Access List
Question 1
Explanation
The first answer is not correct because the 10.0.0.0 network range is not correct. It should be 10.0.0.0. to 10.255.255.255.
Question 2
Explanation
Logging-enabled access control lists (ACLs) provide insight into traffic as it traverses the network or is dropped by network devices. Unfortunately, ACL logging can be CPU intensive and can negatively affect other functions of the network device. There are two primary factors that contribute to the CPU load increase from ACL logging: process switching of packets that match log-enabled access control entries (ACEs) and the generation and transmission of log messages.
Process switching is the slowest switching methods (compared to fast switching and Cisco Express Forwarding) because it must find a destination in the routing table. Process switching must also construct a new Layer 2 frame header for every packet. With process switching, when a packet comes in, the scheduler calls a process that examines the routing table, determines which interface the packet should be switched to and then switches the packet. The problem is, this happens for the every packet.
Reference: http://www.cisco.com/web/about/security/intelligence/acl-logging.html
Question 3
Explanation
If you use the “debug ip packet” command on a production router, you can bring it down since it generates an output for every packet and the output can be extensive. The best way to limit the output of debug ip packet is to create an access-list that linked to the debug. Only packets that match the access-list criteria will be subject to debug ip packet. For example, this is how to monitor traffic from 1.1.1.1 to 2.2.2.2
| access-list 100 permit ip 1.1.1.1 2.2.2.2 debug ip packet 100 |
Note: The “debug ip packet” command is used to monitor packets that are processed by the routers routing engine and are not fast switched.
Question 4
Question 5
Question 6
Explanation
+ The question asks to “always” block traffic (every week) so we must use keyword “periodic”.
+ Traffic should be blocked to 11:59 PM, which means 23:59
Note: The time is specified in 24-hour time (hh:mm), where the hours range from 0 to 23 and the minutes range from 0 to 59
Only answer B satisfies these two requirements so it is the best answer. In fact, all the above answers are not correct as the access-list should deny web traffic, not allow them as shown in the answers.
Question 7
Question 8
Question 9
Explanation
The established keyword is only applicable to TCP access list entries to match TCP segments that have the ACK and/or RST control bit set (regardless of the source and destination ports), which assumes that a TCP connection has already been established in one direction only. Let’s see an example below:
 Suppose you only want to allow the hosts inside your company to telnet to an outside server but not vice versa, you can simply use an “established” access-list like this:
Suppose you only want to allow the hosts inside your company to telnet to an outside server but not vice versa, you can simply use an “established” access-list like this:
| access-list 100 permit tcp any any established access-list 101 permit tcp any any eq telnet ! interface S0/0 ip access-group 100 in ip access-group 101 out |
Note:
Suppose host A wants to start communicating with host B using TCP. Before they can send real data, a three-way handshake must be established first. Let’s see how this process takes place:
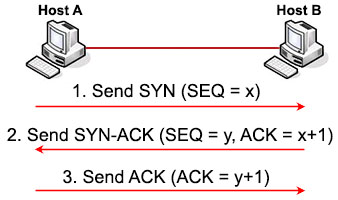
1. First host A will send a SYN message (a TCP segment with SYN flag set to 1, SYN is short for SYNchronize) to indicate it wants to setup a connection with host B. This message includes a sequence (SEQ) number for tracking purpose. This sequence number can be any 32-bit number (range from 0 to 232) so we use “x” to represent it.
2. After receiving SYN message from host A, host B replies with SYN-ACK message (some books may call it “SYN/ACK” or “SYN, ACK” message. ACK is short for ACKnowledge). This message includes a SYN sequence number and an ACK number:
+ SYN sequence number (let’s called it “y”) is a random number and does not have any relationship with Host A’s SYN SEQ number.
+ ACK number is the next number of Host A’s SYN sequence number it received, so we represent it with “x+1”. It means “I received your part. Now send me the next part (x + 1)”.
The SYN-ACK message indicates host B accepts to talk to host A (via ACK part). And ask if host A still wants to talk to it as well (via SYN part).
3. After Host A received the SYN-ACK message from host B, it sends an ACK message with ACK number “y+1” to host B. This confirms host A still wants to talk to host B.
Question 10
Explanation
Reflexive access lists provide filtering on upper-layer IP protocol sessions. They contain temporary entries that are automatically created when a new IP session begins. They are nested within extended, named IP access lists that are applied to an interface. Reflexive access lists are typically configured on border routers, which pass traffic between an internal and external network. These are often firewall routers. Reflexive access lists do not end with an implicit deny statement because they are nested within an access list and the subsequent statements need to be examined.
Reference: http://www.cisco.com/en/US/docs/ios-xml/ios/sec_data_acl/configuration/15-1s/sec-access-list-ov.html
Question 11
Explanation
The command “ipv6 traffic-filter access-list-name { in | out }” applies the access list to incoming or outgoing traffic on the interface.
Question 12
Question 13
Explanation
When the ACL logging feature is configured, the system monitors ACL flows and logs dropped packets and statistics for each flow that matches the deny conditions of the ACL entry.
