NetFlow Tutorial
One of the most important tasks of a network administrator is to monitor the health of our networks, learn how our bandwidth is being used, what applications are consuming it, when it needs upgrade… Although monitoring protocols like SNMP and SPAN (port mirroring) can help us answer some questions but they are not enough to give us an insightful view of our networks. Luckily we have another amazing tool: NetFlow!
NetFlow is a networking analysis protocol that gives the ability to collect detailed information about network traffic as it flows through a router interface. NetFlow helps network administrators answers the questions of who (users), what (application), when (time of day), where (source and destination IP addresses) and how network traffic is flowing.
Let’s take an example! In the topology below, when traffic from Network 1, 2, 3… passes through the interfaces of a NetFlow enabled device, relevant information is captured and stored in the NetFlow cache. NetFlow collects IP traffic information as records and sends them to a NetFlow collector for traffic flow analysis.
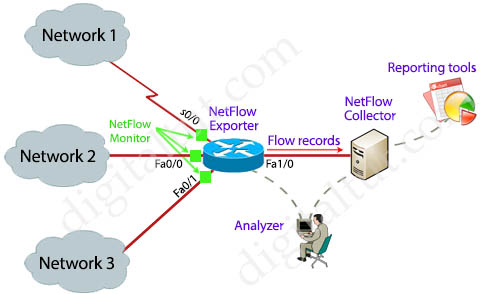
NetFlow components
+ NetFlow Monitor: a component applied to an interface and collects information about flows. Flow monitors consist of a record and a cache. You add the record to the flow monitor after the flow monitor is created. In the topology above, we can apply the NetFlow Monitors to the s0/0, Fa0/0 and Fa0/1 interfaces of the router to collect traffic information of these interfaces
+ NetFlow Exporter: aggregates packets into flows, stores IP flow information in its NetFlow cache and exports them in the form of flow records to the NetFlow collector
+ NetFlow Collector: collects flow records sent from the NetFlow exporters, parsing and storing the flows. Usually a collector is a separate software running on a network server. NetFlow records are exported to a NetFlow collector using User Datagram Protocol (UDP)
+ NetFlow Sampler: used to reduce the number of packets that are selected for analysis. It is applied to a NetFlow Monitor to reduce the overhead load because the number of packets that the flow monitor must analyze is reduced. But notice that the accuracy of the information stored in the flow monitor’s cache is also reduced correspondingly.
| Note: The term “flows” here should be understood as “unidirectional streams of related packets” |
The most important component of NetFlow is the NetFlow Exporter (and its NetFlow cache) so we will discuss more about it.
How NetFlow Exporter works
When packets arrive at the NetFlow Exporter, each of them is inspected for one or many IP packet attributes. These attributes are used to determine if the packet is unique or similar to other packets. If it is similar then it is classified as in the same flow.
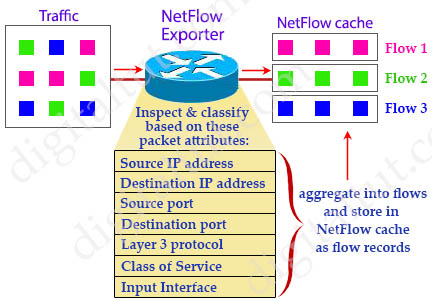
There are seven key IP packet attributes that can be used by NetFlow to classify packets into separate flows:
+ IP source address
+ IP destination address
+ Source port
+ Destination port
+ Layer 3 protocol type
+ Class of Service (or Type of Service – ToS) Byte
+ Input (Router or switch) interface
Other attributes can be also used and they are called non-key attributes such as timestamps, packet and byte counters, TCP flag information…
After inspecting these attributes, the NetFlow Exporter condenses them into flow records and save in a database called the NetFlow cache. These flow records can also be exported to a NetFlow Collector.
