IPv6 Questions 2
Question 1
Question 2
Question 3
Explanation
Address Family Translation (AFT) using NAT64 technology can be achieved by either stateless or stateful means:
+ Stateless NAT64 is a translation mechanism for algorithmically mapping IPv6 addresses to IPv4 addresses, and IPv4 addresses to IPv6 addresses. Like NAT44, it does not maintain any bindings or session state while performing translation, and it supports both IPv6-initiated and IPv4-initiated communications.
+ Stateful NAT64 is a stateful translation mechanism for translating IPv6 addresses to IPv4 addresses, and IPv4 addresses to IPv6 addresses. Like NAT44, it is called stateful because it creates or modifies bindings or session state while performing translation. It supports both IPv6-initiated and IPv4-initiated communications using static or manual mappings.
Question 4
Question 5
Explanation
When a change is made to one of the IP header fields in the IPv6 pseudo-header checksum (such as one of the IP addresses), the checksum field in the transport layer header may become invalid. Fortunately, an incremental change in the area covered by the Internet standard checksum [RFC1071] will result in a well-defined change to the checksum value [RFC1624]. So, a checksum change caused by modifying part of the area covered by the checksum can be corrected by making a complementary change to a different 16-bit field covered by the same checksum.
Reference: https://tools.ietf.org/html/rfc6296
Question 6
Question 7
Explanation
Link-local addresses are always configured with the FE80::/64 prefix. Most routing protocols use the link-local address for a next-hop.
Question 8
Explanation
A link-local address is an IPv6 unicast address that can be automatically configured on any interface using the link-local prefix FE80::/10 (1111 1110 10) and the interface identifier in the modified EUI-64 format. Link-local addresses are not necessarily bound to the MAC address (configured in a EUI-64 format). Link-local addresses can also be manually configured in the FE80::/10 format using the ipv6 address link-local command.
Reference: http://www.cisco.com/c/en/us/support/docs/ip/ip-version-6-ipv6/113328-ipv6-lla.html
Question 9
Explanation
Stateless Address Auto Configuration (SLAAC) is a method in which the host or router interface is assigned a 64-bit prefix, and then the last 64 bits of its address are derived by the host or router with help of EUI-64 process.
Question 10
Question 11
Explanation
The components of IPv6 header is shown below:
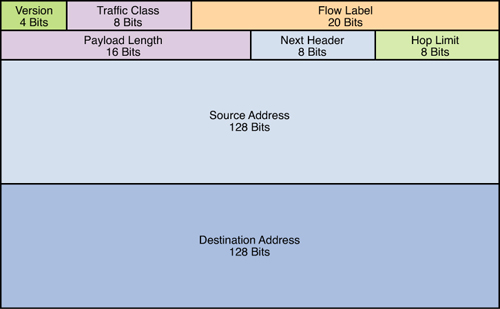
The Traffic Class field (8 bits) is where quality of service (QoS) marking for Layer 3 can be identified. In a nutshell, the higher the value of this field, the more important the packet. Your Cisco routers (and some switches) can be configured to read this value and send a high-priority packet sooner than other lower ones during times of congestion. This is very important for some applications, especially VoIP.
The Flow Label field (20 bits) is originally created for giving real-time applications special service. The flow label when set to a non-zero value now serves as a hint to routers and switches with multiple outbound paths that these packets should stay on the same path so that they will not be reordered. It has further been suggested that the flow label be used to help detect spoofed packets.
The Hop Limit field (8 bits) is similar to the Time to Live field in the IPv4 packet header. The value of the Hop Limit field specifies the maximum number of routers that an IPv6 packet can pass through before the packet is considered invalid. Each router decrements the value by one. Because no checksum is in the IPv6 header, the router can decrease the value without needing to recalculate the checksum, which saves processing resources.



Hello, Question 11. What’s the correct answer?
BCE or ACD.
@DigitalTut, I need to resolv this.
question no 11 is correct answer is A,C,D
HI
Q11 correct is BCE. To filter packets in a ACL you won’t use hop limit or traffic class but flow label and IPv6 source and destination addresses.