The log and log-input options apply to an individual ACE and cause packets that match the ACE to be logged. The sample below illustrates the initial message and periodic updates sent by an IOS device with a default configuration using the log ACE option.
*May 1 22:12:13.243: %SEC-6-IPACCESSLOGP: list ACL-IPv4-E0/0-IN permitted tcp 192.168.1.3(1024) -> 192.168.2.1(22), 1 packet
Reference: https://www.cisco.com/c/en/us/about/security-center/access-control-list-logging.html
From the example above we can see when an ACL drops a packet, it generates a level 6 Syslog (%SEC-6-)



I have booked the 300-101 exam next week. I have purchased the information here. I hope that I can pass the exam next week. h tt p:// 6.gg/dA kbs
Anonymous. Please send me the information to solokinin @ gmail . com
h tt
(The dump here is real and effective, and the pass rate is over 90%.)
p:/ /kks.me/aK2La
Where do I get the questions w/ answers for this?
Where can you see the questions?
please, anyone tell me “question 6”
I don’t think Answer: B.
B. time-range SATSUN periodic Saturday Sunday 1:00 to 23:59
access-list 102 permit tcp any any eq 80 time-range SATSUN
access-list 102 permit tcp any any eq 443 time-range SATSUN
interface Vlan 303
ip address 10.9.5.3 255.255.255.0
ip access-group 102 in
⇒not permit but deny. why permit ?
W ww.cci
edumps.xyz?utm_source=bbs&utm_medium=bbs
I just passed the CCIE exam last week. I bought the topic here. The topic is true and effective. I have practiced most of the exam questions, but you have to remember the answer. You can’t just remember it. The options, I have encountered several questions in it, the options for the correct answer have been changed.
h ttp :
//j.mp/2Pxd7Ht
The latest question bank, the most complete information, or the teacher of online guidance.
Please send the pdf with questions to archerhitman AT mail . ru
JUST 20 $, TO GUARANTEE your Success.
CCNA R&S
200-125 CCNA = 565 Q&As DUMPs + LABs
100-105 ICND1 = 347 Q&As DUMPs + LABs
200-105 ICND2 = 268 Q&As DUMPs + LABs
CCNP R&S
ROUTE = 768 Q&As DUMPS + LABs
SWITCH = 287 Q&As DUMPs + LABs
TSHOOT = 180 Q&As DUMPs + Tickets
CCIE R&S
400-101 WRITTEN = 114 Q&As DUMPS
Get at BELOW Link
Remove SPACES:
go o . g l /FkMoqt
I have the latest Dump I require the latest VCE. Who has the VCE but not the Dump?
Sommerseller at Gmail dot com
please send latest dump- email {email not allowed}
please send latest dump- email jun_ieccomputers at yahoo dot com
What happened to questions 7 & 8?
Hi,
I am new for 9tut ccnp.What can I do for get the questions?
Hi gus.
Today i pass CCNP Router(300-101) Exam with 900+ Marks.
I have a valid dumps. If any one required email ” ccnpvaliddumps @ hotmail dot com
320 Q only.
Any Cisco Certification could be achieved if you have proper training. I would recommend you to join SPOTO and have their advanced training sessions.
i pass yesterday ,anything you want, you can find me theodosits @ hotmail .com without the blanks
Hi,
Please share CCNP (Route) dumps.
My email : dbrahma@gmail
Hi Guys
those who passed their exam, can you please share your study material??
can someone please email ccnp route dumps? my email boyapativuf14056@gmail
you guys can text me for sharing dumps: ballking242@ gmail . com
Can someone email me the latest ccnp route dumps. my email is {email not allowed}
Can someone email me the latest ccnp route dumps. my email is doncasta8@ yahoo .com
hi guys,
Can anyone please send the latest dumps on {email not allowed}
Thanks in advance
hi guys,
can anyone please send me the latest dumps for ICDN2 on {email not allowed}
Hi Guys. If you want to download freedump 300-101 go in my link
htt ps: //w ww.yout ube.co m/wa tch?v=8YAlL G9FYlo
Hi guys,
Can anyone tell me if 9tut dumps are still good or they are outdated?
Route dump please mavsm3388(a)gmail.com
Guys please share route dumps on payal . sharma86 (at) gmail . com
Can someone email me the latest ccnp route dumps? My email is renee.help (at) gmail dot com
who needs updated dump for ROUTE can contact me: cisco4career @ gmail . com
Good luck to all!
hi all good day, I’m chasing the CCNP route exam. I hope to get it before the migration. Please share with me the latest dumps for this exam in the email below. I really appreciate if you will include the VCE file for this thank you.
remove: S P A C E and replace 0 (zero) to o (ohw)
cj clds_cj @ yah00.c0m
q9
whats the difference between c and d?
why is acl 149 right?
standard acl are from 1-to 99
does anyone need a gns3 server with cisco l3 and l2 components with power? i run a server @home.. i can create an rdp account.
mail: mail2recep at gmai dot com
Hi Guys,
Please share CCNP (Route) valid dumps.
email: {email not allowed}
Tnx
@el recepo
Q9 – your are filtering on a port number and that is why extended acl is needed
Hi Guys
Is there anyone who wrote recently?