Point to Point Protocol (PPP) Tutorial
Note: The Point-to-Point Protocol is not a topic in CCNA 200-301 so if you are preparing for this exam you can ignore this tutorial.
Point-to-Point Protocol (PPP) is an open standard protocol that is mostly used to provide connections over point-to-point serial links. The main purpose of PPP is to transport Layer 3 packets over a Data Link layer point-to-point link. PPP can be configured on:
+ Asynchronous serial connection like Plain old telephone service (POTS) dial-up
+ Synchronous serial connection like Integrated Services for Digital Network (ISDN) or point-to-point leased lines.
PPP consists of two sub-protocols:
+ Link Control Protocol (LCP): set up and negotiate control options on the Data Link Layer (OSI Layer 2). After finishing setting up the link, it uses NCP.
+ Network control Protocol (NCP): negotiate optional configuration parameters and facilitate for the Network Layer (OSI Layer 3). In other words, it makes sure IP and other protocols can operate correctly on PPP link

Establish a PPP session
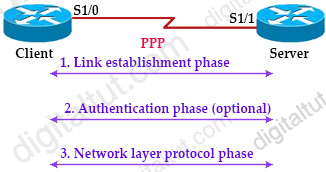
Before a PPP connection is established, the link must go through three phases of session establishment:
1. Link establishment phase: In this phase, each PPP device sends LCP packets to configure and test the data link
2. Authentication phase (optional): If authentication is enabled, either PAP or CHAP will be used. PAP and CHAP are two authentication protocols used in PPP
3. Network layer protocol phase: PPP sends NCP packets to choose and configure Network Layer protocol (OSI Layer 3) to be encapsulated and sent over the PPP data link
| Note: The default serial encapsulation on Cisco routers is HDLC so if you want to use PPP you have to configure it. Unlike HDLC which is a Cisco proprietary protocol, PPP is an open standard protocol so you should use it to connect a Cisco router to a non-Cisco router |
PPP Authentication Methods
In this part we will learn more about two authentication methods used in Authentication Phase of PPP.
PPP has two built-in security mechanisms which are Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP).
Password Authentication Protocol (PAP) is a very simple authentication protocol. The client who wants to access a server sends its username and password in clear text. The server checks the validity of the username and password and either accepts or denies connection. This is called two-way handshake. In PAP two-way handshake process, the username and password are sent in the first message.
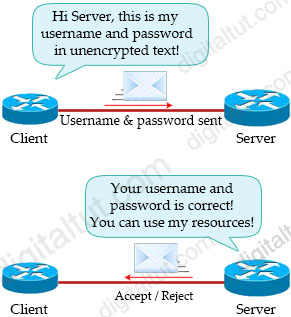 PAP two-way handshake
PAP two-way handshake
For those systems that require greater security, PAP is not enough as a third party with access to the link can easily pick up the password and access the system resources. In this case CHAP can save our life!
Challenge Handshake Authentication Protocol (CHAP) is an PPP authentication protocol which is far more secure than PAP. Let’s see how CHAP three-way handshake works:
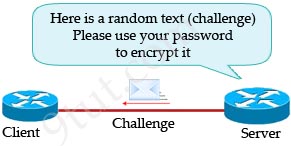
With CHAP, the protocol begins (after the LCP phase is complete) with a random text (called a challenge) sent from the Server, which asks the Client to authenticate.
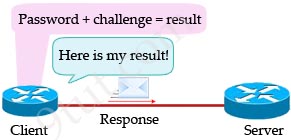
After receiving the challenge, the Client uses its password to perform a one-way hash algorithm (MD5) to encrypt the random text received from the server. The result is then sent back to the Server. Therefore even if someone can capture the messages between client and server, he cannot know what the password is.
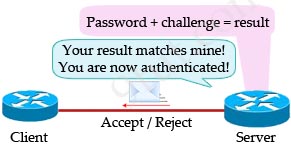
At the Server side, the same algorithm is used to generate its own result. If the two results match, the passwords must match too.
The main difference between PAP and CHAP is PAP sends username and password in clear text to the server while CHAP does not. Notice that in CHAP authentication process, the password itself is never sent across the link.
Another difference between these two authentication protocols is PAP performs authentication at the initial link establishment only while CHAP performs authentication at the initial link establishment and periodically after that. The challenge text is random and unique so the “result” is also unique from time to time. This prevents playback attack (in which a hacker tries to copy the “result” text sent from Client to reuse).
| CHAP Summary: + CHAP is defined as a one-way authentication method. However, you use CHAP in both directions to create a two-way authentication. Hence, with two-way CHAP, a separate three-way handshake is initiated by each side. + In the Cisco CHAP implementation, by default, the called party must authenticate the calling party. The protocol begins with a random text (called a challenge) sent from the Server, which asks the Client to authenticate |
In the next part we will learn how to configure PAP and CHAP for PPP.


