, the codes for a traceroute command reply are:
! — success
* — time out
N — network unreachable
H — host unreachable
P — protocol unreachable
A — admin denied
Q — source quench received (congestion)
? — unknown (any other ICMP message)
Reference: https://www.cisco.com/c/en/us/support/docs/ip/ip-routed-protocols/22826-traceroute.html
Question 79
Refer to the exhibit.
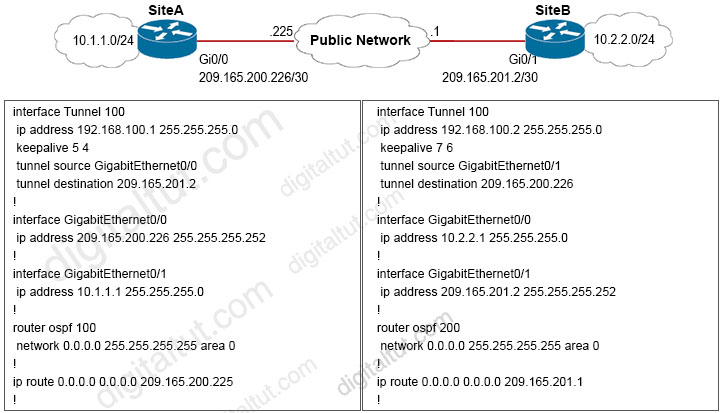
A network engineer configures a new GRE tunnel and enters the show run command. What does the output verify?
A. The tunnel keepalive is configured incorrectly because they must match on both sites
B. The tunnel destination will be known via the tunnel interface
C. The tunnel will be established and work as expected
D. The default MTU of the tunnel interface is 1500 byte.
Answer: B
Explanation
GRE keepalive packets may be sent from both sides of a tunnel or from just one side. If they are sent from both sides, the period and retry parameters can be different at each side of the link -> Answer A is not correct.
Tunnel interfaces by default will have 1476 bytes MTU. 24 bytes less the physical -> Answer D is not correct.
In this question, we turned on OSPF on all active interfaces (with the “network 0.0.0.0 255.255.255.255 area 0” command). So on SiteB the tunnel interface (192.168.100.2) is also running OSPF. When SiteA receives the OSPF advertisement from SiteB, it realizes it can reach the other side of the tunnel via OSPF (and it would not use the default route any more). In other words, it reaches the tunnel destination through the tunnel itself -> This causes “recursive routing” error.
Note: In order to avoid this error, do not advertise the tunnel destination IP address on the tunnel interface to other side.
Good recursive routing reference: https://networklessons.com/cisco/ccie-routing-switching/gre-tunnel-recursive-routing-error
Question 80
Refer to the exhibit.
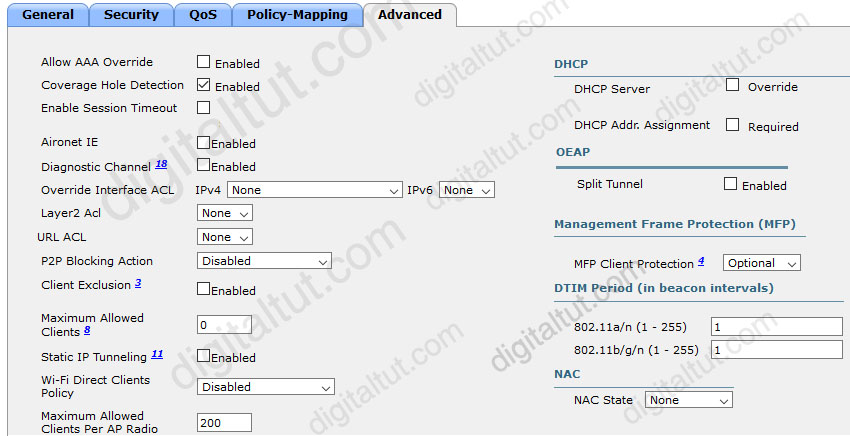
An engineer has configured Cisco ISE to assign VLANs to clients based on their method of authentication, but this is not working as expected. Which action will resolve this issue?
