Drag Drop Questions
Question 1
Explanation
OSPF metric is only dependent on the interface bandwidth & reference bandwidth while EIGRP metric is dependent on bandwidth and delay by default.
Both OSPF and EIGRP have three tables to operate: neighbor table (store information about OSPF/EIGRP neighbors), topology table (store topology structure of the network) and routing table (store the best routes).
Question 2
Question 3
Explanation
The following diagram illustrates the key difference between traffic policing and traffic shaping. Traffic policing propagates bursts. When the traffic rate reaches the configured maximum rate (or committed information rate), excess traffic is dropped (or remarked). The result is an output rate that appears as a saw-tooth with crests and troughs. In contrast to policing, traffic shaping retains excess packets in a queue and then schedules the excess for later transmission over increments of time. The result of traffic shaping is a smoothed packet output rate.
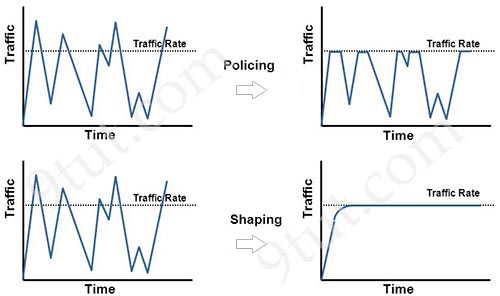
Note: Committed information rate (CIR): The minimum guaranteed data transfer rate agreed to by the routing device.
Question 4
Explanation
ITR is the function that maps the destination EID to a destination RLOC and then encapsulates the original packet with an additional header that has the source IP address of the ITR RLOC and the destination IP address of the RLOC of an Egress Tunnel Router (ETR). After the encapsulation, the original packet become a LISP packet.
ETR is the function that receives LISP encapsulated packets, decapsulates them and forwards to its local EIDs. This function also requires EID-to-RLOC mappings so we need to point out an “map-server” IP address and the key (password) for authentication.
A LISP proxy ETR (PETR) implements ETR functions on behalf of non-LISP sites. A PETR is typically used when a LISP site needs to send traffic to non-LISP sites but the LISP site is connected through a service provider that does not accept nonroutable EIDs as packet sources. PETRs act just like ETRs but for EIDs that send traffic to destinations at non-LISP sites.
Map Server (MS) processes the registration of authentication keys and EID-to-RLOC mappings. ETRs sends periodic Map-Register messages to all its configured Map Servers.
Map Resolver (MR): a LISP component which accepts LISP Encapsulated Map Requests, typically from an ITR, quickly determines whether or not the destination IP address is part of the EID namespace
Question 5
Explanation
Unlike OSPF where we can summarize only on ABR or ASBR, in EIGRP we can summarize anywhere.
Manual summarization can be applied anywhere in EIGRP domain, on every router, on every interface via the ip summary-address eigrp as-number address mask [administrative-distance ] command (for example: ip summary-address eigrp 1 192.168.16.0 255.255.248.0). Summary route will exist in routing table as long as at least one more specific route will exist. If the last specific route will disappear, summary route also will fade out. The metric used by EIGRP manual summary route is the minimum metric of the specific routes.
Question 6
Explanation
When Secure Vault is not in use, all information stored in its container is encrypted. When a user wants to use the files and notes stored within the app, they have to first decrypt the database. This happens by filling in a previously determined Security Lock – which could be a PIN or a password of the user’s choosing.
When a user leaves the app, it automatically encrypts everything again. This way all data stored in Secure Vault is decrypted only while a user is actively using the app. In all other instances, it remains locked to any attacker, malware or spyware trying to access the data.
How token-based authentication works: Users log in to a system and – once authenticated – are provided with a token to access other services without having to enter their username and password multiple times. In short, token-based authentication adds a second layer of security to application, network, or service access.
OAuth is an open standard for authorization used by many APIs and modern applications. The simplest example of OAuth is when you go to log onto a website and it offers one or more opportunities to log on using another website’s/service’s logon. You then click on the button linked to the other website, the other website authenticates you, and the website you were originally connecting to logs you on itself afterward using permission gained from the second website.
