Access List
Question 1
Explanation
The first answer is not correct because the 10.0.0.0 network range is not correct. It should be 10.0.0.0. to 10.255.255.255.
Question 2
Explanation
Logging-enabled access control lists (ACLs) provide insight into traffic as it traverses the network or is dropped by network devices. Unfortunately, ACL logging can be CPU intensive and can negatively affect other functions of the network device. There are two primary factors that contribute to the CPU load increase from ACL logging: process switching of packets that match log-enabled access control entries (ACEs) and the generation and transmission of log messages.
Process switching is the slowest switching methods (compared to fast switching and Cisco Express Forwarding) because it must find a destination in the routing table. Process switching must also construct a new Layer 2 frame header for every packet. With process switching, when a packet comes in, the scheduler calls a process that examines the routing table, determines which interface the packet should be switched to and then switches the packet. The problem is, this happens for the every packet.
Reference: http://www.cisco.com/web/about/security/intelligence/acl-logging.html
Question 3
Explanation
If you use the “debug ip packet” command on a production router, you can bring it down since it generates an output for every packet and the output can be extensive. The best way to limit the output of debug ip packet is to create an access-list that linked to the debug. Only packets that match the access-list criteria will be subject to debug ip packet. For example, this is how to monitor traffic from 1.1.1.1 to 2.2.2.2
| access-list 100 permit ip 1.1.1.1 2.2.2.2 debug ip packet 100 |
Note: The “debug ip packet” command is used to monitor packets that are processed by the routers routing engine and are not fast switched.
Question 4
Question 5
Question 6
Explanation
+ The question asks to “always” block traffic (every week) so we must use keyword “periodic”.
+ Traffic should be blocked to 11:59 PM, which means 23:59
Note: The time is specified in 24-hour time (hh:mm), where the hours range from 0 to 23 and the minutes range from 0 to 59
Only answer B satisfies these two requirements so it is the best answer. In fact, all the above answers are not correct as the access-list should deny web traffic, not allow them as shown in the answers.
Question 7
Question 8
Question 9
Explanation
The established keyword is only applicable to TCP access list entries to match TCP segments that have the ACK and/or RST control bit set (regardless of the source and destination ports), which assumes that a TCP connection has already been established in one direction only. Let’s see an example below:
 Suppose you only want to allow the hosts inside your company to telnet to an outside server but not vice versa, you can simply use an “established” access-list like this:
Suppose you only want to allow the hosts inside your company to telnet to an outside server but not vice versa, you can simply use an “established” access-list like this:
| access-list 100 permit tcp any any established access-list 101 permit tcp any any eq telnet ! interface S0/0 ip access-group 100 in ip access-group 101 out |
Note:
Suppose host A wants to start communicating with host B using TCP. Before they can send real data, a three-way handshake must be established first. Let’s see how this process takes place:
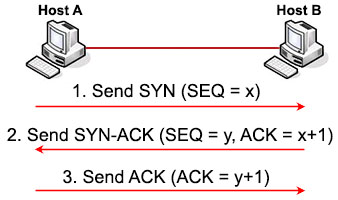
1. First host A will send a SYN message (a TCP segment with SYN flag set to 1, SYN is short for SYNchronize) to indicate it wants to setup a connection with host B. This message includes a sequence (SEQ) number for tracking purpose. This sequence number can be any 32-bit number (range from 0 to 232) so we use “x” to represent it.
2. After receiving SYN message from host A, host B replies with SYN-ACK message (some books may call it “SYN/ACK” or “SYN, ACK” message. ACK is short for ACKnowledge). This message includes a SYN sequence number and an ACK number:
+ SYN sequence number (let’s called it “y”) is a random number and does not have any relationship with Host A’s SYN SEQ number.
+ ACK number is the next number of Host A’s SYN sequence number it received, so we represent it with “x+1”. It means “I received your part. Now send me the next part (x + 1)”.