A. require a DHCP address assignment
B. utilize RADIUS profiling
C. set a NAC state
D. enable AAA override
Answer: D
Explanation
Dynamic VLAN assignment is one such feature that places a wireless user into a specific VLAN based on the credentials supplied by the user. This task of assigning users to a specific VLAN is handled by a RADIUS authentication server, such as Cisco ISE. This can be used, for example, to allow the wireless host to remain on the same VLAN as it moves within a campus network.
…
In order to accomplish dynamic VLAN assignment with WLCs based on ISE to AD group mapping, these steps must be performed:
+ ISE to AD integration and configuration of authentication and authorization policies for users on ISE
+ WLC configuration to support dot1x authentication and AAA override for correspondent SSID
+ End client supplicant configuration
Question 81
What is the function of a VTEP in VXLAN?
A. provide the routing underlay and overlay for VXLAN headers
B. dynamically discover the location of end hosts in a VXLAN fabric
C. encapsulate and de-encapsulate traffic into and out of the VXLAN fabric
D. statically point to end host locations of the VXLAN fabric
Answer: C
===================== New Questions (added on 15th-Jun-2021) =====================
Question 82
If the noise floor is -90 dBm and the wireless client is receiving a signal of -75 dBm, what is the SNR?
A. -165
B. 83
C. 15
D. 1.2
Answer: C
Explanation
If your SNR measurements are already in decibel form, then you can subtract the noise quantity from the desired signal: SNR = S – N. This is because when you subtract logarithms, it is the equivalent of dividing normal numbers. Also, the difference in the numbers equals the SNR. In this question, SNR = -75 – (-90) = 15.
Question 83
Drag and drop the snippets onto the blanks within the code to construct a script that advertises the network prefix 192.168.5.0 session. Not all options are used.

Answer: 1-A; 2-C;3-B
=========================== New Questions (added on 27th-Jun-2021) ===========================
Question 84
How does an on-premises infrastructure compare to a cloud infrastructure?
A. On-premises can increase compute power faster than cloud
B. On-premises offers faster deployment than cloud
C. On-premises offers lower latency for physically adjacent systems than cloud
D. On-premises requires less power and cooling resources than cloud
Answer: C
Question 85
Which design principle states that a user has no access by default to any resource, and unless a resource is explicitly granted, it should be denied?
A. complete mediation
B. least privilege
C. economy of mechanism
D. fail-safe defaults
Answer: D
Explanation
The Principle of Fail-Safe Defaults states that, unless a subject is given explicit access to an object, it should be denied access to that object.
Note: By the principle of least privilege, that administrator should only be able to access the subjects and objects involved in mail queueing and delivery. As we saw, this minimizes the threats if that administrator’s account is compromised. The mail system can be damaged or destroyed, but nothing else can be.
Reference: https://us-cert.cisa.gov/bsi/articles/knowledge/principles/failing-securely
Question 86
Refer to the exhibit.
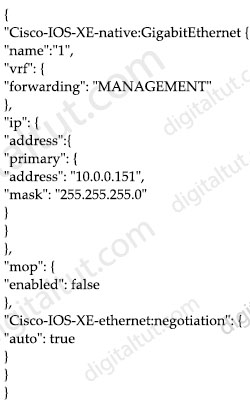
Drag and drop the snippets into the RESTCONF request to form the request that returns this response. Not all options are used.
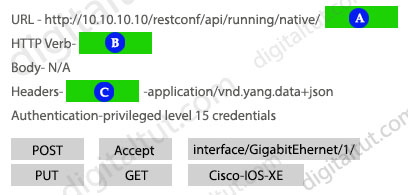
Answer:
1 – interface/GigabitEthernet/1/
2 – GET
3 – Accept
Question 87
Refer to the exhibit.
