Access-list Questions 2
Question 1
Explanation
The established keyword is only applicable to TCP access list entries to match TCP segments that have the ACK and/or RST control bit set (regardless of the source and destination ports), which assumes that a TCP connection has already been established in one direction only. Let’s see an example below:
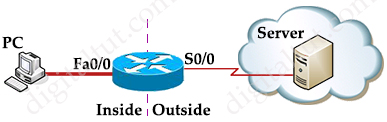 Suppose you only want to allow the hosts inside your company to telnet to an outside server but not vice versa, you can simply use an “established” access-list like this:
Suppose you only want to allow the hosts inside your company to telnet to an outside server but not vice versa, you can simply use an “established” access-list like this:
| access-list 100 permit tcp any any established access-list 101 permit tcp any any eq telnet ! interface S0/0 ip access-group 100 in ip access-group 101 out |
Note:
Suppose host A wants to start communicating with host B using TCP. Before they can send real data, a three-way handshake must be established first. Let’s see how this process takes place:
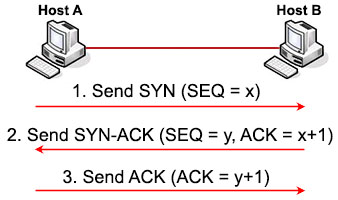
1. First host A will send a SYN message (a TCP segment with SYN flag set to 1, SYN is short for SYNchronize) to indicate it wants to setup a connection with host B. This message includes a sequence (SEQ) number for tracking purpose. This sequence number can be any 32-bit number (range from 0 to 232) so we use “x” to represent it.
2. After receiving SYN message from host A, host B replies with SYN-ACK message (some books may call it “SYN/ACK” or “SYN, ACK” message. ACK is short for ACKnowledge). This message includes a SYN sequence number and an ACK number:
+ SYN sequence number (let’s called it “y”) is a random number and does not have any relationship with Host A’s SYN SEQ number.
+ ACK number is the next number of Host A’s SYN sequence number it received, so we represent it with “x+1”. It means “I received your part. Now send me the next part (x + 1)”.
The SYN-ACK message indicates host B accepts to talk to host A (via ACK part). And ask if host A still wants to talk to it as well (via SYN part).
3. After Host A received the SYN-ACK message from host B, it sends an ACK message with ACK number “y+1” to host B. This confirms host A still wants to talk to host B.
Question 2



Answer should be Option A. Option B shows line vty 0 15, that is not matched with exabit, line vty 5 15
May I ask why is letter C not also the correct answer for Q1? The only difference is the access-list number used
ldnl – The access-list number determines if it is a standard or extended access-list. A standard access-list (1-99) does not support protocol based rules. You can only pick a source and destination address. Extended access lists allow this, and that is why it is correct. I hope that helps.
nhema – vty 0 15 includes all vty lines from the exhibit, so that is why it is the correct answer. Option A only includes the first 5 vty lines, and ignores the rest. That is why it is incorrect.
@idnl access-list 10 is not extended that’s why the correct answer is D.
Vty 0 -4 is on routers. vty 0-15 is on L3 switches. Why is option A wrong?
What’s the difference in C & D, but D is the answer? Nothing states it has to be an extended due to this? Why would C not be the answer or how is one to determine the difference based off the question and explaination?
Also is 10 and 110 the sequence or the actual ACL #?
@Q1 – Stupidity Here
Because 10 is a simple access-list (1-99) and you cannot use protocol and port numbers.
Router(config)#access-list 10 permit tcp any any eq 21 established
^
% Invalid input detected at ‘^’ marker.
Router(config)#
Extended access-lists (100-199) offer this possibility, so D is correct.