The SYN-ACK message indicates host B accepts to talk to host A (via ACK part). And ask if host A still wants to talk to it as well (via SYN part).
3. After Host A received the SYN-ACK message from host B, it sends an ACK message with ACK number “y+1” to host B. This confirms host A still wants to talk to host B.
Question 10
Explanation
Reflexive access lists provide filtering on upper-layer IP protocol sessions. They contain temporary entries that are automatically created when a new IP session begins. They are nested within extended, named IP access lists that are applied to an interface. Reflexive access lists are typically configured on border routers, which pass traffic between an internal and external network. These are often firewall routers. Reflexive access lists do not end with an implicit deny statement because they are nested within an access list and the subsequent statements need to be examined.
Reference: http://www.cisco.com/en/US/docs/ios-xml/ios/sec_data_acl/configuration/15-1s/sec-access-list-ov.html
Question 11
Explanation
The command “ipv6 traffic-filter access-list-name { in | out }” applies the access list to incoming or outgoing traffic on the interface.
Question 12
Question 13
Explanation
When the ACL logging feature is configured, the system monitors ACL flows and logs dropped packets and statistics for each flow that matches the deny conditions of the ACL entry.
The log and log-input options apply to an individual ACE and cause packets that match the ACE to be logged. The sample below illustrates the initial message and periodic updates sent by an IOS device with a default configuration using the log ACE option.
*May 1 22:12:13.243: %SEC-6-IPACCESSLOGP: list ACL-IPv4-E0/0-IN permitted tcp 192.168.1.3(1024) -> 192.168.2.1(22), 1 packet
Reference: https://www.cisco.com/c/en/us/about/security-center/access-control-list-logging.html
From the example above we can see when an ACL drops a packet, it generates a level 6 Syslog (%SEC-6-)



Hi guys, can someone please send me the latest dumps jovce123 @ gmail .com
Thanks in advance
Hi guys, can someone please send me the latest dumps ezrading @ gmail .com
Is anyone really sending anything. If anyone can share rjshinigami @ gmail.com
Question 9. C or D ?
isn’t 149 be using “extended” ip access-list ?
Question 15.
B- shouldn’t it be deny instead ? why permit the port 80 traffic ?
“Question 15.
B- shouldn’t it be deny instead ? why permit the port 80 traffic ?” – Peter Pan
Exactly!!! Ultimately none of the ACLs are correct. The only relevant details in the answers that properly relate to the question are the “periodic” and “absolute” terms as well as the time ranges. If you just go off of that, then B makes sense.
@ Khal
yes, “periodic” and” 1.00 – 2359″ would make B the closest answer for the question.
Cheers
Hi Please Send me latest Dumps for CCNP route & CCNP Switch exam on–> agosavi99 @ gmail com
Hi everyone, I have the valid dump with me and I’m wiling to share. Please contact me via durshen81 @ gmail .com
Hi I am just wondering how can I see questions? Anyone can get me a hint.
Please reach to me via email {email not allowed} and show me how to see question on this page.
Thanks in advance.
where can we find the questions here?
Passed used the 21q dumps from IT-Libraries
Passed, it-libraries questions are still good. check the comments on this forum for the new questions since there are a couple of them posted here.
Thanks all, done with the router. 539q dumps from IT-Libraries are valid. Practice the labs since the ips change on the exam
Hi everyone, I have the valid dump with me and I’m wiling to share. Please contact me via durshen81 @ gmail .com
Hi everyone, I’m having the valid dump with me and I’m wiling to share. Please contact me via durshen81 @ gmail .com
Hello Team,
I would like to thank you for the advises and that you share your experience, I recently pass the route exam :D….
I study with the Official cert Kevin Wallace, CBT nuggets (nothing that you cannt find for your own in a torrent) and with this site.