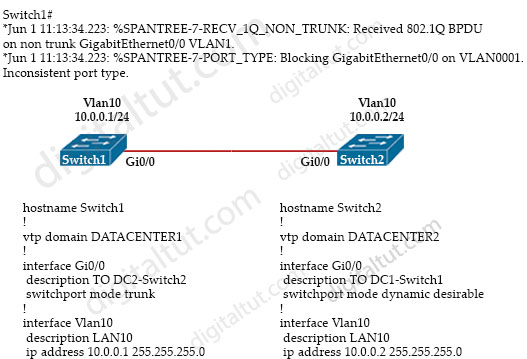
An engineer implemented several configuration changes and receives the logging message on Switch1. Which action should the engineer take to resolve this issue?
A. Change Switch1 to switch port mode dynamic desirable
B. Change Switch2 to switch port mode dynamic auto
C. Change Switch1 to switch port mode dynamic auto
D. Change the VTP domain to match on both switches
Answer: D
Explanation
We can configure “switchport mode trunk” and “switchport mode dynamic desirable” on two ends with no problem. But trunking can be configured only when the ports belong to the same VTP domain.
=========================== New Questions (added on 10th-Jul-2021) ===========================
Question 88
Refer to the exhibit.
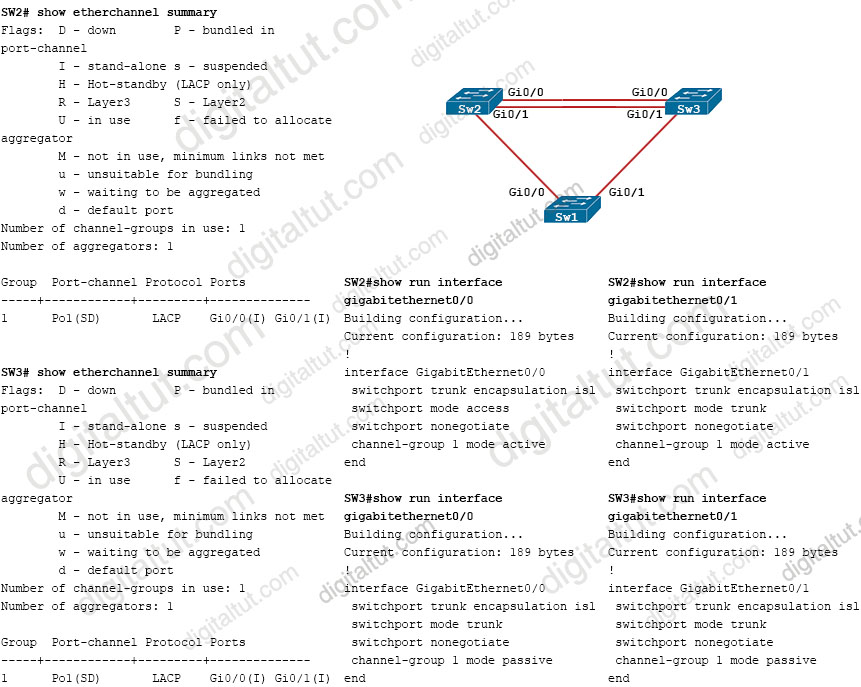
The EtherChannel between SW2 and SW3 is not operational. Which action resolves this issue?
A. Configure the channel-group mode on SW2 Gi0/1 and Gi0/1 to on
B. Configure the channel-group mode on SW3 Gi0/1 to active
C. Configure the mode on SW2 Gi0/0 to trunk
D. Configure the mode on SW2 Gi0/1 to access
Answer: C
Explanation
From the output of “show run interface gigabitethernet0/0” of SW2, we see interface G0/0 is in access mode so we have to change to trunk mode to match with the configuration of G0/1 interface of SW2.
Question 89
A network administrator applies the following configuration to an IOS device. What is the process of password checks when a login attempt is made to the device?
| aaa new-model aaa authentication login default local group tacacs+ |
A. A TACACS+server is checked first. If that check fail, a database is checked.
B. A TACACS+server is checked first. If that check fail, a RADIUS server is checked. If that check fail, a local database is checked.
C. A local database is checked first. If that fails, a TACACS+server is checked, if that check fails, a RADIUS server is checked.