How to view NetFlow data
There are two main methods to view NetFlow data:
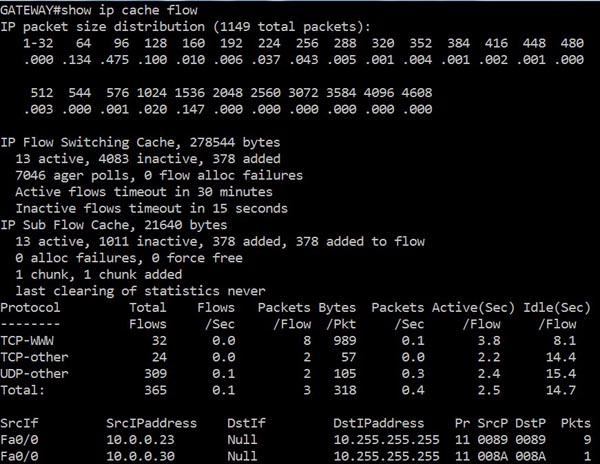
+ Command Line Interface (CLI): Because the NetFlow cache is a part of the NetFlow Exporter so we can view this cache directly via the Command-Line-Interface (CLI), which is very useful for troubleshooting, with the “show ip cache flow” command. An example output of this command is shown below:
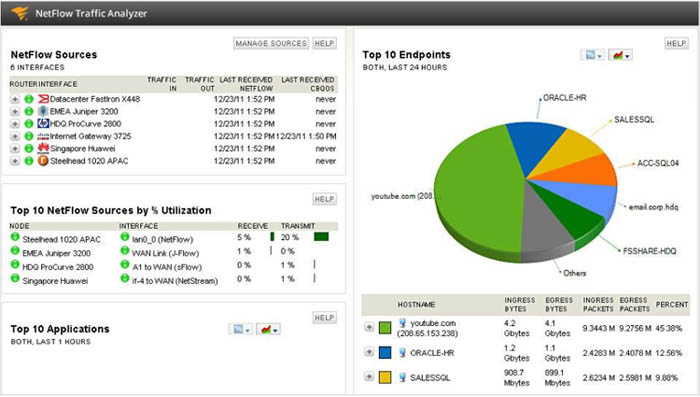
+ A NetFlow reporting tool: there are many tools that can collect NetFlow packets sent to the NetFlow Collector and display a comprehensive view. Below is an example of what SolarWinds NetFlow Traffic Analyzer can analyze:
NetFlow versions
Version 1: the original format supported in the initial NetFlow releases.
Versions 2, 3 and 4 were not released.
Version 5: an enhancement that adds Border Gateway Protocol (BGP) autonomous system information, flow sequence numbers and a few additional fields. This is the standard and most common NetFlow version. Only support IPv4.
Version 6: similar to version 7
Version 7: Cisco-specific version for Catalyst 5000 series switches but not compatible with Cisco routers
Version 8: choice of aggregation schemes in order to reduce resource usage
Version 9: support flow-record format and it is known as Flexible NetFlow technology. NetFlow version 9 includes a template to describe what is being exported. It supports extensible file export format to enable easier support. It also supports additional fields & technologies such as MPLS, IPv6, IPSec, NBAR protocols, Multicast, VLAN ID…
In general, the two most important NetFlow versions are Version 5 and Version 9 which we will learn how to configure them.
| Note: NetFlow version 5 only supports monitoring inbound statistics using the “ip flow ingress” command while NetFlow v9 allows to monitor traffic leaving each interface via “ip flow egress” command. |
In the next part we will learn how to configure NetFlow version 5 & 9.



lucky
Again, another fantastic explanation & example. Thank You
Hey, does ENCOR has LABs or only the testlets?
interface FastEthernet0/0
to enable flow need additional configuration as shown below:
ip flow monitor Tut_Monitor input
ip flow monitor Tut_Monitor output
ip flow ingress
ip flow egress
ip flow-top-talker
sort bytes
top 5
interface FastEthernet0/0
!!! to enable flow need additional configuration as shown below:
ip flow monitor Tut_Monitor input
ip flow monitor Tut_Monitor output
ip flow ingress
ip flow egress
ip flow-top-talker
sort bytes
top 5
https://community.cisco.com/t5/switching/net-flow-quot-ip-flow-route-cache-flow-quot/td-p/1982382
where to get latest VCE for 350-401?