I can say that I found a couple of new questions and a new Frame relay drag and drop that is not here:
SVC —— A circuit that provides temporary on-demand connections between DTEs
DLCI—— A locally significant ID
PVC ——-A logical connection comprising two endpoints and CIR
LMI ——- A signaling mechanism for frame relay devices
FECN—– An indicator of congestion on the network.
Please do not pay for dumps or believe in guys who post “new dump” or “I have the new dump”, or “I failed the exam”, those guys should be rape and kill!!!!!!
Anyway, hope you pass the exam and share your real experience for the other exams.
can you please send the valid dump to biruktil111@yahoo dotcom
can you send me working dumps please, {email not allowed}
Thanks all, done with the router. 440q dumps from IT-Libraries are valid. Practice the labs since the ips change on the exam
Can i get the dexter dumps please at pro6151945 at gmail dot com
Guaranteed Latest Stuff to pass exam.
HERE Instant DOWNLOAD
20 US$ only
Below link
https://docs.google.com/document/d/1afXgWBvIWTSr8R0Mt-kDRdMmFCI3ytfuSK-1vOyWov0/edit?usp=sharing
you can practice question here : http://chen-academy.com/edukn
Hey could someone please send me the latest dumps and/or the VCE player software to this email puppy_wuv15 @ Yahoo
Hi digitaltut team i am unable to access the composite questions kindly assist
@MissT: Please make sure you have installed latest Flash plugin at https://get.adobe.com/flashplayer and enable it on your web browser.
I think question 12 should be B. ipv6 access-list [access-list-name]. The question asked about enabling IPv6 ACL and it did not mention anything about the interface.
Hi, could someone please send me the latest Dumps of routing 300-101 PDF in to this email: {email not allowed}
email sugmados @ Yahoo Fr
@Elv,
The IPv6 neighbor discovery process uses the IPv6 network-layer service; therefore, to enable IPv6 neighbor discovery, you must add IPv6 ACLs to allow IPv6 neighbor discovery packets to be sent and received on an interface.
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_data_acl/configuration/xe-3s/sec-data-acl-xe-3s-book/ip6-acls-xe.html
Q2
In all software releases, the access-list-number can be 100 to 199. In Cisco IOS Software Release 12.0.1, extended ACLs begin to use additional numbers (2000 to 2699). These additional numbers are referred to as expanded IP ACLs. Cisco IOS Software Release 11.2 added the ability to use list name in extended ACLs.
https://www.cisco.com/c/en/us/support/docs/security/ios-firewall/23602-confaccesslists.html#extacls
should be Q4,
Thanks digitaltut.
Hi guys, can someone please send me the latest dumps devastante75 @Yahoo. com
10ks
Who can assist with a password access issue
Latest Update 100% Real CCNP Exam Questions
dumps
pro
dot
com
Guys For God sake please stop asking for dumps. This is the website. Use it and get prepare. PLEASE. Thanks
@digitaltut
question 10- The answer should be reflexive access
https://www.cisco.com/c/en/us/td/docs/ios/12_2/security/configuration/guide/fsecur_c/scfreflx.pdf
@cisconinja
Reflexive access lists provide the ability to filter network traffic at a router, based on IP upper-layer protocol “session” information.
Extended ACLs is the correct.
Hi All:
Can anybody send me latest dumps for CCNP_ROUTE at {email not allowed}
Thanks,
Can anybody send me latest dumps for CCNP_ROUTE at eng.sonjoy @ gmail . com
Passed, if you go the exam study the 440q dumps.
q12:
@Elv, have a good point but I think there is a keyword you are missing, as I did with this question.
The question is asking how to “Enable” an IPv6 ACL not “Create” the distinction is very easy to overlook.
Share a useful link, the content inside is true and effective.
http: //t.cn /RDVCyvH
@NANA Thank you for sharing, I have to prepare for the exam, I hope to pass.
why question 4 is not A and it is D ?
Can some one explain me
Can someone send latest to huntredt99 @ yahoo . com
@Fereshte@huntred
There is a lot of information inside, you can find all the information you want to know inside.