D. A local database is checked first. If that check fails, a TACACS+server is checked.
Answer: D
Explanation
“aaa authentication login” specifies that you want to use authentication. You need to give the authentication parameters a list name, either default or some other name you define:
| aaa authentication login {default | list-name} group {group-name | radius | tacacs+} [method 2…3…4] |
+ The ‘default’ means we want to apply for all login connections (such as tty, vty, console and aux). If we use this keyword, we don’t need to configure anything else under tty, vty and aux lines. If we don’t use this keyword then we have to specify which line(s) we want to apply the authentication feature.
+ The ‘local group tacacs+” means all users are authenticated using router’s local database first and then if required, TACACS server is tried.
Question 90
Refer to the exhibit.
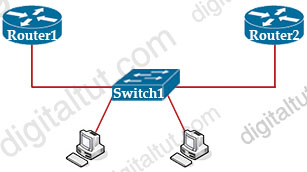
Router 1 is currently operating as the HSRP primary with a priority of 110. Router1 fails and Router2 take over the forwarding role. Which command on Router1 causes it to take over the forwarding role when it return to service?
A. standby 2 priority
B. standby 2 preempt
C. standby 2 track
D. standby 2 timers
Answer: B
Question 91
Drag and drop packet switching architecture from the left onto the correct positions on the right.
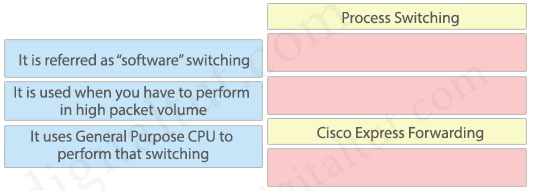
Answer:
Process Switching:
+ It is referred as “software” switching
+ It uses General Purpose CPU to perform that switching
Cisco Express Forwarding:
+ It is used when you have to perform in high packet volume
Question 92
Refer to the exhibit.
Switch1# show interfaces trunk ! Output omitted for brevity Port Mode Encapsulation Status Native Gi1/0/20 auto 802.1q trunking 10 Port Vlans allowed on trunk Gi1/0/20 1-4094 Switch2# show interfaces trunk ! Output omitted for brevity Port Mode Encapsulation Status Native Gi1/0/20 auto 802.1q trunking 10 Port Vlans allowed on trunk Gi1/0/20 1-4094
The trunk does not work over the back-to-back link between Switch1 interface Gig1/0/20 and Switch2 interface Gig1/0/20. Which configuration fixes the problem?
A. Switch2(config)#interface gig1/0/20
Switch2(config-if)#switchport mode dynamic desirable
B. Switch1(config)#interface gig1/0/20
Switch1(config-if)#switchport mode dynamic auto
C. Switch2(config)#interface gig1/0/20
Switch2(config-if)#switchport mode dynamic auto
D. Switch2(config)#interface gig1/0/20
Switch1(config-if)#switchport trunk native vlan 1
Switch2(config)#interface gig1/0/20
Switch2(config-if)#switchport trunk native vlan 1
Answer: A
Explanation
From the output, we learn that both interfaces are in “auto” mode so they cannot establish a trunk. We have to change one (or both) of them to “desirable” mode.
Question 93
What is the function of vBond in a Cisco SDWAN deployment?
A. onboarding of SDWAN routers into the SD-WAN overlay
B. pushing of configuration toward SD-WAN routers
C. initiating connections with SD-WAN routers automatically
D. gathering telemetry data from SD-WAN routers
Answer: A
Explanation
Orchestration plane (vBond) assists in securely onboarding the SD-WAN WAN Edge routers into the SD-WAN overlay. The vBond controller, or orchestrator, authenticates and authorizes the SD-WAN components onto the network. The vBond orchestrator takes an added responsibility to distribute the list of vSmart and vManage controller information to the WAN Edge routers. vBond is the only device in SD-WAN that requires a public IP address as it is the first point of contact and authentication for all SD-WAN components to join the SD-WAN fabric. All other components need to know the vBond IP or DNS information.