I struggled to grasp #9 for a bit. Yes, SLAAC/EUI-64 is an answer, but why isn’t DHCPv6, I wondered. In the end, I think it’s because of the wording of “with default settings on all interfaces”. Therefore, even though the DHCPv6 pool(named dhcp-pool) is shown as being configured, it is not applied to any interface with the “ipv6 dhcp server dhcp-pool” command. Leaving only SLAAC/EUI-64 as a way to configure the client.
The explanation on this page does not elaborate on why SLAAC/EUI-64 is the answer in this case, it only explains a little about how SLAAC/EUI-64 work. Am I mistaken?
“Q11 correct is BCE. To filter packets in a ACL you won’t use hop limit or traffic class but flow label and IPv6 source and destination addresses.” — cl
I agree with this(BCE). if you try creating an ipv6 ACL, of course source and destination are always able to be specified. beyond that, I found that flow-label is supported and there is no option for hop limit or traffic class.
R1(config-ipv6-acl)#deny ipv6 host 1111::1 host 2222::2 ?
auth Match on authentication header
dest-option Destination Option header (all types)
dscp Match packets with given dscp value
flow-label Flow label
fragments Check non-initial fragments
hbh Match on hop-by-hop option
log Log matches against this entry
log-input Log matches against this entry, including input
mobility Mobility header (all types)
mobility-type Mobility header with type
routing Routing header (all types)
routing-type Routing header with type
sequence Sequence number for this entry
time-range Specify a time-range
undetermined-transport Transport cannot be determined or is missing
Hi friends, I have the valid dump with me and I’m wiling to share. Please contact me via durshen81 @ gmail .com
Confirming the 539q dumps are valid.
Passed, if you go the exam study the 21q dumps.
Confirming the 21q dumps are valid.
@BreakerOfChains Had the same question. I think you are correct.
please I need questions (digitaltut) . I do not see question
Q2:
search for: NAt64 over NAT-PT
https://www.cisco.com/c/en/us/products/collateral/ios-nx-os-software/enterprise-ipv6-solution/white_paper_c11-676278.html
Q11
I do believe the correct answers are really A C D. Let’s think about it:
Destination address – what for? Destination add. is the add. of enterprise’s WAN link which is under attack.
Source address – We can’t just block a source ip address in a DDoS attack since the packets do not come from only one source.
Q11
Is correct as is.
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_data_acl/configuration/xe-3s/sec-data-acl-xe-3s-book/ip6-acls-xe.html
The following header fields are used for IPv6 inspection: traffic class, flow label, payload length, next header, hop limit, and source or destination IP address. For further information on and descriptions of the IPv6 header fields, see RFC 2474.
SUMMARY STEPS
1. enable
2. configure terminal
3. ipv6 access-list access-list-name
4. Do one of the following:
permit protocol {source-ipv6-prefix/prefix-length | any | host source-ipv6-address} [operator [port-number]] {destination-ipv6-prefix / prefix-length | any | host destination-ipv6-address} [operator [port-number]] [dest-option-type [doh-number | doh-type]] [dscp value] [flow-label value] [fragments] [log] [log-input] [mobility] [mobility-type [mh-number | mh-type]] [routing] [routing-type routing-number] [sequence value] [time-range name]
Q11 is trying to differentiate between IPv4 with IPv6. The answers are corrects.
Possible the configuration in Q9 is shown for confusing only. EUI-64 is not a addressing mechanisms itself. It is just an unique ID, just part of a whole process.
“The three typical strategies for IPv6 automated address assignment are:
SLAAC: Clients self-address with no ready centralized tracking or management. No means to pass options (like DNS server) to clients that don’t support RFC 6106.
Stateless DHCP: Use SLAAC for addresses, but pick up options from a DHCP server.
Stateful DHCP: Manage addresses leases and options from central server, just like IPv4 DHCP.”
Maybe answer is B, C, but I’m not sure.
hi Marcus,
Could you please provide the link for your explanation.
Its good explanation.
I accept your explanation.
as MDLT said
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_data_acl/configuration/xe-3s/sec-data-acl-xe-3s-book/ip6-acls-xe.html
Q11:
The following header fields are used for IPv6 inspection: traffic class, flow label, payload length, next header, hop limit, and source or destination IP address.
but since the question is specifically mention ipv6, so I will say the answer A,C,D is correct. rather than B,C,E, because ipv4 also can use B,C,E
Hi, @unstoppable. I found it there:
https://blogs.cisco.com/enterprise/ipv6-automatic-addressing
thanks Marcus, you are great!
Q4 isnt answer is wrong?
Router A and Router B are configured with IPv6 addressing and basic routing capabilities using OSPFv3. The networks that are advertised from Router A do not show up in Router B’s routing table. After debugging IPv6 packets, the message “not a router” is found in the output. Why is the routing information not being learned by Router B?
it says answer is D. But, in the question it is said that basic routing capabilities using OSPFv3 is configured which means some routing commands have been made. However, it is absolutely impossible to make routing configurations without entering at first #ipv6 unicast-routing. Can someone please clarify this question. Thank you
Q11
http://www.infosectoday.com/Articles/Basic_IPv6_Security_Considerations.htm
Q9:
“(config-if)#ipv6 address 2001::/64 ?
anycast Configure as an anycast
eui-64 Use eui-64 interface identifier
”
One can use eui-64 in combination with a statically defined prefix. Thus I think answers A and B are correct.
Which two functions are completely independent when implementing NAT64 over NAT-PT?
(Choose two.)
A. DNS
B. NAT
C. port redirection
D. stateless translation
E. session handling
can someone explain why it’s A&B for this question ?
Treyon: explication for Q2 is in link added by Digitaltut at Question 3
“NAT-PT has been deemed deprecated by IETF because of its tight coupling with Domain Name System (DNS). ….
Network Address Translation IPv6 to IPv4, or NAT64, technology facilitates communication between IPv6-only and IPv4-only hosts and networks (whether in a transit, an access, or an edge network). This solution allows both enterprises and ISPs to accelerate IPv6 adoption while simultaneously handling IPv4 address depletion. The DNS64 and NAT64 functions are completely separated, which is essential to the superiority of NAT64 over NAT-PT. “
MDLT very good reference to ipv6 inspection but did not explain why not source and destination address(fragment offset is not case for ipv6).
Reason is what MDLT said and type of attack (denial of service: that mean it try to shutdown a service). Traffic Class and Flow Label is referred to data flows and that can be link to specific service. Regarding Hop Limit i don’t known. In wiki is written “Hop Limit (8 bits)
Replaces the time to live field of IPv4. This value is decremented by one at each forwarding node and packet discarded if it becomes 0. However destination node should process the packet normally even if hop limit becomes 0.” Only explanation that come is denial of services to CPU (control plane of Route Processor), trying to increase CPU
Q9 A and B are correct answers. Those are “two dynamic IPv6 addressing mechanisms could you use on end hosts to provide end-to-end connectivity”. Using EUI-64, host call interface address and using SLACC call ipv6 prefix and prefix-length.
C is WRONG. Why? because create ipv6 dhcp pool dhcp-pool is not enough for DHCPv6 stateless (stateful is not the case if you look to pool definition -lack of address-prefix-)
So, for DHCPv6 is need to configure something on interface
(config-if)=ipv6 nd other-config-flag
(config-if)=ipv6 dhcp server dhcp-pool
By contrary, in question is written “If IPv6 is configured with default settings on all interfaces on the router”.
So, digitaltut answer is just perfect
Q11: This is what makes Cisco exams so frustrating, they could have easily just asked “What fields are found in an IPv6 header and not in an IPv4 header?”, instead of “The enterprise network WAN link has been receiving several denial of service attacks from both IPv4 and IPv6 sources. Which three elements can you use to identify an IPv6 packet via its header, in order to filter future attacks? (Choose three)”, I feel that any router worth its salt could tell the difference between an IPv6 address (128 bit length) and an IPv4 address (32 bit length).