Question 7
Explanation
To attach a policy map to an input interface, a virtual circuit (VC), an output interface, or a VC that will be used as the service policy for the interface or VC, use the service-policy command in the appropriate configuration mode.
Class of Service (CoS) is a 3 bit field within an Ethernet frame header when we use 802.1q which supports virtual LANs on an Ethernet network. This field specifies a priority value which is between 0 and 63 inclusive which can be used in the Quality of Service (QoS) to differentiate traffic.
The Differentiated Services Code Point (DSCP) is a 6-bit field in the IP header for the classification of packets. Differentiated Services is a technique which is used to classify and manage network traffic and it helps to provide QoS for modern Internet networks. It can provide services to all kinds of networks.
Traffic policing is also known as rate limiting as it propagates bursts. When the traffic rate reaches the configured maximum rate (or committed information rate), excess traffic is dropped (or remarked). The result is an output rate that appears as a saw-tooth with crests and troughs.
Traffic shaping retains excess packets in a queue and then schedules the excess for later transmission over increments of time -> It causes delay.
Question 8
Question 9
Question 10
Explanation
+ StealthWatch: performs security analytics by collecting network flows via NetFlow
+ ESA: email security solution which protects against email threats like ransomware, business email compromise, phishing, whaling, and many other email-driven attacks
+ AMP for Endpoints (AMP4E): provides malware protection on endpoints
+ Umbrella: provides DNS protection by blocking malicious destinations using DNS
+ Firepower Threat Defense (FTD): provides a comprehensive suite of security features such as firewall capabilities, monitoring, alerts, Intrusion Detection System (IDS) and Intrusion Prevention System (IPS).



@admin
D&D for Qos is not working in Composite Quizzes.
please take a look.
@david: Thanks for your detection! We have just updated the Composite Quizzes.
Q1 is wrong.
OSPF metric is based on BW, not delay and reliability. That answer should be dragged to the EIGRP part (EIGRP metric is based on BW, delay, reliability, load and MTU).
And OSPF maintains 3 tables: neighbor, topology and routing table.
Agree
Q1
OSPF – 2,5,6
EIGRP – 1,3,4
On the QoS drag and drop Question 3, if Shaping typically has delays shouldn’t it also introduce delay and jitter?
is it the eigrp should be based on bandwidth and delay by default ? not reliability ?
@japanese: Yes, we also noticed it in the explanation but there is no better choice so we had to pick it.
Q8 D&D – Cloud : which sequence is correct please.
Pay…, Very Scalable…, Physical location
or
Pay.., Physical location…, Very Scable…
Q6.
Seems like wrong, because:
Oauth = through identity provider
Proof: https://www.ciscolive.com/c/dam/r/ciscolive/emea/docs/2018/pdf/DEVNET-3613.pdf (just see page 12).
HTTP basic authentication — username and password in an encoded string
token-based authentication — API-dependent secret
secure vault — public API resource
OAuth — authorization through identity provider
Reference: https://www.ciscolive.com/c/dam/r/ciscolive/emea/docs/2018/pdf/DEVNET-3613.pdf
@ldnl
Yes, this is exact it!
@digitaltut
Please help to update question 6.
Dear All,
Please someone share the latest dumps at (suffianmanzoor at gmail dot com).
many thanks in advance.
Question 10, Umbrella should be provides DNS protection. Cisco bought OpenDNS and then rebranded it as Umbrella. We use Umbrella where I work and it has integration with the Meraki firewalls where the Meraki Firewalls hijack any outgoing DNS requests and pass them to Umbrella. (this is a beta feature we enabled.) Anyways. I’m 100 percent confident Umbrella is DNS protection
QoS drag and drop. Should it be??:
Traffic Policing:
-drop excessive traffic
-causes TCP retransmissions when traffic is dropped
-introduces no delays and jitter
Traffic Shaping
-buffers excessive traffic
-typically delays, rather than drops traffic
-introduces delays and jitter
Hi , So taken the exam & passed. 60% same Q and the rest are very close to current Q but . difference will be in the wording . lots of new automation Q .
thanks for your help good website, but you do not have testing simulator like certkingdom thank to them also
thank you
Hi,
I have a question. Are the practical labs in the exam ?
Best regards
Hans