=========================== New Questions (added on 3rd-Aug-2021) ===========================
Question 94
What is the difference in dBm when an AP power increases from 25 mW to 100mW?
A. 75dBm
B. 150dBm
C. 6dBm
D. 125dBm
Answer: C
Explanation
Formula to convert from mW to dBm:
P(dBm) = 10log10(mW)
Therefore:
+ 25mW converts to dBm: 10log10(25)= 13.98dBm
+ 100mW converts to dBm: 10log10(100) = 20dBm
The difference between them is about 6dBm.
Or a shorter way from the formula:
logAB – logAC = logA(B/C)
Then 10log10(100) – 10log10(25) = 10log10(100/25) = 10log10(4) = 6.02
Question 95
Which free application make REST call against DNA center?
A. Postman
B. Ansible
C. Chef
D. Puppet
Answer: A
======================= New Questions (added on 11th-Aug-2021) =======================
Question 96
A network engineer must configure a router to send logging messages to a syslog server based on these requirements:
uses syslog IP address: 10.10.10.1
uses a reliable protocol
must not use any well-known TCP/UDP ports
Which configuration must be used?
A. logging host 10.10.10.1 transport udp port 1024
B. logging origin-id 10.10.10.1
C. logging host 10.10.10.1 transport udp port 1023
D. logging host 10.10.10.1 transport tcp port 1024
Answer: D
Question 97
Drag and drop the characteristics from the left onto the routing protocols they describe on the right.
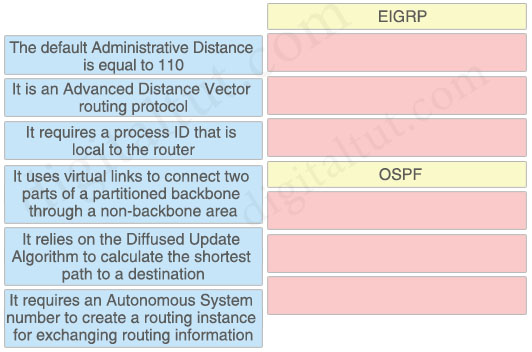
Answer:
EIGRP
+ It is an Advanced Distance Vector routing protocol
+ It relies on the Diffused Update Algorithm to calculate the shortest path to a destination
+ It requires an Autonomous System number to create a routing instance for exchanging routing information
OSPF
+ The default Administrative Distance is equal to 110
+ It requires a process ID that is local to the router
+ It uses virtual links to connect two parts of a partitioned backbone through a non-backbone area
======================= New Questions (added on 16th-Aug-2021) =======================
Question 98
Refer to the exhibit.
psswd = (base64.b64decode(‘SzFwM001RzchCg==’). decode(‘utf-8’)).strip(‘/n’) d = datetime.date.today() date = str(10000*d.year + 100*d.month + d.day)
Refer to the exhibit. Which result does the python code achieve?
A. The code converts time to the yyyymmdd representation
B. The code encrypts a base64 decrypted password
C. The code converts time to the “year/month/day” time format
D. The code converts time to the Epoch LINUX time format
Answer: A
Explanation
There are two results in the code above:
+ The first result is in the first line with “psswd” variable. The purpose of this line is to decrypt (not encrypt) an encrypted base64 string -> Answer B is not correct.
+ The second result is in the last line with “date” variable. Let’s take an example with the date 16th-Aug-2021 to see how the “date” variable is calculated:
date = 10000 * 2021 + 100 * 8 + 16 = 20210000 + 800 + 16 = 20210816 -> Therefore the date is in yyyymmdd format.

Question 99
Refer to the exhibit. Which command is required to verify NETCONF capability reply messages?
A. show netconf | section rpc-reply
B. show netconf rpc-reply
C. show netconf xml rpc-reply
D. show netconf schema | section rpc-reply
Answer: D
Explanation
The output of the show netconf schema command displays the element structure for a NETCONF request and the resulting reply. This schema can be used to construct proper NETCONF requests and parse the resulting replies.
We tested this command under IOS-XE v16.05.01b and this is the result:

Other commands are not correct: